Adding advanced security to a user pool
After you create your user pool, you have access to Advanced security on the navigation bar in the Amazon Cognito console. You can turn the user pool advanced security features on, and customize the actions that are taken in response to different risks. Or you can use audit mode to gather metrics on detected risks without applying any security mitigations. In audit mode, the advanced security features publish metrics to Amazon CloudWatch. You can see advanced security metrics after Amazon Cognito generates its first advanced security event. See Viewing advanced security metrics.
Advanced security features include compromised credentials detection and adaptive authentication.
- Compromised credentials
-
Users reuse passwords for multiple user accounts. The compromised credentials feature of Amazon Cognito compiles data from public leaks of user names and passwords, and compares your users' credentials to lists of leaked credentials. Compromised credentials detection also checks for commonly-guessed passwords.
You can choose the user actions that prompt a check for compromised credentials, and the action that you want Amazon Cognito to take in response. For sign-in, sign-up, and password-change events, Amazon Cognito can Block sign-in, or Allow sign-in. In both cases, Amazon Cognito generates a user activity log, where you can find more information about the event.
- Adaptive authentication
-
Amazon Cognito can review location and device information from your users' sign-in requests and apply an automatic response to secure the user accounts in your user pool against suspicious activity.
When you activate advanced security, Amazon Cognito assigns a risk score to user activity. You can assign an automatic response to suspicious activity: you can Require MFA, Block sign-in, or just log the activity details and risk score. You can also automatically send email messages that notify your user of the suspicious activity so that they can reset their password or take other self-guided actions.
- Access token customization
-
When you activate advanced security features, you can configure your user pool to accept responses to a version 2 Lambda trigger event. With version 2, you can customize scopes and other claims in access tokens. This increases your ability to create flexible authorization outcomes when your users authenticate. For more information, see Customizing the access token.
Topics
Considerations and limitations
-
Additional pricing applies for Amazon Cognito advanced security features. See the Amazon Cognito pricing page
. -
Amazon Cognito supports adaptive authentication and compromised-credentials detection with the following standard authentication flows:
USER_PASSWORD_AUTH,ADMIN_USER_PASSWORD_AUTH, andUSER_SRP_AUTH. You can't use advanced security with aCUSTOM_AUTHflow and Custom authentication challenge Lambda triggers, or with federated sign-in. -
With Amazon Cognito advanced security features in Full function mode, you can create IP address Always block and Always allow exceptions. A session from an IP address on the Always block exception list isn't assigned a risk level by adaptive authentication, and can't sign in to your user pool.
-
Blocked requests from IP addresses on an Always block exception list in your user pool contribute to the request rate quotas for your user pools. Amazon Cognito advanced security features don't prevent distributed denial of service (DDoS) attacks. To implement defenses against volumetric attacks in your user pools, add AWS WAF web ACLs. For more information, see Associating an AWS WAF web ACL with a user pool.
-
Client credentials grants are intended for machine-to-machine (M2M) authorization with no connection to user accounts. Advanced security features only monitor user accounts and passwords in your user pool. To implement security features with your M2M activity, consider the capabilities of AWS WAF for monitoring request rates and content. For more information, see Associating an AWS WAF web ACL with a user pool.
Prerequisites
Before you begin, you need the following:
-
A user pool with an app client. For more information, see Getting started with user pools.
-
Set multi-factor authentication (MFA) to Optional in the Amazon Cognito console to use the risk-based adaptive authentication feature. For more information, see Adding MFA to a user pool.
-
If you're using email notifications, go to the Amazon SES console
to configure and verify an email address or domain to use with your email notifications. For more information about Amazon SES, see Verifying Identities in Amazon SES.
Configuring advanced security features
You can configure Amazon Cognito advanced security features in the AWS Management Console.
To configure advanced security for a user pool
-
Go to the Amazon Cognito console
. If prompted, enter your AWS credentials. -
Choose User Pools.
-
Choose an existing user pool from the list, or create a user pool.
-
Choose the App integration tab. Locate Advanced security and choose Enable. If you enabled advanced security earlier, choose Edit.
-
Select Full function to configure advanced security responses to compromised credentials and adaptive authentication. Select Audit only to gather information and send user pool data to CloudWatch. Advanced security pricing applies in both Audit only and Full function mode. For more information, see Amazon Cognito Pricing
. We recommend keeping the advanced security features in audit mode for two weeks before enabling actions. During this time, Amazon Cognito can learn the usage patterns of your app users.
