기계 번역으로 제공되는 번역입니다. 제공된 번역과 원본 영어의 내용이 상충하는 경우에는 영어 버전이 우선합니다.
추적 생성
모범 사례로 모든 AWS 리전에 적용되는 추적을 생성합니다. CloudTrail콘솔에서 트레일을 생성할 때의 기본 설정입니다. 트레일이 모든 지역에 적용되는 경우, CloudTrail 작업 중인 AWS 파티션의 모든 리전에 있는 로그 파일을 지정한 S3 버킷으로 전송합니다. 트레일을 생성하고 나면 지정한 이벤트 로깅이 AWS CloudTrail 자동으로 시작됩니다.
참고
트레일을 생성한 후 CloudTrail 로그에서 수집된 이벤트 데이터를 추가로 분석하고 이에 따라 조치를 AWS 서비스 취하도록 기타를 구성할 수 있습니다. 자세한 정보는 AWS 로그와의 서비스 통합 CloudTrail 을 참조하세요.
콘솔에서 추적 생성
다음 절차를 사용하여 작업 중인 파티션의 모든 AWS 리전 AWS 파티션에 이벤트를 기록하는 트레일을 만드십시오. 이것이 권장되는 모범 사례입니다. 단일 리전에 이벤트를 로깅하려면(권장하지 않음) AWS CLI를 사용합니다.
를 사용하여 CloudTrail 트레일을 만들려면 AWS Management Console
에 AWS Management Console 로그인하고 https://console.aws.amazon.com/cloudtrail/
에서 CloudTrail 콘솔을 엽니다. -
CloudTrail 서비스 홈 페이지, 트레일 페이지 또는 대시보드 페이지의 트레일 섹션에서 트레일 생성을 선택합니다.
-
[Create Trail] 페이지에서 [Trail name]의 경우 추적 이름을 입력합니다. 자세한 정보는 이름 지정 요구 사항을 참조하세요.
-
AWS Organizations 조직 트레일인 경우 조직 내 모든 계정에 대해 트레일을 활성화할 수 있습니다. 이 옵션을 보려면 관리 계정이나 위임된 관리자 계정의 사용자 또는 역할로 콘솔에 로그인해야 합니다. 조직 추적을 생성하려면 사용자 또는 역할에 충분한 권한이 있는지 확인합니다. 자세한 내용은 조직에 대한 추적 생성 단원을 참조하세요.
-
[스토리지 위치(Storage location)]에서 [새 S3 버킷 생성(Create new S3 bucket)]을 선택하여 버킷을 생성합니다. 버킷을 만들면 필요한 버킷 정책을 CloudTrail 만들고 적용합니다.
참고
[기존 S3 버킷 사용(Use existing S3 bucket)]을 선택한 경우 [추적 로그 버킷 이름(Trail log bucket name)]에 버킷을 지정하거나 [찾아보기(Browse)]를 선택하여 자체 계정의 버킷을 선택합니다. 다른 계정의 버킷을 사용하려면 해당 버킷의 이름을 지정해야 합니다. 버킷 정책은 쓰기 CloudTrail 권한을 부여해야 합니다. 버킷 정책의 수동 편집에 대한 자세한 내용은 에 대한 Amazon S3 버킷 정책 CloudTrail 단원을 참조하세요.
로그를 더 쉽게 찾을 수 있도록 기존 버킷에 새 폴더 (접두사라고도 함) 를 만들어 CloudTrail 로그를 저장하십시오. [접두사(Prefix)]에 접두사를 입력합니다.
-
SSE-S3 암호화 대신 SSE-KMS 암호화를 사용하여 로그 파일을 암호화하려면 Log file SSE-KMS encryption(로그 파일 SSE-KMS 암호화)에서 Enabled(사용)를 선택합니다. 기본값은 [사용(Enabled)]입니다. SSE-KMS 암호화를 사용하지 않으면 로그는 SSE-S3 암호화를 사용하여 암호화합니다. SSE-KMS 암호화에 대한 자세한 내용은 서버 측 암호화 사용 (SSE-KMS) 을 참조하십시오. AWS Key Management Service SSE-S3 암호화에 대한 자세한 내용은 Amazon S3 관리형 암호화 키(SSE-S3)로 서버 측 암호화 사용을 참조하세요.
SSE-KMS 암호화를 활성화하는 경우 신규 또는 기존 암호화를 선택합니다. AWS KMS keyAWS KMS 별칭에서 별칭을 다음과 같은 형식으로 지정합니다.
alias/MyAliasName자세한 정보는 KMS 키를 사용하도록 리소스 업데이트을 참조하세요. CloudTrail AWS KMS 다중 지역 키도 지원합니다. 다중 리전 키에 대한 자세한 내용은 AWS Key Management Service 개발자 가이드의 다중 리전 키 사용 단원을 참조하세요.참고
다른 계정에 있는 키의 ARN을 입력할 수도 있습니다. 자세한 정보는 KMS 키를 사용하도록 리소스 업데이트을 참조하세요. 키 정책은 키를 CloudTrail 사용하여 로그 파일을 암호화하고 지정한 사용자가 암호화되지 않은 형식으로 로그 파일을 읽을 수 있도록 허용해야 합니다. 키 정책의 수동 편집에 대한 자세한 내용은 CloudTrail에 대한 AWS KMS 키 정책 구성 단원을 참조하세요.
