Environment variables
Environment variables are key-value pairs that you can add to your application's settings to make them available to Amplify Hosting. As a best practice, you can use environment variables to expose application configuration data. All environment variables that you add are encrypted to prevent rogue access.
Amplify doesn't allow you to create environment variables with an AWS
prefix. This prefix is reserved for Amplify internal use only.
Important
Don't use environment variables to store secrets. Store secrets in an environment secret created using the AWS Systems Manager Parameter Store. For more information, see Environment secrets.
Amplify environment variables
The following environment variables are accessible by default within the Amplify console.
| Variable name | Description | Example value |
|---|---|---|
|
_BUILD_TIMEOUT |
The build timeout duration in minutes |
|
|
_LIVE_UPDATES |
The tool will be upgraded to the latest version. |
|
|
USER_DISABLE_TESTS |
The test step is skipped during a build. You can disable tests for all branches or specific branches in an app. This environment variable is used for apps that perform tests during the build phase. For more information about setting this variable, see Disabling tests. |
|
|
AWS_APP_ID |
The app ID of the current build |
|
|
AWS_BRANCH |
The branch name of the current build |
|
|
AWS_BRANCH_ARN |
The branch Amazon Resource Name (ARN) of the current build |
|
|
AWS_CLONE_URL |
The clone URL used to fetch the git repository contents |
|
|
AWS_COMMIT_ID |
The commit ID of the current build “HEAD” for rebuilds |
|
|
AWS_JOB_ID |
The job ID of the current build. This includes some padding of ‘0’ so it always has the same length. |
|
|
AWS_PULL_REQUEST_ID |
The pull request ID of the web preview build. This environment variable is only available when using GitHub as your repository provider. |
|
|
AMPLIFY_AMAZON_CLIENT_ID |
The Amazon client ID |
|
|
AMPLIFY_AMAZON_CLIENT_SECRET |
The Amazon client secret |
|
|
AMPLIFY_FACEBOOK_CLIENT_ID |
The Facebook client ID |
|
|
AMPLIFY_FACEBOOK_CLIENT_SECRET |
The Facebook client secret |
|
|
AMPLIFY_GOOGLE_CLIENT_ID |
The Google client ID |
|
|
AMPLIFY_GOOGLE_CLIENT_SECRET |
The Google client secret |
|
|
AMPLIFY_DIFF_DEPLOY |
Enable or disable diff based frontend deployment. For more information, see Enable or disable diff based frontend build and deploy. |
|
|
AMPLIFY_DIFF_DEPLOY_ROOT |
The path to use for diff based frontend deployment comparisons, relative to the root of your repository. |
|
|
AMPLIFY_DIFF_BACKEND |
Enable or disable diff based backend builds. For more information, see Enable or disable diff based backend builds |
|
|
AMPLIFY_BACKEND_PULL_ONLY |
Amplify manages this environment variable. For more information, see Edit an existing frontend to point to a different backend |
|
|
AMPLIFY_BACKEND_APP_ID |
Amplify manages this environment variable. For more information, see Edit an existing frontend to point to a different backend |
|
|
AMPLIFY_SKIP_BACKEND_BUILD |
If you do not have a backend section in your build specification and want
to disable backend builds, set this environment variable to
|
|
|
AMPLIFY_ENABLE_DEBUG_OUTPUT |
Set this variable to |
|
|
AMPLIFY_MONOREPO_APP_ROOT |
The path to use to specify the app root of a monorepo app, relative to the root of your repository. |
|
|
AMPLIFY_USERPOOL_ID |
The ID for the Amazon Cognito user pool imported for auth |
|
|
AMPLIFY_WEBCLIENT_ID |
The ID for the app client to be used by web applications The app client must be configured with access to the Amazon Cognito user pool specified by the AMPLIFY_USERPOOL_ID environment variable. |
|
|
AMPLIFY_NATIVECLIENT_ID |
The ID for the app client to be used by native applications The app client must be configured with access to the Amazon Cognito user pool specified by the AMPLIFY_USERPOOL_ID environment variable. |
|
|
AMPLIFY_IDENTITYPOOL_ID |
The ID for the Amazon Cognito identity pool |
|
|
AMPLIFY_PERMISSIONS_BOUNDARY_ARN |
The ARN for the IAM policy to use as a permissions boundary that
applies to all IAM roles created by Amplify. For more information, see
IAM Permissions Boundary for Amplify-generated roles |
|
|
AMPLIFY_DESTRUCTIVE_UPDATES |
Set this environment variable to true to allow a GraphQL API to be
updated with schema operations that can potentially cause data loss. For
more information, see Update schema |
|
Note
The AMPLIFY_AMAZON_CLIENT_ID and
AMPLIFY_AMAZON_CLIENT_SECRET environment variables are OAuth tokens, not
an AWS access key and secret key.
