Create a Classic Load Balancer with an HTTPS listener
A load balancer takes requests from clients and distributes them across the EC2 instances that are registered with the load balancer.
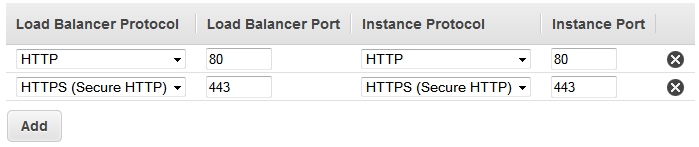
You can create a load balancer that listens on both the HTTP (80) and HTTPS (443) ports. If you specify that the HTTPS listener sends requests to the instances on port 80, the load balancer terminates the requests and communication from the load balancer to the instances is not encrypted. If the HTTPS listener sends requests to the instances on port 443, communication from the load balancer to the instances is encrypted.
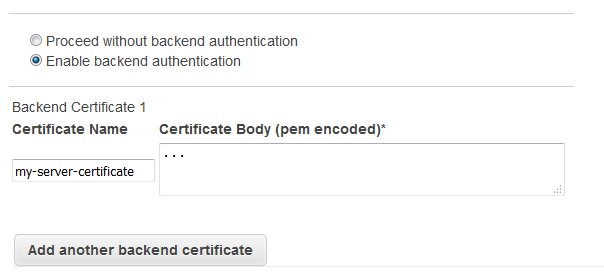
If your load balancer uses an encrypted connection to communicate with the instances, you can optionally enable authentication of the instances. This ensures that the load balancer communicates with an instance only if its public key matches the key that you specified to the load balancer for this purpose.
For information about adding an HTTPS listener to an existing load balancer, see Configure an HTTPS listener for your Classic Load Balancer.
Contents
Prerequisites
Before you get started, be sure that you've met the following prerequisites:
-
Complete the steps in Prepare your VPC and EC2 instances.
-
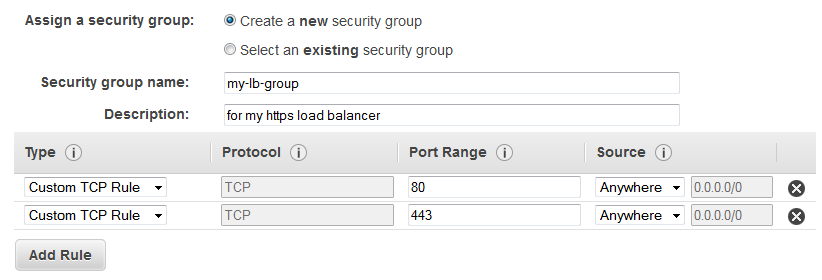
Launch the EC2 instances that you plan to register with your load balancer. The security groups for these instances must allow traffic from the load balancer.
-
The EC2 instances must respond to the target of the health check with an HTTP status code 200. For more information, see Configure health checks for your Classic Load Balancer.
-
If you plan to enable the keep-alive option on your EC2 instances, we recommend that you set the keep-alive settings to at least the idle timeout settings of your load balancer. If you want to ensure that the load balancer is responsible for closing the connections to your instance, make sure that the value set on your instance for the keep-alive time is greater than the idle timeout setting on your load balancer. For more information, see Configure the idle connection timeout for your Classic Load Balancer.
-
If you create a secure listener, you must deploy an SSL server certificate on your load balancer. The load balancer uses the certificate to terminate and then decrypt requests before sending them to the instances. If you don't have an SSL certificate, you can create one. For more information, see SSL/TLS certificates for Classic Load Balancers.
Create an HTTPS/SSL load balancer using the AWS Management Console
Create an HTTPS/SSL load balancer using the AWS CLI
Use the following instructions to create an HTTPS/SSL load balancer using the AWS CLI.