-
[추가 설정(Additional settings)]에서 다음을 구성합니다.
-
[로그 파일 검증(Log file validation)]에서 [사용(Enabled)]을 선택하여 로그 다이제스트를 S3 버킷에 전달합니다. 다이제스트 파일을 사용하여 로그 파일이 전달된 후 CloudTrail 변경되지 않았는지 확인할 수 있습니다. 자세한 정보는 CloudTrail 로그 파일 무결성 검증을 참조하세요.
-
SNS 알림 전송의 경우 로그가 버킷으로 전송될 때마다 알림을 받으려면 활성화를 선택합니다. CloudTrail 로그 파일에 여러 이벤트를 저장합니다. 모든 이벤트가 아니라 모든 로그 파일에 대해 SNS 알림이 전송됩니다. 자세한 내용은 CloudTrail에 대한 Amazon SNS 알림 구성 단원을 참조하세요.
SNS 알림을 사용하도록 설정하는 경우 [새 SNS 주제 생성(Create a new SNS topic)]에서 [신규(New)]를 선택하여 주제를 생성하거나 [기존(Existing)]을 선택하여 기존 주제를 사용합니다. 모든 리전에 적용되는 추적을 생성하는 경우 모든 리전의 로그 파일 전송에 대한 SNS 알림이 사용자가 생성하는 단일 SNS 주제로 전송됩니다.
새로 만들기를 선택한 경우 새 주제의 이름을 CloudTrail 지정하거나 이름을 입력할 수 있습니다. [기존(Existing)]을 선택하는 경우 드롭다운 목록에서 SNS 주제를 선택합니다. 다른 리전 또는 적절한 권한이 있는 계정에서 주제의 ARN을 입력할 수도 있습니다. 자세한 내용은 에 대한 Amazon SNS 주제 정책 CloudTrail 단원을 참조하세요.
주제를 생성한 경우 로그 파일 전송에 대한 알림을 받으려면 해당 주제를 구독해야 합니다. Amazon SNS 콘솔에서 구독할 수 있습니다. 알림의 빈도로 인해 Amazon SQS 대기열을 사용하여 알림을 프로그래밍 방식으로 처리하도록 구독을 구성하는 것이 좋습니다. 자세한 내용은 Amazon Simple Notification Service 시작하기 가이드를 참조하세요.
-
-
필요에 따라 [로그에서 CloudWatch 활성화] 를 선택하여 CloudWatch 로그 파일을 Logs로 CloudTrail 전송하도록 구성할 수 있습니다. 자세한 정보는 CloudWatch Logs에 이벤트 전송을 참조하세요.
-
CloudWatch 로그와의 통합을 활성화한 경우 새 로그 그룹을 만들려면 [새로 만들기] 를 선택하고 기존 로그 그룹을 사용하려면 [Existing] 을 선택합니다. 새로 만들기를 선택하는 경우 새 로그 그룹의 이름을 CloudTrail 지정하거나 이름을 입력할 수 있습니다.
-
[기존(Existing)]을 선택하는 경우 드롭다운 목록에서 로그 그룹을 선택합니다.
-
로그를 Logs로 전송할 수 있는 권한을 위한 새 IAM 역할을 생성하려면 New를 CloudWatch 선택합니다. 드롭다운 목록에서 기존 IAM 역할을 선택하려면 [기존(Existing)]을 선택합니다. [정책 문서(Policy document)]를 확장하면 새 역할 또는 기존 역할의 정책 문이 표시됩니다. 이에 대한 자세한 내용은 모니터링에 CloudWatch 로그를 CloudTrail 사용하기 위한 역할 정책 문서 단원을 참조하세요.
참고
-
추적을 구성할 때 다른 계정에 속한 S3 버킷 및 SNS 주제를 선택할 수 있습니다. 하지만 로그 CloudWatch 로그 그룹에 이벤트를 CloudTrail 전송하려면 현재 계정에 있는 로그 그룹을 선택해야 합니다.
관리 계정만 콘솔을 사용하여 조직 트레일의 CloudWatch 로그 로그 그룹을 구성할 수 있습니다. 위임된 관리자는 OR AWS CLI CloudTrail
CreateTrail또는UpdateTrailAPI 작업을 사용하여 CloudWatch 로그 로그 그룹을 구성할 수 있습니다.
-
-
-
태그에 대해 하나 이상의 사용자 정의 태그(키-값 페어)를 추적에 추가합니다. 태그를 사용하면 CloudTrail 트레일과 CloudTrail 로그 파일이 포함된 Amazon S3 버킷을 모두 식별할 수 있습니다. 그러면 리소스에 리소스 그룹을 사용할 수 있습니다. CloudTrail 자세한 내용은 AWS Resource Groups 및 리소스에 CloudTrail 태그를 사용하는 이유는 무엇인가요? 섹션을 참조하세요.
-
[로그 이벤트 선택(Choose log events)] 페이지에서 로그하려는 이벤트 유형을 선택합니다. Management events(관리 이벤트)에서 다음을 수행합니다.
-
[API 활동(API activity)]에서 추적이 [읽기(Read)] 이벤트, [쓰기(Write)] 이벤트 또는 둘 다를 로그하도록 할지 선택합니다. 자세한 정보는 관리 이벤트을 참조하세요.
