Conditions with multiple context keys or values
You can use the Condition element of a policy to test multiple context keys or
multiple values for a single context key in a request. When you make a request to AWS, either
programmatically or through the AWS Management Console, your request includes information about your
principal, operation, tags, and more. You can use context keys to test the values of the
matching context keys in the request, with the context keys specified in the policy condition.
To learn about information and data included in a request, see The request context.
Topics
Evaluation logic for multiple context keys or values
A Condition element can contain multiple condition operators, and each
condition operator can contain multiple context key-value pairs. Most context keys support
using multiple values, unless otherwise specified.
-
If your policy statement has multiple condition operators, the condition operators are evaluated using a logical
AND. -
If your policy statement has multiple context keys attached to a single condition operator, the context keys are evaluated using a logical
AND. -
If a single condition operator includes multiple values for a context key, those values are evaluated using a logical
OR. -
If a single negated matching condition operator includes multiple values for a context key, those values are evaluated using a logical
NOR.
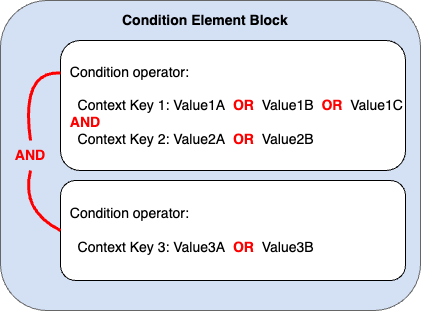
All context keys in a condition element block must resolve to true to invoke the desired
Allow or Deny effect. The following figure illustrates the
evaluation logic for a condition with multiple condition operators and context key-value
pairs.
For example, the following S3 bucket policy illustrates how the previous figure is
represented in a policy. The condition block includes condition operators
StringEquals and ArnLike, and context keys
aws:PrincipalTag and aws:PrincipalArn. To invoke the desired
Allow or Deny effect, all context keys in the condition block must
resolve to true. The user making the request must have both principal tag keys,
department and role, that include one of the tag
key values specified in the policy. Also, the principal ARN of the user making the request
must match one of the aws:PrincipalArn values specified in the policy to be
evaluated as true.
The following table shows how AWS evaluates this policy based on the condition key values in your request.
| Policy Condition | Request Context | Result |
|---|---|---|
|
|
Match |
|
|
No match |
|
|
No match |
|
No |
No match |
|
No |
No match |
Evaluation logic for negated matching condition operators
Some condition
operators, such as StringNotEquals or ArnNotLike, use
negated matching to compare the context key-value pairs in your policy against the context
key-value pairs in a request. When multiple values are specified for a single context key in a
policy with negated matching condition operators, the effective permissions work like a
logical NOR. In negated matching, a logical NOR or NOT
OR returns true only if all values evaluate to false.
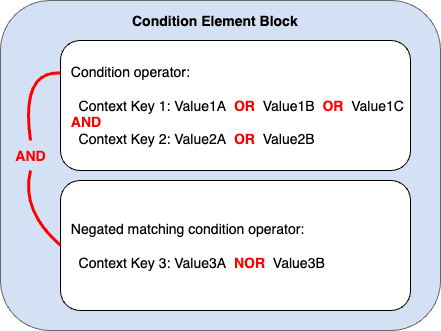
The following figure illustrates the evaluation logic for a condition with multiple condition operators and context key-value pairs. The figure includes a negated matching condition operator for context key 3.
For example, the following S3 bucket policy illustrates how the previous figure is
represented in a policy. The condition block includes condition operators
StringEquals and ArnNotLike, and context keys
aws:PrincipalTag and aws:PrincipalArn. To invoke the desired
Allow or Deny effect, all context keys in the condition block must
resolve to true. The user making the request must have both principal tag keys,
department and role, that include one of the tag
key values specified in the policy. Since the ArnNotLike condition operator uses
negated matching, the principal ARN of the user making the request must not match any of the
aws:PrincipalArn values specified in the policy to be evaluated as true.
The following table shows how AWS evaluates this policy based on the condition key values in your request.
| Policy Condition | Request Context | Result |
|---|---|---|
|
|
Match |
|
|
No match |
|
|
No match |
|
> No |
No match |
|
No |
No match |