Tasks
Step 1: Configure listeners
A listener is a process that checks for connection requests. It is configured with a protocol and a port for front-end (client to load balancer) connections and a protocol and port for back-end (load balancer to instance) connections. For information about the ports, protocols, and listener configurations supported by Elastic Load Balancing, see Listeners for your Classic Load Balancer.
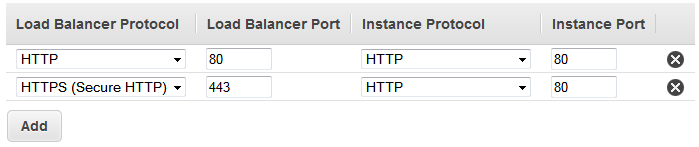
In this example, you configure two listeners for your load balancer by specifying the ports and protocols to use for front-end and back-end connections. The first listener accepts HTTP requests on port 80 and sends the requests to the instances on port 80 using HTTP. The second listener accepts HTTPS requests on port 443 and sends requests to instances using HTTP on port 80.
Because the second listener uses HTTPS for the front-end connection, you must deploy an SSL sever certificate on your load balancer. The load balancer uses the certificate to terminate and then decrypt requests before sending them to the instances.
To configure listeners for your load balancer
-
Get the Amazon Resource Name (ARN) of the SSL certificate. For example:
ACM
arn:aws:acm:region:123456789012:certificate/12345678-1234-1234-1234-123456789012IAM
arn:aws:iam::123456789012:server-certificate/my-server-certificate -
Use the following create-load-balancer command to configure the load balancer with the two listeners:
aws elb create-load-balancer --load-balancer-namemy-load-balancer--listeners "Protocol=http,LoadBalancerPort=80,InstanceProtocol=http,InstancePort=80" "Protocol=https,LoadBalancerPort=443,InstanceProtocol=http,InstancePort=80,SSLCertificateId="ARN" --availability-zonesus-west-2aThe following is an example response:
{ "DNSName": "my-loadbalancer-012345678.us-west-2.elb.amazonaws.com" } -
(Optional) Use the following describe-load-balancers command to view the details of your load balancer:
aws elb describe-load-balancers --load-balancer-namemy-load-balancer
Step 2: Configure the SSL security policy
You can select one of the predefined security policies, or you can create your
own custom security policy. Otherwise, Elastic Load Balancing configures your load balancer with
the default predefined security policy, ELBSecurityPolicy-2016-08. We
recommend that you use the default security policy. For more information about
security policies, see SSL negotiation configurations for
Classic Load Balancers.
To verify that your load balancer is associated with the default security policy
Use the following describe-load-balancers command:
aws elb describe-load-balancers --load-balancer-namemy-loadbalancer
The following is an example response. Note that ELBSecurityPolicy-2016-08
is associated with the load balancer on port 443.
{
"LoadBalancerDescriptions": [
{
...
"ListenerDescriptions": [
{
"Listener": {
"InstancePort": 80,
"SSLCertificateId": "ARN",
"LoadBalancerPort": 443,
"Protocol": "HTTPS",
"InstanceProtocol": "HTTP"
},
"PolicyNames": [
"ELBSecurityPolicy-2016-08"
]
},
{
"Listener": {
"InstancePort": 80,
"LoadBalancerPort": 80,
"Protocol": "HTTP",
"InstanceProtocol": "HTTP"
},
"PolicyNames": []
}
],
...
}
]
}If you prefer, you can configure the SSL security policy for your load balancer instead of using the default security policy.
(Optional) to use a predefined SSL security policy
-
Use the following describe-load-balancer-policies command to list the names of the predefined security policies:
aws elb describe-load-balancer-policiesFor information about the configuration for the predefined security policies, see Predefined SSL security policies.