-
AWS KMS 이벤트 제외를 선택하여 트레일에서 이벤트를 필터링 AWS Key Management Service (AWS KMS) 할 수 있습니다. 기본 설정은 모든 AWS KMS 이벤트를 포함하는 것입니다.
AWS KMS 이벤트를 기록하거나 제외하는 옵션은 트레일에 관리 이벤트를 기록하는 경우에만 사용할 수 있습니다. 관리 이벤트를 기록하지 않도록 선택하면 이벤트가 기록되지 않으며 AWS KMS 이벤트 로깅 설정을 변경할 수 없습니다. AWS KMS
AWS KMS
Encrypt,Decrypt, 와 같은 작업은GenerateDataKey일반적으로 대규모 (99% 이상) 의 이벤트를 생성합니다. 이러한 작업은 이제 읽기 이벤트로 로그됩니다. ,DisableDelete, 및ScheduleKey(일반적으로 이벤트 볼륨의 0.5% 미만) 와 같은 관련성이 낮은 AWS KMS 작업은 쓰기 AWS KMS 이벤트로 기록됩니다.EncryptDecryptGenerateDataKey, 및 와 같은 대용량 이벤트를 제외하지만 여전히 기록하려면 쓰기 관리 이벤트를 기록하도록 선택하고 이벤트 제외 확인란의 선택을 취소하십시오.DisableDeleteScheduleKeyAWS KMS -
[Amazon RDS Data API 이벤트 제외(Exclude Amazon RDS Data API events)]를 선택하여 추적에서 Amazon Relational Database Service Data API 이벤트를 필터링합니다. 기본 설정은 모든 Amazon RDS Data API 이벤트를 포함하는 것입니다. Amazon RDS Data API 이벤트에 대한 자세한 내용은 Amazon RDS for Aurora 사용 설명서에서 AWS CloudTrail을 사용하여 데이터 API 호출 로깅 단원을 참조하세요.
-
-
데이터 이벤트를 로그하려면 [데이터 이벤트(Data events)]를 선택합니다. 데이터 이벤트 로깅에는 추가 요금이 부과됩니다. 자세한 내용은 AWS CloudTrail 요금
을 참조하십시오. -
중요
12~16단계는 기본값인 고급 이벤트 선택기를 사용하여 데이터 이벤트를 구성하는 단계입니다. 고급 이벤트 선택기를 사용하면 더 많은 데이터 이벤트 유형을 구성하고 추적에서 캡처하는 데이터 이벤트를 세밀하게 제어할 수 있습니다. 기본 이벤트 선택기를 사용하기로 선택했다면, 기본 이벤트 선택기를 사용하여 데이터 이벤트 설정 구성의 단계를 완료한 다음 이 절차의 17단계로 돌아갑니다.
[데이터 이벤트 유형(Data event type)]에서 데이터 이벤트를 로그할 리소스 유형을 선택합니다. 사용할 수 있는 데이터 이벤트 유형에 대한 자세한 내용은 데이터 이벤트 섹션을 참조하세요.
참고
Lake Formation에서 생성한 AWS Glue 테이블의 데이터 이벤트를 로깅하려면 Lake Formation을 선택합니다.
-
로그 셀렉터 템플릿을 선택하세요. CloudTrail 리소스 유형에 대한 모든 데이터 이벤트를 기록하는 사전 정의된 템플릿이 포함되어 있습니다. 사용자 지정 로그 선택기 템플릿을 구축하려면 [사용자 지정(Custom)]을 선택합니다.
참고
S3 버킷에 대해 미리 정의된 템플릿을 선택하면 현재 AWS 계정에 있는 모든 버킷과 트레일 생성을 완료한 후 생성한 모든 버킷에 대한 데이터 이벤트 로깅이 가능합니다. 또한 계정의 모든 IAM 자격 증명에 의해 수행된 데이터 이벤트 활동을 기록할 수 있으며, 이는 해당 활동이 다른 AWS 계정에 속한 버킷에서 수행된 경우에도 마찬가지입니다. AWS
한 리전에만 추적을 적용하는 경우 모든 S3 버킷을 로그하는 사전 정의된 템플릿을 선택하면 추적과 동일한 리전의 모든 버킷과 해당 리전에서 나중에 생성하는 버킷에 대해 데이터 이벤트 로깅이 활성화됩니다. AWS 계정의 다른 지역에 있는 Amazon S3 버킷에 대한 데이터 이벤트는 기록하지 않습니다.
모든 리전에 대한 트레일을 생성하는 경우, Lambda 함수의 사전 정의된 템플릿을 선택하면 현재 AWS 계정에 있는 모든 함수와 트레일 생성을 완료한 후 원하는 리전에 생성할 수 있는 모든 Lambda 함수에 대한 데이터 이벤트 로깅이 가능합니다. 단일 리전에 대한 트레일을 생성하는 경우 (를 사용하여 AWS CLI), 이 옵션을 선택하면 AWS 계정의 해당 리전에 현재 있는 모든 함수와 트레일 생성을 완료한 후 해당 리전에 생성할 수 있는 모든 Lambda 함수에 대한 데이터 이벤트 로깅이 활성화됩니다. 다른 리전에서 생성되는 Lambda 함수에 대한 데이터 이벤트 로깅은 활성화되지 않습니다.