Set environment variables
Use the following instructions to set environment variables for an application in the Amplify console.
Note
Environment variables is visible in the Amplify console’s App settings menu only when an app is set up for continuous deployment and connected to a git repository. For instructions on this type of deployment, see Getting started with existing code.
To set environment variables
-
Sign in to the AWS Management Console and open the Amplify console
. -
In the Amplify console, choose App Settings, and then choose Environment variables.
-
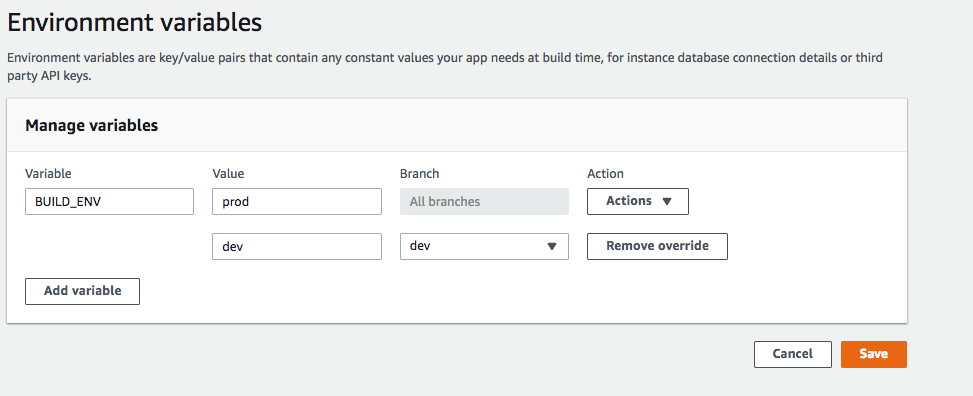
In the Environment variables section, choose Manage variables.
-
In the Manage variables section, under Variable, enter your key. For Value, enter your value. By default, Amplify applies the environment variables across all branches, so you don’t have to re-enter variables when you connect a new branch.
-
(Optional) To customize an environment variable specifically for a branch, add a branch override as follows:
-
Choose Actions and then choose Add variable override.
-
You now have a set of environment variables specific to your branch.

-
-
Choose Save.
Access environment variables at build time
To access an environment variable during a build, edit your build settings to include the environment variable in your build commands.
To edit build settings to include an environment variable
-
Sign in to the AWS Management Console and open the Amplify console
. -
In the Amplify console, choose App Settings, then choose Build settings.
-
In the App build specification section, choose Edit.
-
Add the environment variable to your build command. You should now be able to access your environment variable during your next build. This example changes the npm's behavior (BUILD_ENV) and adds an API token (TWITCH_CLIENT_ID) for an external service to an environment file for later use.
build: commands: - npm run build:$BUILD_ENV - echo "TWITCH_CLIENT_ID=$TWITCH_CLIENT_ID" >> backend/.env
Each command in your build configuration runs inside a Bash shell. For more information
on working with environment variables in Bash, see Shell Expansions
Making environment variables accessible to server-side runtimes
A Next.js server component doesn't have access to your app's environment variables by default. This behavior is intentional to protect any secrets stored in environment variables that your application uses during the build phase.
