Use the solution
Note
Dependencies outside the scope of this solution can impact the account migration between AWS Organizations (for example, quotas for AWS Organizations, resources shared by AWS RAM
Login page
At the email address you provided for the Provide Web UI Login User Email input when you launched the Hub stack, you will receive an email with the subject WebUI Credentials - Account Assessment for AWS Organizations that contains the following:
-
Your temporary login credentials
-
The URL for the web UI
You may alternatively retrieve the web UI URL from the CloudFormation template outputs under "WebUserInterfaceURL".
To add or manage additional users, use the Cognito Service user interface in the AWS Console.
Welcome page
This page displays after you log in. If applicable, it shows your previous scan job status and assessment type for that job.

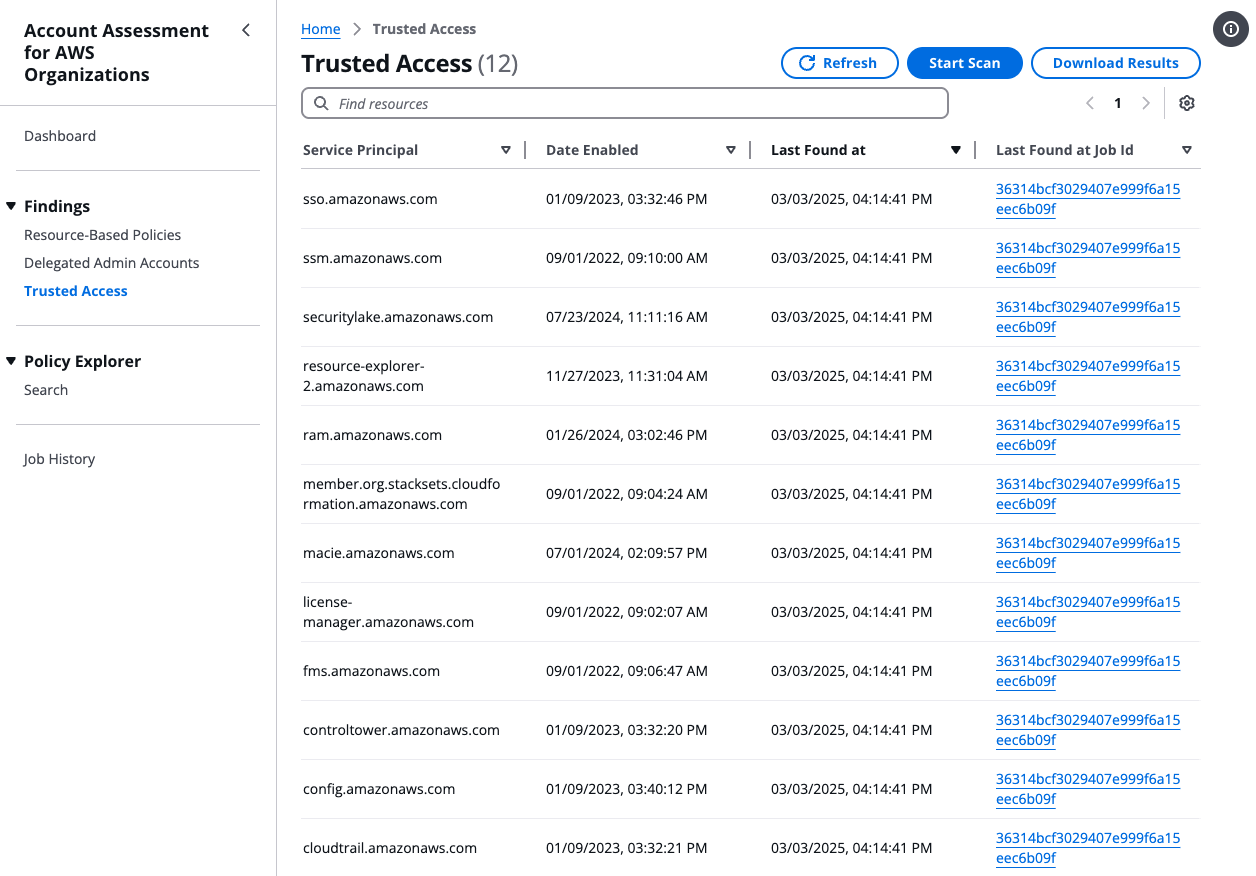
Findings
The left pane lists three types of assessments.
-
Resource-Based Polices (Deprecated, read-only page since v1.1.0)
-
Delegated Admin Accounts
-
Trusted Access
Begin an assessment by selecting Start Scan or download the table content as .csv file by selecting Download Results.
Note
You can run one active scan per assessment type at a time.