또한 모든 함수에 대한 데이터 이벤트를 로깅하면 계정의 모든 IAM ID가 수행한 데이터 이벤트 활동을 로깅할 수 있으며, 이는 해당 활동이 다른 AWS 계정에 속한 함수에서 수행된 경우에도 마찬가지입니다. AWS
-
(선택 사항) 선택자 이름(Selector name)에 선택자를 식별할 이름을 입력합니다. 선택기 이름은 "2개의 S3 버킷에 대한 데이터 이벤트 로그그"애와 같이 고급 이벤트 선택기를 설명하는 이름입니다. 선택기 이름은 고급 이벤트 선택기에서의
Name으로 나열되며, JSON 뷰(JSON view)를 확장하여 볼 수 있습니다. -
[고급 이벤트 선택기(Advanced event selectors)]에서 데이터 이벤트를 로그하려는 특정 리소스에 대한 표현식을 작성합니다. 사전 정의된 로그 템플릿을 사용한다면 이 단계를 건너뛸 수 있습니다.
-
다음 필드 중에서 선택합니다.
-
readOnly-readOnly또는 값과 같도록 설정할 수 있습니다.truefalse읽기 전용 데이터 이벤트는Get*또는Describe*이벤트와 같이 리소스의 상태를 변경하지 않는 이벤트입니다. 쓰기 이벤트는Put*,Delete*또는Write*이벤트와 같이 리소스, 속성 또는 아티팩트를 추가, 변경 또는 삭제합니다.read이벤트와write이벤트를 모두 로그하려면readOnly선택기를 추가하지 마세요. -
eventName-eventName은 연산자를 사용할 수 있습니다. 이를 사용하여 CloudTrail, 또는 와 같이PutBucket기록된 모든 데이터 이벤트를 포함하거나GetSnapshotBlock제외할 수 있습니다.PutItem -
resources.ARN- 와 함께resources.ARN모든 연산자를 사용할 수 있지만 같거나 같지 않은 연산자를 사용하는 경우 값은 템플릿에서 값으로 지정한 유형의 유효한 리소스 ARN과 정확히 일치해야 합니다.resources.type다음 표는 각
resources.type에 대한 유효한 ARN 형식을 보여 줍니다.참고
ARN이 없는 리소스 유형을 필터링하는 데는
resources.ARN필드를 사용할 수 없습니다.resources.type resources.ARN AWS::DynamoDB::Table1arn:partition:dynamodb:region:account_ID:table/table_nameAWS::Lambda::Functionarn:partition:lambda:region:account_ID:function:function_nameAWS::S3::Object2arn:partition:s3:::bucket_name/ arn:partition:s3:::bucket_name/object_or_file_name/AWS::AppConfig::Configurationarn:partition:appconfig:region:account_ID:application/application_ID/environment/environment_ID/configuration/configuration_profile_IDAWS::B2BI::Transformerarn:partition:b2bi:region:account_ID:transformer/transformer_IDAWS::Bedrock::AgentAliasarn:partition:bedrock:region:account_ID:agent-alias/agent_ID/alias_IDAWS::Bedrock::KnowledgeBasearn:partition:bedrock:region:account_ID:knowledge-base/knowledge_base_IDAWS::Cassandra::Tablearn:partition:cassandra:region:account_ID:keyspace/keyspace_name/table/table_nameAWS::CloudFront::KeyValueStorearn:partition:cloudfront:region:account_ID:key-value-store/KVS_nameAWS::CloudTrail::Channelarn:partition:cloudtrail:region:account_ID:channel/channel_UUIDAWS::CodeWhisperer::Customizationarn:partition:codewhisperer:region:account_ID:customization/customization_IDAWS::CodeWhisperer::Profilearn:partition:codewhisperer:region:account_ID:profile/profile_IDAWS::Cognito::IdentityPoolarn:partition:cognito-identity:region:account_ID:identitypool/identity_pool_IDAWS::DynamoDB::Streamarn:partition:dynamodb:region:account_ID:table/table_name/stream/date_timeAWS::EC2::Snapshotarn:partition:ec2:region::snapshot/snapshot_IDAWS::EMRWAL::Workspacearn:partition:emrwal:region:account_ID:workspace/workspace_nameAWS::FinSpace::Environmentarn:partition:finspace:region:account_ID:environment/environment_IDAWS::Glue::Tablearn:partition:glue:region:account_ID:table/database_name/table_nameAWS::GreengrassV2::ComponentVersionarn:partition:greengrass:region:account_ID:components/component_nameAWS::GreengrassV2::Deploymentarn:partition:greengrass:region:account_ID:deployments/deployment_IDAWS::GuardDuty::Detectorarn:partition:guardduty:region:account_ID:detector/detector_IDAWS::IoT::Certificatearn:partition:iot:region:account_ID:cert/certificate_IDAWS::IoT::Thingarn:partition:iot:region:account_ID:thing/thing_IDAWS::IoTSiteWise::Assetarn:partition:iotsitewise:region:account_ID:asset/asset_IDAWS::IoTSiteWise::TimeSeriesarn:partition:iotsitewise:region:account_ID:timeseries/timeseries_IDAWS::IoTTwinMaker::Entityarn:partition:iottwinmaker:region:account_ID:workspace/workspace_ID/entity/entity_IDAWS::IoTTwinMaker::Workspacearn:partition:iottwinmaker:region:account_ID:workspace/workspace_IDAWS::KendraRanking::ExecutionPlanarn:partition:kendra-ranking:region:account_ID:rescore-execution-plan/rescore_execution_plan_IDAWS::KinesisVideo::Streamarn:partition:kinesisvideo:region:account