Test VPC setup with IAM policies
You can further test your VPC that you have set up with Amazon EC2 or WorkSpaces by deploying IAM policies that restrict access.
The following policy denies access to Amazon S3 unless it is using your specified VPC.
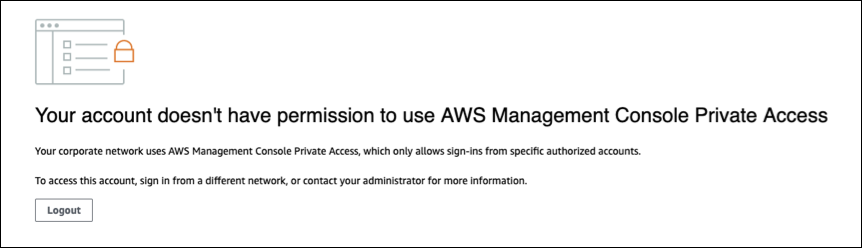
The following policy limits sign in to selected AWS account IDs by using a AWS Management Console Private Access policy for the sign-in endpoint.
If you connect with an identity that does not belong to your account, the following error page is displayed.