Policy Explorer
Beginning with Account Assessment v1.1.0, the Policy Explorer allows you to conduct nuanced searches for policies in your AWS Organization.
Note
Policy Explorer runs a nightly scan for policies across your AWS Organization and stores a string representation of each policy in DynamoDB. Search results you see on the Policy Explorer page are not real-time, but based on the last successful scan. Consult the JobHistory page to find out when the last successful scan was conducted.

You can search for policies
-
By type (Identity Based Policies, Resource Based Policies, Service Control Policies)
-
By region. Use
GLOBALfor region-independent policies -
By principal
-
By action
-
By resource
-
By condition
-
By effect (Allow, Deny or Both)
The matching strategy is string contains, e.g. a search input like us- will match policies in all us regions.
The search criteria is applied server-side. If your search is too broad, and the amount of result data exceeds what the frontend can handle, you will see a message asking you to narrow down the search with additional criteria.
Use the View Policies button to see the full string representation of any policy.

Dependencies on your AWS Organization
A main use case of the "Resource-based Policy Scan" in Account Assessment prior to v1.1.0 was to find policies that contain a condition with the Organization ID, hinting at a policy that may break when the account is moved to a different AWS Organization.
This use case is now covered by PolicyExplorer. To search for Policies that contain your Organizational ID in the condition, press the button Add OrgId which will prepopulate the Condition search input field with your Org ID. Leave all other fields blank.

Job History
The Job History page helps you review the previous scans and their status. The solution provides four status possibilities:
-
ACTIVE – Scan is currently running
-
SUCCEEDED – Scan completed successfully
-
SUCCEEDED_WITH_FAILED_TASKS – Scan completed, but some tasks have errors
-
FAILED – Scan failed
Select the Job ID to view specific findings per job.

When you select the Job ID, the Job Details page displays the findings and any failed tasks during your selected job. You can use this information to help you identify the resource and errors. If the error states that a certain account/region/service/resource could not be scanned, that means that there may be possible findings which the solution was not able to assess. Use your judgement to decide how to proceed.
The AccessDenied error often hints at the fact that the SpokeRole of the Account Assessment solution was not installed in the respective account, so the solution has no permission to access the account in question for a scan.

Next steps
We designed this solution to help you determine specific AWS Organizations dependencies in your underlying resource-based policies. It does not check the validity or correctness of these policies. There are myriad ways in which you can use this data, not limited to common use cases such as consolidating multiple AWS Organizations, preparing for a security audit, or changing your AWS Organization’s management account.
Account migration
One of the common use cases for this solution is to help you plan for migrating your AWS Organizations accounts, such as with a company merger or acquisition. Migrating your accounts requires careful consideration. Specifically, we recommend:
-
Verifying that your policies work as intended before making changes.
-
Using IAM Access Analyzer to verify that your policies achieve your desired permissions.
-
Reviewing and updating the
Conditionpolicy element to meet your security requirements. Do not delete theConditionwithout reviewing the underlying impact. -
Reviewing other dependencies outside the scope of this solution that can impact the account migration between AWS Organizations.
We recommend that you engage with AWS Solutions Architects, Technical Account Managers, and AWS Professional Services to review your AWS Organizations-based dependencies identified by the solution before initiating account migration. Additional resources include the following:
-
How do I move accounts between organizations in AWS Organizations?
– This blog post identifies some of the account, reporting, billing, and other considerations you will need to take when migrating accounts. -
Migrating accounts between AWS Organizations with consolidated billing to all features
– This blog post provides further insights into consolidated billing and account migration.