_ID:stream/stream_name/creation_timeAWS::ManagedBlockchain::Networkarn:partition:managedblockchain:::networks/network_nameAWS::ManagedBlockchain::Nodearn:partition:managedblockchain:region:account_ID:nodes/node_IDAWS::MedicalImaging::Datastorearn:partition:medical-imaging:region:account_ID:datastore/data_store_IDAWS::NeptuneGraph::Grapharn:partition:neptune-graph:region:account_ID:graph/graph_IDAWS::PCAConnectorAD::Connectorarn:partition:pca-connector-ad:region:account_ID:connector/connector_IDAWS::QBusiness::Applicationarn:partition:qbusiness:region:account_ID:application/application_IDAWS::QBusiness::DataSourcearn:partition:qbusiness:region:account_ID:application/application_ID/index/index_ID/data-source/datasource_IDAWS::QBusiness::Indexarn:partition:qbusiness:region:account_ID:application/application_ID/index/index_IDAWS::QBusiness::WebExperiencearn:partition:qbusiness:region:account_ID:application/application_ID/web-experience/web_experienc_IDAWS::RDS::DBClusterarn:partition:rds:region:account_ID:cluster/cluster_nameAWS::S3::AccessPoint3arn:partition:s3:region:account_ID:accesspoint/access_point_nameAWS::S3ObjectLambda::AccessPointarn:partition:s3-object-lambda:region:account_ID:accesspoint/access_point_nameAWS::S3Outposts::Objectarn:partition:s3-outposts:region:account_ID:object_pathAWS::SageMaker::Endpointarn:partition:sagemaker:region:account_ID:endpoint/endpoint_nameAWS::SageMaker::ExperimentTrialComponentarn:partition:sagemaker:region:account_ID:experiment-trial-component/experiment_trial_component_nameAWS::SageMaker::FeatureGrouparn:partition:sagemaker:region:account_ID:feature-group/feature_group_nameAWS::SCN::Instancearn:partition:scn:region:account_ID:instance/instance_IDAWS::ServiceDiscovery::Namespacearn:partition:servicediscovery:region:account_ID:namespace/namespace_IDAWS::ServiceDiscovery::Servicearn:partition:servicediscovery:region:account_ID:service/service_IDAWS::SNS::PlatformEndpointarn:partition:sns:region:account_ID:endpoint/endpoint_type/endpoint_name/endpoint_IDAWS::SNS::Topicarn:partition:sns:region:account_ID:topic_nameAWS::SQS::Queuearn:partition:sqs:region:account_ID:queue_nameAWS::SSM::ManagedNodeARN은 다음 형식 중 하나여야 합니다.
-
arn:partition:ssm:region:account_ID:managed-instance/instance_ID -
arn:partition:ec2:region:account_ID:instance/instance_ID
AWS::SSMMessages::ControlChannelarn:partition:ssmmessages:region:account_ID:control-channel/control_channel_IDAWS::SWF::Domainarn:partition:swf:region:account_ID:/domain/domain_nameAWS::ThinClient::Devicearn:partition:thinclient:region:account_ID:device/device_IDAWS::ThinClient::Environmentarn:partition:thinclient:region:account_ID:environment/environment_IDAWS::Timestream::Databasearn:partition:timestream:region:account_ID:database/database_nameAWS::Timestream::Tablearn:partition:timestream:region:account_ID:database/database_name/table/table_nameAWS::VerifiedPermissions::PolicyStorearn:partition:verifiedpermissions:region:account_ID:policy-store/policy_store_ID1 스트림이 활성화된 테이블의 경우 데이터 이벤트의
resources필드에AWS::DynamoDB::Stream과AWS::DynamoDB::Table이 모두 포함됩니다.resources.type으로AWS::DynamoDB::Table을 지정하는 경우 기본적으로 DynamoDB 테이블과 DynamoDB 스트림 이벤트가 모두 로깅됩니다. 스트림 이벤트를 제외하려면eventName필드에 필터를 추가하십시오.2 특정 S3 버킷의 모든 객체에 대한 모든 데이터 이벤트를 로깅하려면,
StartsWith연산자를 사용하고 일치하는 값으로 버킷 ARN만 포함합니다. 후행 슬래시는 의도적인 것입니다. 제외하지 마세요.3 S3 액세스 포인트의 모든 객체에 대한 이벤트를 로깅하려면 액세스 포인트 ARN만을 사용하고, 객체 경로를 포함하지 않으며,
StartsWith또는NotStartsWith연산자를 사용할 것을 권장합니다. -
데이터 이벤트 리소스의 ARN 형식에 대한 자세한 내용은 AWS Identity and Access Management 사용 설명서의 작업, 리소스 및 조건 키 단원을 참조하세요.
-
-
각 필드에 대해 [+ 조건(+ Condition)]을 선택하여 모든 조건에 대해 최대 500개의 지정된 값까지 필요한 만큼 조건을 추가합니다. 예를 들어, 트레일에 기록되는 데이터 이벤트에서 두 S3 버킷의 데이터 이벤트를 제외하려면 필드를 Resources.ARN으로 설정하고 연산자를 for not start 로 설정한 다음 S3 버킷 ARN을 붙여넣거나 이벤트를 기록하지 않으려는 S3 버킷을 찾아보면 됩니다.
