Create trails in additional accounts
You can use the console or the AWS CLI to create trails in additional AWS accounts and aggregate their log files to one Amazon S3 bucket. Alternatively, you could create an organization trail to log all AWS accounts that are part of an organization in AWS Organizations. For more information, see Creating a trail for an organization.
Using the console to create trails in additional AWS accounts
You can use the CloudTrail console to create trails in additional accounts.
-
Sign in to AWS Management Console with the account for which you want to create a trail. Follow the steps in Creating a trail with the console to create a trail using the console.
-
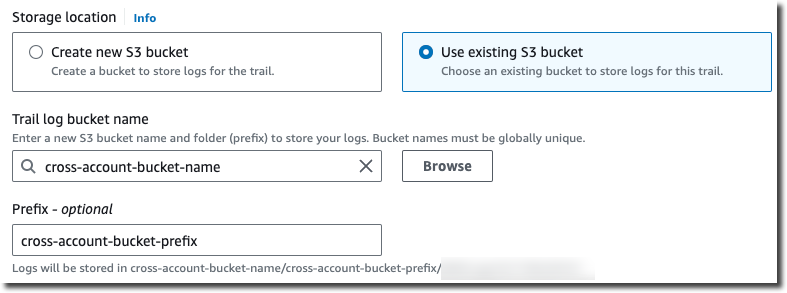
For Storage location, choose Use existing S3 bucket. Use the text box to enter the name of the bucket you're using to store log files across accounts.
Note
The bucket policy must grant CloudTrail permission to write to it. For information about manually editing the bucket policy, see Setting bucket policy for multiple accounts.
-
For Prefix, enter the prefix you are using to store log files across accounts. If you choose to use a prefix that is different from what you specified in your bucket policy, you must edit the bucket policy on your destination bucket to allow CloudTrail to write log files to your bucket using this new prefix.
Using the CLI to create a trail in additional AWS accounts
You can use the AWS command line tools to create trails in additional accounts and aggregate their log files to one Amazon S3 bucket. For more information about these tools, see cloudtrail in the AWS CLI Command Reference.
Create a trail by using the create-trail command, specifying the following:
-
--namespecifies the name of the trail. -
--s3-bucket-namespecifies the Amazon S3 bucket you are using to store log files across accounts. -
--s3-prefixspecifies a prefix for the log file delivery path (optional). -
--is-multi-region-trailspecifies that this trail will log events in all AWS Regions in the partition in which you are working.
You can create one trail for each Region in which an account is running AWS resources.
The following example command shows how to create a trail for your additional accounts
by using the AWS CLI. To have log files for these account delivered to the bucket you
created in your first account (111111111111 in this example), specify the
bucket name in the --s3-bucket-name option. Amazon S3 bucket names are globally
unique.
aws cloudtrail create-trail --namemy-trail--s3-bucket-nameamzn-s3-demo-bucket--is-multi-region-trail
When you run the command, you will see output similar to the following:
{ "IncludeGlobalServiceEvents": true, "Name": "AWSCloudTrailExample", "TrailARN": "arn:aws:cloudtrail:us-east-2:222222222222:trail/my-trail", "LogFileValidationEnabled": false, "IsMultiRegionTrail": true, "IsOrganizationTrail": false, "S3BucketName": "amzn-s3-demo-bucket" }
For more information about using CloudTrail from the AWS command line tools, see the CloudTrail command line reference.