-
Use the following create-load-balancer-policy command to create an SSL negotiation policy using one of the predefined security policies that you described in the previous step:
aws elb create-load-balancer-policy --load-balancer-namemy-loadbalancer--policy-namemy-SSLNegotiation-policy--policy-type-name SSLNegotiationPolicyType --policy-attributes AttributeName=Reference-Security-Policy,AttributeValue=predefined-policy -
(Optional) Use the following describe-load-balancer-policies command to verify that the policy is created:
aws elb describe-load-balancer-policies --load-balancer-namemy-loadbalancer--policy-namemy-SSLNegotiation-policyThe response includes the description of the policy.
-
Use the following set-load-balancer-policies-of-listener command to enable the policy on load balancer port 443:
aws elb set-load-balancer-policies-of-listener --load-balancer-namemy-loadbalancer--load-balancer-port 443 --policy-namesmy-SSLNegotiation-policyNote
The
set-load-balancer-policies-of-listenercommand replaces the current set of policies for the specified load balancer port with the specified set of policies. The--policy-nameslist must include all policies to be enabled. If you omit a policy that is currently enabled, it is disabled. -
(Optional) Use the following describe-load-balancers command to verify that the policy is enabled:
aws elb describe-load-balancers --load-balancer-namemy-loadbalancerThe following is an example response showing that the policy is enabled on port 443.
{ "LoadBalancerDescriptions": [ { .... "ListenerDescriptions": [ { "Listener": { "InstancePort": 80, "SSLCertificateId": "ARN", "LoadBalancerPort": 443, "Protocol": "HTTPS", "InstanceProtocol": "HTTP" }, "PolicyNames": [ "my-SSLNegotiation-policy" ] }, { "Listener": { "InstancePort": 80, "LoadBalancerPort": 80, "Protocol": "HTTP", "InstanceProtocol": "HTTP" }, "PolicyNames": [] } ], ... } ] }
When you create a custom security policy, you must enable at least one
protocol and one cipher. The DSA and RSA ciphers are specific to the signing
algorithm and are used to create the SSL certificate. If you already have your
SSL certificate, make sure to enable the cipher that was used to create your
certificate. The name of your custom policy must not begin with
ELBSecurityPolicy- or ELBSample-, as these
prefixes are reserved for the names of the predefined security policies.
(Optional) to use a custom SSL security policy
-
Use the create-load-balancer-policy command to create an SSL negotiation policy using a custom security policy. For example:
aws elb create-load-balancer-policy --load-balancer-namemy-loadbalancer--policy-namemy-SSLNegotiation-policy--policy-type-name SSLNegotiationPolicyType --policy-attributes AttributeName=Protocol-TLSv1.2,AttributeValue=true AttributeName=Protocol-TLSv1.1,AttributeValue=true AttributeName=DHE-RSA-AES256-SHA256,AttributeValue=true AttributeName=Server-Defined-Cipher-Order,AttributeValue=true -
(Optional) Use the following describe-load-balancer-policies command to verify that the policy is created:
aws elb describe-load-balancer-policies --load-balancer-namemy-loadbalancer--policy-namemy-SSLNegotiation-policyThe response includes the description of the policy.
-
Use the following set-load-balancer-policies-of-listener command to enable the policy on load balancer port 443:
aws elb set-load-balancer-policies-of-listener --load-balancer-namemy-loadbalancer--load-balancer-port 443 --policy-namesmy-SSLNegotiation-policyNote
The
set-load-balancer-policies-of-listenercommand replaces the current set of policies for the specified load balancer port with the specified set of policies. The--policy-nameslist must include all policies to be enabled. If you omit a policy that is currently enabled, it is disabled. -
(Optional) Use the following describe-load-balancers command to verify that the policy is enabled:
aws elb describe-load-balancers --load-balancer-namemy-loadbalancerThe following is an example response showing that the policy is enabled on port 443.