두 번째 S3 버킷을 추가하려면 [+ 조건(+ Condition)]을 선택한 다음, 이전 지침을 반복하여 ARN을 붙여넣거나 다른 버킷을 찾습니다.
참고
추적의 모든 선택기에 대해 최대 500개의 값을 가질 수 있습니다. 여기에는
eventName과 같은 선택기에 대한 여러 값의 배열이 포함됩니다. 모든 선택기에 대해 단일 값이 있는 경우 선택기에 최대 500개의 조건을 추가할 수 있습니다.계정에 15,000개가 넘는 Lambda 함수가 있는 경우 트레일을 생성할 때 콘솔에서 CloudTrail 모든 함수를 보거나 선택할 수 없습니다. 함수가 표시되지 않는 경우에도 사전 정의된 선택기 템플릿을 사용하여 모든 함수를 여전히 로그할 수 있습니다. 특정 함수에 대한 데이터 이벤트를 로그하려면 함수를 수동으로 추가할 수 있습니다(함수의 ARN을 알고 있는 경우). 콘솔에서 트레일 생성을 완료한 다음 및 put-event-selectors 명령을 사용하여 특정 Lambda 함수에 대한 데이터 이벤트 로깅을 구성할 수도 있습니다. AWS CLI 자세한 정보는 를 사용하여 트레일을 관리합니다. AWS CLI을 참조하세요.
-
필요에 따라 필드를 추가하려면 [+ 필드(+ Field)]를 선택합니다. 오류를 방지하려면 필드에 충돌하거나 중복되는 값을 설정하지 마세요. 예를 들어 한 선택기의 ARN을 값과 같도록 지정하지 마세요. 그런 다음, ARN이 다른 선택기의 동일한 값과 같지 않도록 지정하세요.
-
-
데이터 이벤트를 로그할 다른 데이터 유형을 추가하려면 [데이터 이벤트 유형 추가(Add data event type)]를 선택합니다. 데이터 이벤트 유형에 대한 고급 이벤트 선택기를 구성하려면 12단계부터 이 단계까지 반복합니다.
-
트레일에 Insights 이벤트를 기록하도록 하려면 CloudTrail Insights 이벤트를 선택하십시오.
[이벤트 유형(Event type)]에서 [Insights 이벤트(Insights events)]를 선택합니다. API 호출률에 대한 Insights 이벤트를 로그하려면 쓰기(Write) 관리 이벤트를 로그하고 있어야 합니다. API 오류율에 대한 Insights 이벤트를 로그하려면 읽기(Read) 또는 쓰기(Write) 관리 이벤트를 로그하고 있어야 합니다.
CloudTrail Insights는 관리 이벤트에서 비정상적인 활동을 분석하고 이상이 감지되면 이벤트를 기록합니다. 기본적으로 추적은 인사이트 이벤트를 로그하지 않습니다. 인사이트에 이벤트에 대한 자세한 내용은 Insights 이벤트 로깅 단원을 참조하세요. 인사이트 이벤트 로깅에는 추가 요금이 부과됩니다. CloudTrail 가격 책정은 요금을 참조하십시오.AWS CloudTrail
Insights 이벤트는 트레일 세부 정보 페이지의 스토리지 위치 영역에 지정된 동일한 S3
/CloudTrail-Insight버킷의 이름이 지정된 다른 폴더로 전송됩니다. CloudTrail새 접두사를 자동으로 생성합니다. 예를 들어, 현재 대상 S3 버킷의 이름이S3bucketName/AWSLogs/CloudTrail/인 경우 새 접두사가 있는 S3 버킷 이름은S3bucketName/AWSLogs/CloudTrail-Insight/이 됩니다. -
로그할 이벤트 유형의 선택을 마쳤으면 [다음(Next)]을 선택합니다.
-
[검토 및 생성(Review and create)] 페이지에서 선택 사항을 검토합니다. 단원에 표시된 추적 설정을 변경하려면 해당 단원에서 [편집(Edit)]을 선택합니다. 추적을 생성할 준비가 되었으면 [추적 생성(Create trail)]을 선택합니다.
-
[Trails] 페이지에 새 추적이 나타납니다. 약 5분 후에 계정에서 이루어진 AWS API 호출을 보여주는 로그 파일을 CloudTrail 게시합니다. 지정한 S3 버킷에서 로그 파일을 볼 수 있습니다. Insights 이벤트 로깅을 활성화했는데 비정상적인 활동이 감지되면 첫 번째 Insights 이벤트가 전달되는 데 최대 36시간이 걸릴 수 있습니다. CloudTrail
참고
CloudTrail 일반적으로 API 호출 후 평균 약 5분 이내에 로그를 전달합니다. 이 시간은 보장되지 않습니다. 자세한 내용은 AWS CloudTrail 서비스 수준 계약
에서 검토하세요. 트레일을 잘못 구성한 경우 (예: S3 버킷에 연결할 수 없는 경우) 는 30일 동안 S3 버킷으로 로그 파일 재배송을 시도하며, 이러한 attempted-to-deliver 이벤트에는 표준 CloudTrail 요금이 적용됩니다. CloudTrail 잘못 구성된 추적에 대한 요금이 부과되지 않도록 하려면 추적을 삭제해야 합니다.
