Amplify Documentation for Swift
AWS Amplify is everything mobile developers need to develop cloud-powered fullstack applications without hassle. Easily connect your cross-platform applications to the cloud for data modeling, authentication, storage, serverless functions, and more.
Build fullstack apps with your framework of choice
You can use AWS Amplify with popular web and mobile frameworks like JavaScript, Flutter, Swift, and React. Build, connect, and host fullstack apps on AWS. Get started by selecting your preferred framework.
Features
Code-first DX
The new code-first developer experience lets you define your infrastructure with TypeScript.
Fullstack Git deployments
Deploy your frontend and backend together on every code commit. Your Git branch is the source of truth.
Faster local development
Per-developer cloud sandbox environments let you quickly iterate during development.
Develop
- Generate and use your data without hassleUse TypeScript to define your data and let us handle the model and configuration file generations.
- Authn and authz for secure appsChoose the auth strategy (such as passwords, social, email links) and control data access based on users and groups.
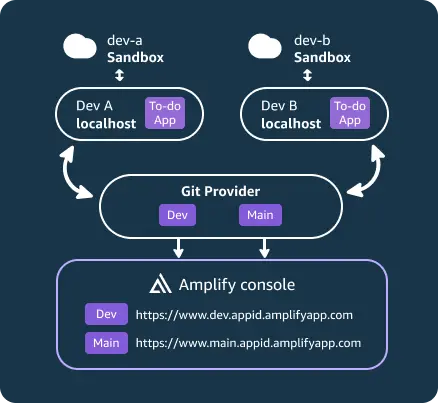
Deploy
- Faster iterations with per-developer sandboxesPer-developer cloud sandboxes provide high fidelity and faster deployment times to make local iteration quick.
- Zero-config fullstack branchesFullstack deployments from your Git branch. Autodeploy Git branches to set up staging, development, and production environments.
- GUI to manage your dataManage your app data, users and groups, and files in a single console.
Customize
- Add any AWS service with CDKExtend or customize with the AWS CDK to access 200+ AWS services.
- Bring your own pipelinesUse your own pipelines to set up cross-account or multi-region, stage-based deployments.
- Monorepo and multi-repo supportEnable support for all types of fullstack team workflows: monorepos, micro frontends, multi-repos, and more.
import * as sns from 'aws-cdk-lib/aws-sns';import * as sqs from 'aws-cdk-lib/aws-sqs';import { defineBackend } from '@aws-amplify/backend';import { auth } from './auth/resource.js';import { data } from './data/resource.js';
const backend = defineBackend({ auth, data});
const customResourceStack = backend.createStack('MyCustomResources');
new sqs.Queue(customResourceStack, 'CustomQueue');new sns.Topic(customResourceStack, 'CustomTopic');