{ "LoadBalancerDescriptions": [ { .... "ListenerDescriptions": [ { "Listener": { "InstancePort": 80, "SSLCertificateId": "ARN", "LoadBalancerPort": 443, "Protocol": "HTTPS", "InstanceProtocol": "HTTP" }, "PolicyNames": [ "my-SSLNegotiation-policy" ] }, { "Listener": { "InstancePort": 80, "LoadBalancerPort": 80, "Protocol": "HTTP", "InstanceProtocol": "HTTP" }, "PolicyNames": [] } ], ... } ] }
Step 3: Configure back-end instance authentication (optional)
If you set up HTTPS/SSL on the back-end connection, you can optionally set up authentication of your instances.
When you set up back-end instance authentication, you create a public key policy. Next, you use this public key policy to create a back-end instance authentication policy. Finally, you set the back-end instance authentication policy with the instance port for the HTTPS protocol.
The load balancer communicates with an instance only if the public key that the instance presents to the load balancer matches a public key in the authentication policy for your load balancer.
To configure back-end instance authentication
-
Use the following command to retrieve the public key:
openssl x509 -inyour X509 certificate PublicKey-pubkey -noout -
Use the following create-load-balancer-policy command to create a public key policy:
aws elb create-load-balancer-policy --load-balancer-namemy-loadbalancer--policy-namemy-PublicKey-policy\ --policy-type-name PublicKeyPolicyType --policy-attributes AttributeName=PublicKey,AttributeValue=MIICiTCCAfICCQD6m7oRw0uXOjANBgkqhkiG9w 0BAQUFADCBiDELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAldBMRAwDgYDVQQHEwdTZ WF0dGxlMQ8wDQYDVQQKEwZBbWF6b24xFDASBgNVBAsTC0lBTSBDb25zb2xlMRIw EAYDVQQDEwlUZXN0Q2lsYWMxHzAdBgkqhkiG9w0BCQEWEG5vb25lQGFtYXpvbi5 jb20wHhcNMTEwNDI1MjA0NTIxWhcNMTIwNDI0MjA0NTIxWjCBiDELMAkGA1UEBh MCVVMxCzAJBgNVBAgTAldBMRAwDgYDVQQHEwdTZWF0dGxlMQ8wDQYDVQQKEwZBb WF6b24xFDASBgNVBAsTC0lBTSBDb25zb2xlMRIwEAYDVQQDEwlUZXN0Q2lsYWMx HzAdBgkqhkiG9w0BCQEWEG5vb25lQGFtYXpvbi5jb20wgZ8wDQYJKoZIhvcNAQE BBQADgY0AMIGJAoGBAMaK0dn+a4GmWIWJ21uUSfwfEvySWtC2XADZ4nB+BLYgVI k60CpiwsZ3G93vUEIO3IyNoH/f0wYK8m9TrDHudUZg3qX4waLG5M43q7Wgc/MbQ ITxOUSQv7c7ugFFDzQGBzZswY6786m86gpEIbb3OhjZnzcvQAaRHhdlQWIMm2nr AgMBAAEwDQYJKoZIhvcNAQEFBQADgYEAtCu4nUhVVxYUntneD9+h8Mg9q6q+auN KyExzyLwaxlAoo7TJHidbtS4J5iNmZgXL0FkbFFBjvSfpJIlJ00zbhNYS5f6Guo EDmFJl0ZxBHjJnyp378OD8uTs7fLvjx79LjSTbNYiytVbZPQUQ5Yaxu2jXnimvw 3rrszlaEXAMPLE=Note
To specify a public key value for
--policy-attributes, remove the first and last lines of the public key (the line containing "-----BEGIN PUBLIC KEY-----" and the line containing "-----END PUBLIC KEY-----"). The AWS CLI does not accept white space characters in--policy-attributes. -
Use the following create-load-balancer-policy command to create a back-end instance authentication policy using
my-PublicKey-policy.aws elb create-load-balancer-policy --load-balancer-namemy-loadbalancer--policy-namemy-authentication-policy--policy-type-name BackendServerAuthenticationPolicyType --policy-attributes AttributeName=PublicKeyPolicyName,AttributeValue=my-PublicKey-policyYou can optionally use multiple public key policies. The load balancer tries all the keys, one at a time. If the public key presented by an instance matches one of these public keys, the instance is authenticated.