To make specific environment variables accessible to Next.js, you must modify the Amplify build specification file to set the environment variables in the environment files that Next.js recognizes. This enables Amplify to load the environment variables before it builds the application. For more information about modifying your build specification, see examples of how to add environment variables in the build commands section.
Create a new backend environment with authentication parameters for social sign-in
To connect a branch to an app
-
Sign in to the AWS Management Console and open the Amplify console
. -
The procedure for connecting a branch to an app varies depending on whether you are connecting a branch to a new app or an existing app.
-
Connecting a branch to a new app
-
On the Build settings page, locate the Select a backend environment to use with this branch section. For Environment, choose Create new environment, and enter the name of your backend environment. The following screenshot shows the Select a backend environment to use with this branch section of the Build settings page with
backendentered for the backend environment name.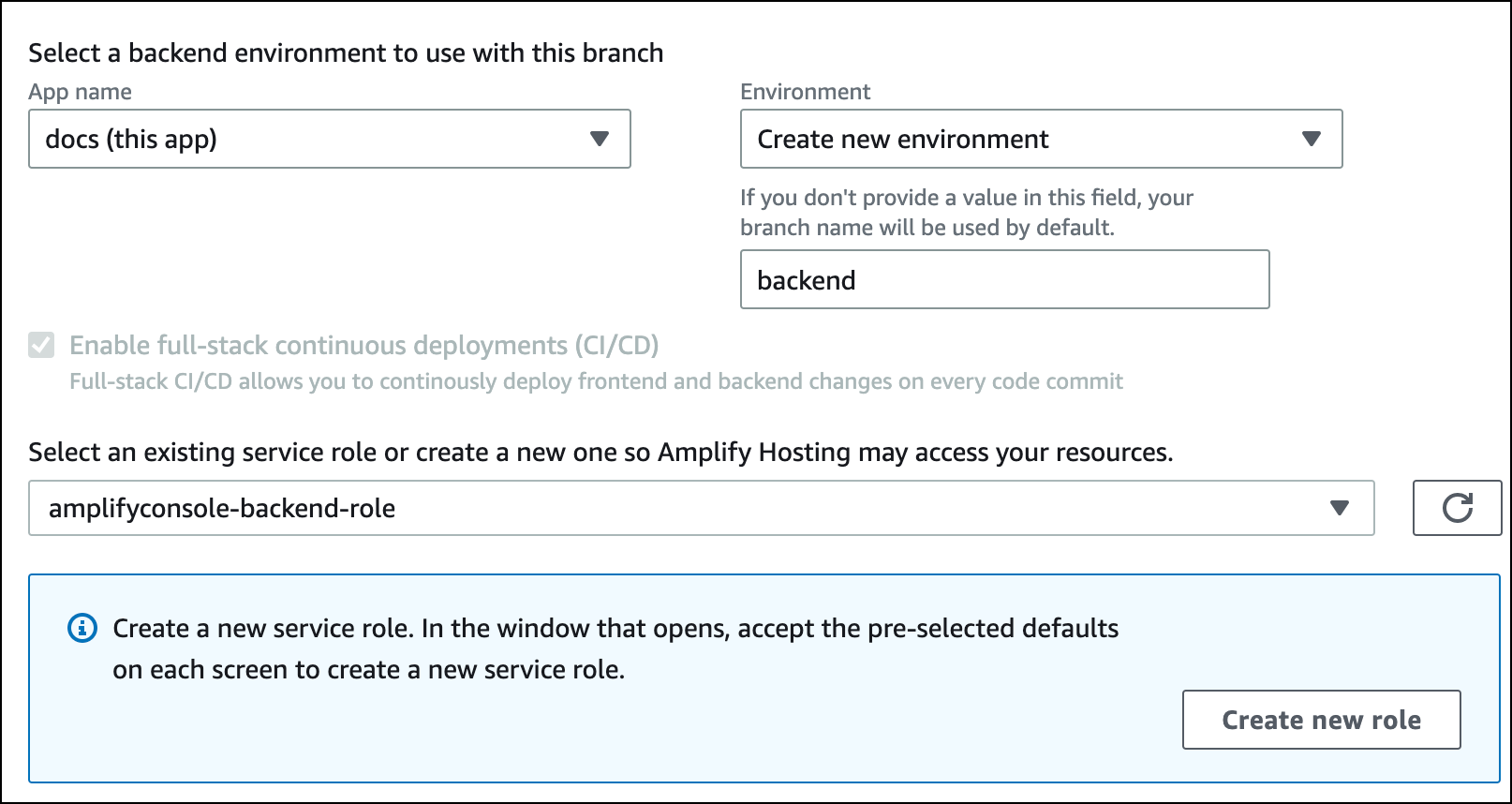
-
Expand the Advanced settings section on the Build settings page and add environment variables for social sign-in keys. For example,
AMPLIFY_FACEBOOK_CLIENT_SECRETis a valid environment variable. For the list of Amplify system environment variables that are available by default, see the table in Amplify environment variables.