기본 이벤트 선택기를 사용하여 데이터 이벤트 설정 구성
고급 이벤트 선택기를 사용하여 모든 데이터 이벤트 유형을 구성할 수 있습니다. 고급 이벤트 선택기를 사용하면 세밀한 선택기를 만들어 관심 있는 이벤트만 기록할 수 있습니다.
기본 이벤트 선택기를 사용하여 데이터 이벤트를 기록하는 경우 Amazon S3 버킷, AWS Lambda 함수 및 Amazon DynamoDB 테이블에 대한 데이터 이벤트 로깅으로 제한됩니다. 기본 이벤트 선택기를 사용하여 eventName 필드를 필터링할 수는 없습니다.
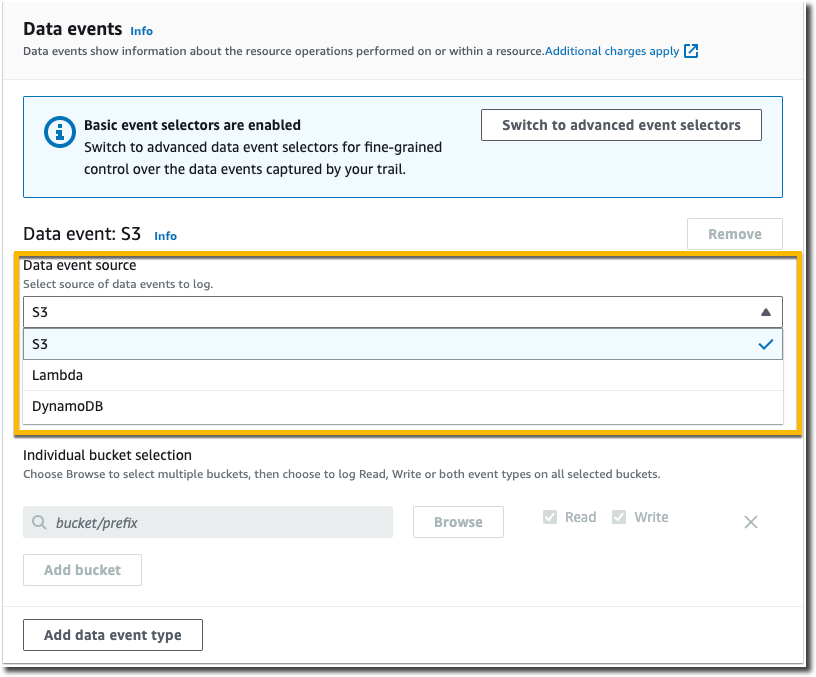
다음 절차에 따라 기본 이벤트 선택기를 사용하여 데이터 이벤트 설정을 구성합니다.
기본 이벤트 선택기를 사용하여 데이터 이벤트 설정 구성
-
[데이터(Events)]에서 [데이터 이벤트(Data events)]를 선택하여 데이터 이벤트를 로깅합니다. 데이터 이벤트 로깅에는 추가 요금이 부과됩니다. 자세한 내용은 AWS CloudTrail 요금
을 참조하십시오. -
Amazon S3 버킷의 경우:
-
[데이터 이벤트 소스(Data event source)]에서 S3를 선택합니다.
-
[현재 및 미래의 모든 S3 버킷(All current and future S3 buckets)]을 로그하도록 선택하거나 개별 버킷 또는 함수를 지정할 수 있습니다. 기본적으로 데이터 이벤트는 현재 및 미래의 모든 S3 버킷에 대해 로그됩니다.
참고
기본값인 모든 현재 및 미래 S3 버킷 옵션을 유지하면 현재 AWS 계정에 있는 모든 버킷과 트레일 생성을 완료한 후 생성하는 모든 버킷에 대한 데이터 이벤트 로깅이 활성화됩니다. 또한 계정의 모든 IAM 자격 증명에 의해 수행된 데이터 이벤트 활동을 기록할 수 있으며, 이는 해당 활동이 다른 AWS 계정에 속한 버킷에서 수행된 경우에도 마찬가지입니다. AWS
를 사용하여 단일 지역에 대한 트레일을 생성하는 경우 현재 및 미래의 모든 S3 버킷을 선택하면 트레일과 동일한 리전에 있는 모든 버킷과 해당 리전에서 나중에 생성하는 모든 버킷에 대한 데이터 이벤트 로깅이 활성화됩니다. AWS CLI AWS 계정의 다른 지역에 있는 Amazon S3 버킷에 대한 데이터 이벤트는 기록하지 않습니다.
-
기본값인 [현재 및 미래의 모든 S3 버킷(All current and future S3 buckets)]을 그대로 둘 경우 [읽기(Read)] 이벤트, [쓰기(Write)] 이벤트 또는 둘 다를 로그하도록 선택합니다.
-
개별 버킷을 선택하려면 [현재 및 미래의 모든 S3 버킷(All current and future S3 buckets)]에서 [읽기(Read)] 및 [쓰기(Write)] 확인란의 선택을 해제합니다. [개별 버킷 선택(Individual bucket selection)]에서 데이터 이벤트를 로그할 버킷을 찾습니다. 원하는 버킷의 버킷 접두사를 입력하여 특정 버킷을 찾습니다. 이 창에서 여러 버킷을 선택할 수 있습니다. 더 많은 버킷의 데이터 이벤트를 로그하려면 [버킷 추가(Add bucket)]를 선택합니다. [읽기(Read)] 이벤트(예:
GetObject), [쓰기(Write)] 이벤트(예:PutObject) 또는 둘 다를 로그하도록 선택합니다.이 설정은 개별 버킷에 대해 구성한 개별 설정보다 우선 적용됩니다. 예를 들어 모든 S3 버킷에 대해 [읽기(Read)] 이벤트 로깅을 지정한 다음, 데이터 이벤트 로깅 대상으로 특정 버킷을 추가하기로 선택하면 추가한 버킷에 대해 [읽기(Read)]가 사전 선택됩니다. 선택을 취소할 수 없습니다. [Write]에 대한 옵션만 구성할 수 있습니다.