-
If you selected Audit only, choose Save changes. If you selected Full function:
-
Select whether you will take Custom action or use or Cognito defaults to respond to suspected Compromised credentials. Cognito defaults are:
-
Detect compromised credentials on Sign-in, Sign-up, and Password change.
-
Respond to compromised credentials with the action Block sign-in.
-
-
If you selected Custom actions for Compromised credentials, choose the user pool actions that Amazon Cognito will use for Event detection and the Compromised credentials responses that you would like Amazon Cognito to take. You can Block sign-in or Allow sign-in with suspected compromised credentials.
-
Choose how to respond to malicious sign-in attempts under Adaptive authentication. Select whether you will take Custom action or use or Cognito defaults to respond to suspected malicious activity. When you select Cognito defaults, Amazon Cognito blocks sign-in at all risk levels and does not notify the user.
-
If you selected Custom actions for Adaptive authentication, choose the Automatic risk response actions that Amazon Cognito will take in response to detected risks based on severity level. When you assign a response to a level of risk, you can't assign a less-restrictive response to a higher level of risk. You can assign the following responses to risk levels:
-
Allow sign-in - Take no preventative action.
-
Optional MFA - If the user has MFA configured, Amazon Cognito will always require the user to provide an additional SMS or time-based one-time password (TOTP) factor when they sign in. If the user does not have MFA configured, they can continue signing in normally.
-
Require MFA - If the user has MFA configured, Amazon Cognito will always require the user to provide an additional SMS or TOTP factor when they sign in. If the user does not have MFA configured, Amazon Cognito will prompt them to set up MFA. Before you automatically require MFA for your users, configure a mechanism in your app to capture phone numbers for SMS MFA, or to register authenticator apps for TOTP MFA.
-
Block sign-in - Prevent the user from signing in.
-
Notify user - Send an email message to the user with information about the risk that Amazon Cognito detected and the response you have taken. You can customize email message templates for the messages you send.
-
-
-
If you chose Notify user in the previous step, you can customize your email delivery settings and email message templates for adaptive authentication.
-
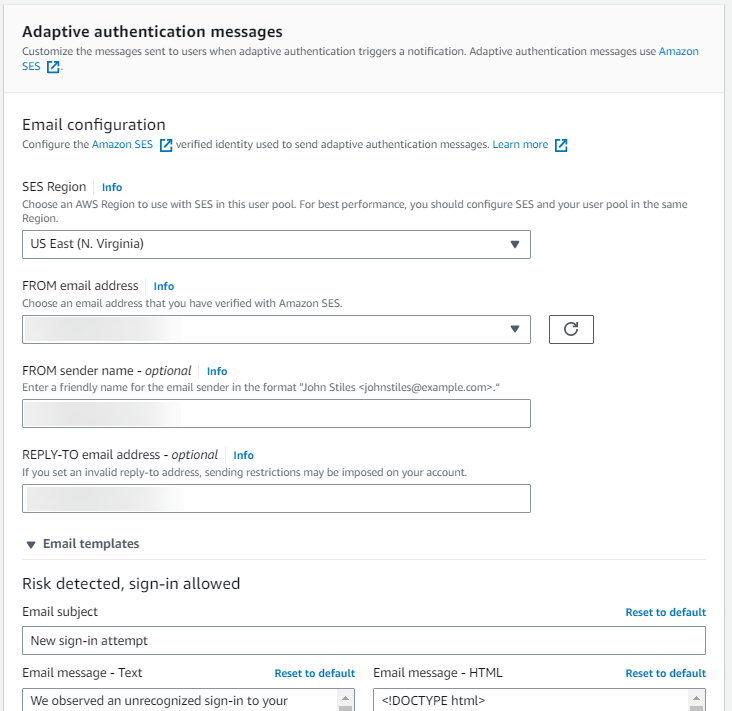
Under Email configuration, choose the SES Region, FROM email address, FROM sender name, and REPLY-TO email address that you want to use with adaptive authentication. For more information about integrating your user pool email messages with Amazon Simple Email Service, see Email settings for Amazon Cognito user pools.
-
Expand Email templates to customize adaptive authentication notifications with both HTML and plaintext versions of email messages. To learn more about email message templates, see Message templates.
-
-
Expand IP address exceptions to create an Always-allow or an Always-block list of IPv4 or IPv6 address ranges that will always be allowed or blocked, regardless of the advanced security risk assessment. Specify the IP address ranges in CIDR notation
(such as 192.168.100.0/24). -
Choose Save changes.