-
-
Connecting a branch to an existing app
-
If you are connecting a new branch to an existing app, set the social sign-in environment variables before connecting the branch. In the navigation pane, choose App Settings, Environment variables.
-
In the Environment variables section, choose Manage variables.
-
In the Manage variables section, choose Add variable.
-
For Variable (key), enter your client ID. For Value, enter your client secret.
-
Choose, Save.
-
-
Frontend framework environment variables
If you are developing your app with a frontend framework that supports its own environment variables, it is important to understand that these are not the same as the environment variables you configure in the Amplify console. For example, React (prefixed REACT_APP) and Gatsby (prefixed GATSBY), enable you to create runtime environment variables that those frameworks automatically bundle into your frontend production build. To understand the effects of using these environment variables to store values, refer to the documentation for the frontend framework you are using.
Storing sensitive values, such as API keys, inside these frontend framework prefixed environment variables is not a best practice and is highly discouraged. For an example of using Amplify's build time environment variables for this purpose, see Access environment variables at build time.
Environment secrets
Environment secrets are similar to environment variables, but they are AWS Systems Manager (SSM) Parameter Store key value pairs that can be encrypted. Some values must be encrypted, such as the Sign in with Apple private key for Amplify.
Set environment secrets
Use the following instructions to set an environment secret for an Amplify app using the AWS Systems Manager console.
To set an environment secret
-
Sign in to the AWS Management Console and open the AWS Systems Manager console
. -
In the navigation pane, choose Application Management, then choose Parameter Store.
-
On the AWS Systems Manager Parameter Store page, choose Create parameter.
-
On the Create parameter page, in the Parameter details section, do the following:
-
For Name, enter a parameter in the format
/amplify/{your_app_id}/{your_backend_environment_name}/{your_parameter_name}. -
For Type, choose SecureString.
-
For KMS key source, choose My current account to use the default key for your account.
-
For Value, enter your secret value to encrypt.
-
-
Choose, Create parameter.
Note
Amplify only has access to the keys under the
/amplify/{your_app_id}/{your_backend_environment_name} for the
specific environment build. You must specify the default AWS KMS key to allow
Amplify to decrypt the value.
Access environment secrets
Accessing an environment secret during a build is similar to accessing environment variables, except that
environment secrets are stored in process.env.secrets as a JSON
string.
Amplify environment secrets
Specify an Systems Manager parameter in the format
/amplify/{your_app_id}/{your_backend_environment_name}/AMPLIFY_SIWA_CLIENT_ID.
You can use the following environment secrets that are accessible by default within the Amplify console.
| Variable name | Description | Example value |
|---|---|---|
|
AMPLIFY_SIWA_CLIENT_ID |
The Sign in with Apple client ID |
|
|
AMPLIFY_SIWA_TEAM_ID |
The Sign in with Apple team ID |
|
|
AMPLIFY_SIWA_KEY_ID |
The Sign in with Apple key ID |
|
|
AMPLIFY_SIWA_PRIVATE_KEY |
The Sign in with Apple private key |
-----BEGIN PRIVATE KEY----- ****...... -----END PRIVATE KEY----- |