로깅에서 버킷을 제거하려면 X를 선택합니다.
-
-
데이터 이벤트를 로그할 다른 데이터 유형을 추가하려면 [데이터 이벤트 유형 추가(Add data event type)]를 선택합니다.
-
Lambda 함수의 경우:
-
[데이터 이벤트 소스(Data event source)]에서 Lambda를 선택합니다.
-
[Lambda 함수(Lambda function)]에서 [모든 리전(All regions)]을 선택하여 모든 Lambda 함수를 로그하거나 [ARN으로 입력 함수(Input function as ARN)]를 선택하여 특정 함수에 대한 데이터 이벤트를 로그합니다.
AWS 계정의 모든 Lambda 함수에 대한 데이터 이벤트를 로깅하려면 모든 현재 및 미래 함수 로깅을 선택합니다. 이 설정은 개별 함수에 대해 구성한 개별 설정보다 우선합니다. 일부 함수가 표시되지 않더라도 모든 함수가 로그됩니다.
참고
모든 리전에 대해 추적을 생성할 경우 이 옵션을 선택하면 현재 AWS 계정에 있는 모든 함수와 추적 생성을 완료한 후 리전에서 생성할 수 있는 Lambda 함수에 대해 데이터 이벤트 로깅이 활성화됩니다. 단일 리전에 대한 트레일을 생성하는 경우 (를 사용하여 AWS CLI), 이 옵션을 선택하면 AWS 계정의 해당 리전에 현재 있는 모든 함수와 트레일 생성을 완료한 후 해당 리전에 생성할 수 있는 모든 Lambda 함수에 대한 데이터 이벤트 로깅이 활성화됩니다. 다른 리전에서 생성되는 Lambda 함수에 대한 데이터 이벤트 로깅은 활성화되지 않습니다.
또한 모든 함수에 대한 데이터 이벤트를 로깅하면 계정의 모든 IAM ID가 수행한 데이터 이벤트 활동을 로깅할 수 있으며, 이는 해당 활동이 다른 AWS 계정에 속한 함수에서 수행된 경우에도 마찬가지입니다. AWS
-
[ARN으로 입력 함수(Input function as ARN)]를 선택한 경우 Lambda 함수의 ARN을 입력합니다.
참고
계정에 15,000개가 넘는 Lambda 함수가 있는 경우 트레일을 생성할 때 콘솔에서 CloudTrail 모든 함수를 보거나 선택할 수 없습니다. 함수가 모두 표시되지는 않더라도 모든 함수를 로그하는 옵션을 선택할 수 있습니다. 특정 함수에 대한 데이터 이벤트를 로그하려면 함수를 수동으로 추가할 수 있습니다(함수의 ARN을 알고 있는 경우). 콘솔에서 트레일 생성을 완료한 다음 및 put-event-selectors 명령을 사용하여 특정 Lambda 함수에 대한 데이터 이벤트 로깅을 구성할 수도 있습니다. AWS CLI 자세한 정보는 를 사용하여 트레일을 관리합니다. AWS CLI을 참조하세요.
-
-
DynamoDB 테이블의 경우:
-
[데이터 이벤트 소스(Data event source)]에서 DynamoDB를 선택합니다.
-
[DynamoDB 테이블 선택(DynamoDB table selection)]에서 [찾아보기(Browse)]를 선택하여 테이블을 선택하거나 액세스 권한이 있는 DynamoDB 테이블의 ARN을 붙여넣습니다. DynamoDB 테이블 ARN은 다음의 형식을 사용합니다.
arn:partition:dynamodb:region:account_ID:table/table_name다른 테이블을 추가하려면 [행 추가(Add row)]를 선택하고 테이블을 찾거나 액세스 권한이 있는 테이블의 ARN을 붙여넣습니다.
-
-
추적에 대한 Insights 이벤트 및 기타 설정을 구성하려면 이 주제인 콘솔에서 추적 생성의 이전 절차로 돌아갑니다.
다음 단계
추적을 생성한 후 추적으로 돌아가 변경할 수 있습니다.
-
아직 하지 않았다면 로그 파일을 CloudTrail Logs로 전송하도록 구성할 수 있습니다. CloudWatch 자세한 정보는 CloudWatch Logs에 이벤트 전송을 참조하세요.
-
테이블을 생성하고 이를 사용해 Amazon Athena에서 쿼리를 실행함으로써 AWS 서비스 활동을 분석할 수 있습니다. 자세한 내용은 Amazon Athena 사용 설명서의 CloudTrail 콘솔에서 CloudTrail 로그용 테이블 생성을 참조하십시오.
-
추적에 사용자 지정 태그(키-값 쌍)를 추가합니다.
-
다른 추적을 생성하려면 [추적(Trails)] 페이지를 열고 [추적 생성(Create trail)]를 선택합니다.