-
Use the following set-load-balancer-policies-for-backend-server command to set
my-authentication-policyto the instance port for HTTPS. In this example, the instance port is port 443.aws elb set-load-balancer-policies-for-backend-server --load-balancer-namemy-loadbalancer--instance-port 443 --policy-namesmy-authentication-policy -
(Optional) Use the following describe-load-balancer-policies command to list all the policies for your load balancer:
aws elb describe-load-balancer-policies --load-balancer-namemy-loadbalancer -
(Optional) Use the following describe-load-balancer-policies command to view details of the policy:
aws elb describe-load-balancer-policies --load-balancer-namemy-loadbalancer--policy-namesmy-authentication-policy
Step 4: Configure health checks (optional)
Elastic Load Balancing regularly checks the health of each registered EC2 instance based on the health checks that you configured. If Elastic Load Balancing finds an unhealthy instance, it stops sending traffic to the instance and routes traffic to the healthy instances. For more information, see Configure health checks for your Classic Load Balancer.
When you create your load balancer, Elastic Load Balancing uses default settings for the health checks. If you prefer, you can change the health check configuration for your load balancer instead of using the default settings.
To configure the health checks for your instances
Use the following configure-health-check command:
aws elb configure-health-check --load-balancer-namemy-loadbalancer--health-check Target=HTTP:80/ping,Interval=30,UnhealthyThreshold=2,HealthyThreshold=2,Timeout=3
The following is an example response:
{
"HealthCheck": {
"HealthyThreshold": 2,
"Interval": 30,
"Target": "HTTP:80/ping",
"Timeout": 3,
"UnhealthyThreshold": 2
}
}Step 5: Register EC2 instances
After you create your load balancer, you must register your EC2 instances with the load balancer. You can select EC2 instances from a single Availability Zone or multiple Availability Zones within the same Region as the load balancer. For more information, see Registered instances for your Classic Load Balancer.
Use the register-instances-with-load-balancer command as follows:
aws elb register-instances-with-load-balancer --load-balancer-namemy-loadbalancer--instancesi-4f8cf126 i-0bb7ca62
The following is an example response:
{
"Instances": [
{
"InstanceId": "i-4f8cf126"
},
{
"InstanceId": "i-0bb7ca62"
}
]
}Step 6: Verify the instances
Your load balancer is usable as soon as any one of your registered instances
is in the InService state.
To check the state of your newly registered EC2 instances, use the following describe-instance-health command:
aws elb describe-instance-health --load-balancer-namemy-loadbalancer--instancesi-4f8cf126 i-0bb7ca62
The following is an example response:
{
"InstanceStates": [
{
"InstanceId": "i-4f8cf126",
"ReasonCode": "N/A",
"State": "InService",
"Description": "N/A"
},
{
"InstanceId": "i-0bb7ca62",
"ReasonCode": "Instance",
"State": "OutOfService",
"Description": "Instance registration is still in progress"
}
]
}If the State field for an instance is OutOfService,
it's probably because your instances are still registering. For more
information, see Troubleshoot a Classic Load Balancer: Instance registration.
After the state of at least one of your instances is InService,
you can test your load balancer. To test your load balancer, copy the DNS name
of the load balancer and paste it into the address field of an
internet-connected web browser. If your load balancer is working, you see the
default page of your HTTP server.
Step 7: Delete your load balancer (optional)
Deleting a the load balancer automatically de-registers its associated EC2 instances. As soon as the load balancer is deleted, you stop incurring charges for that load balancer. However, the EC2 instances continue run and you continue to incur charges.
To delete your load balancer, use the following delete-load-balancer command:
aws elb delete-load-balancer --load-balancer-namemy-loadbalancer
To stop your EC2 instances, use the stop-instances command. To terminate your EC2 instances, use the terminate-instances command.