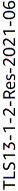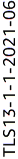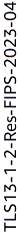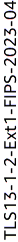TLS listeners for your Network Load Balancer
To use a TLS listener, you must deploy at least one server certificate on your load balancer. The load balancer uses a server certificate to terminate the front-end connection and then to decrypt requests from clients before sending them to the targets. Note that if you need to pass encrypted traffic to the targets without the load balancer decrypting it, create a TCP listener on port 443 instead of creating a TLS listener. The load balancer passes the request to the target as is, without decrypting it.
Elastic Load Balancing uses a TLS negotiation configuration, known as a security policy, to negotiate TLS connections between a client and the load balancer. A security policy is a combination of protocols and ciphers. The protocol establishes a secure connection between a client and a server and ensures that all data passed between the client and your load balancer is private. A cipher is an encryption algorithm that uses encryption keys to create a coded message. Protocols use several ciphers to encrypt data over the internet. During the connection negotiation process, the client and the load balancer present a list of ciphers and protocols that they each support, in order of preference. The first cipher on the server's list that matches any one of the client's ciphers is selected for the secure connection.
Network Load Balancers do not support TLS renegotiation or mutual TLS authentication (mTLS). For mTLS support, create a TCP listener instead of a TLS listener. The load balancer passes the request through as is, so you can implement mTLS on the target.
To create a TLS listener, see Add a listener. For related demos, see TLS Support on Network Load Balancer
Server certificates
The load balancer requires X.509 certificates (server certificate). Certificates are a digital form of identification issued by a certificate authority (CA). A certificate contains identification information, a validity period, a public key, a serial number, and the digital signature of the issuer.
When you create a certificate for use with your load balancer, you must specify a domain name. The domain name on the certificate must match the custom domain name record so that we can verify the TLS connection. If they do not match, the traffic is not encrypted.
You must specify a fully qualified domain name (FQDN) for your certificate, such as
www.example.com or an apex domain name such as example.com.
You can also use an asterisk (*) as a wild card to protect several site names in the
same domain. When you request a wild-card certificate, the asterisk (*) must be in the
leftmost position of the domain name and can protect only one subdomain level. For
instance, *.example.com protects corp.example.com, and
images.example.com, but it cannot protect test.login.example.com.
Also note that *.example.com protects only the subdomains of
example.com, it does not protect the bare or apex domain (example.com).
The wild-card name appears in the Subject field and in the
Subject Alternative Name extension of the certificate. For more
information about public certificates, see Requesting a public certificate in the AWS Certificate Manager User Guide.
We recommend that you create certificates for your load balancers using AWS Certificate Manager (ACM)
Alternatively, you can use TLS tools to create a certificate signing request (CSR), then get the CSR signed by a CA to produce a certificate, then import the certificate into ACM or upload the certificate to AWS Identity and Access Management (IAM). For more information, see Importing certificates in the AWS Certificate Manager User Guide or Working with server certificates in the IAM User Guide.
Supported key algorithms
RSA 1024-bit
RSA 2048-bit
RSA 3072-bit
ECDSA 256-bit
ECDSA 384-bit
ECDSA 521-bit
Default certificate
When you create a TLS listener, you must specify exactly one certificate. This certificate is known as the default certificate. You can replace the default certificate after you create the TLS listener. For more information, see Replace the default certificate.
If you specify additional certificates in a certificate list, the default certificate is used only if a client connects without using the Server Name Indication (SNI) protocol to specify a hostname or if there are no matching certificates in the certificate list.
If you do not specify additional certificates but need to host multiple secure applications through a single load balancer, you can use a wildcard certificate or add a Subject Alternative Name (SAN) for each additional domain to your certificate.
Certificate list
After you create a TLS listener, it has a default certificate and an empty certificate list. You can optionally add certificates to the certificate list for the listener. Using a certificate list enables the load balancer to support multiple domains on the same port and provide a different certificate for each domain. For more information, see Add certificates to the certificate list.
The load balancer uses a smart certificate selection algorithm with support for SNI. If the hostname provided by a client matches a single certificate in the certificate list, the load balancer selects this certificate. If a hostname provided by a client matches multiple certificates in the certificate list, the load balancer selects the best certificate that the client can support. Certificate selection is based on the following criteria in the following order:
-
Hashing algorithm (prefer SHA over MD5)
-
Key length (prefer the largest)
-
Validity period
The load balancer access log entries indicate the hostname specified by the client and the certificate presented to the client. For more information, see Access log entries.
Certificate renewal
Each certificate comes with a validity period. You must ensure that you renew or replace each certificate for your load balancer before its validity period ends. This includes the default certificate and certificates in a certificate list. Renewing or replacing a certificate does not affect in-flight requests that were received by the load balancer node and are pending routing to a healthy target. After a certificate is renewed, new requests use the renewed certificate. After a certificate is replaced, new requests use the new certificate.
You can manage certificate renewal and replacement as follows:
-
Certificates provided by AWS Certificate Manager and deployed on your load balancer can be renewed automatically. ACM attempts to renew certificates before they expire. For more information, see Managed renewal in the AWS Certificate Manager User Guide.
-
If you imported a certificate into ACM, you must monitor the expiration date of the certificate and renew it before it expires. For more information, see Importing certificates in the AWS Certificate Manager User Guide.
-
If you imported a certificate into IAM, you must create a new certificate, import the new certificate to ACM or IAM, add the new certificate to your load balancer, and remove the expired certificate from your load balancer.
Security policies
When you create a TLS listener, you must select a security policy. You can update the security policy as needed. For more information, see Update the security policy.
Considerations:
-
The
ELBSecurityPolicy-TLS13-1-2-2021-06policy is the default security policy for TLS listeners created using the AWS Management Console.-
We recommend the
ELBSecurityPolicy-TLS13-1-2-2021-06security policy, which includes TLS 1.3, and is backwards compatible with TLS 1.2.
-
-
The
ELBSecurityPolicy-2016-08policy is the default security policy for TLS listeners created using the AWS CLI. -
You can choose the security policy that is used for front-end connections, but not backend connections.
-
For backend connections, if your TLS listener is using a TLS 1.3 security policy, the
ELBSecurityPolicy-TLS13-1-0-2021-06security policy is used. Otherwise, theELBSecurityPolicy-2016-08security policy is used for backend connections.
-
-
To meet compliance and security standards that require disabling certain TLS protocol versions, or to support legacy clients requiring deprecated ciphers, you can use one of the
ELBSecurityPolicy-TLS-security policies. You can enable access logs for information about the TLS requests sent to your Network Load Balancer, analyze TLS traffic patterns, manage security policy upgrades, and troubleshoot issues. Enable access logging for your load balancer and examine the corresponding access log entries. For more information, see Access Logs and Network Load Balancer Example Queries. -
You can restrict which security policies are available to users across your AWS accounts and AWS Organizations by using the Elastic Load Balancing condition keys in your IAM and service control policies (SCPs), respectively. For more information, see Service control policies (SCPs) in the AWS Organizations User Guide
TLS 1.3 security policies
Note
TLS 1.3 security policies for Network Load Balancers are only supported in the new EC2 experience. When using the old EC2 experience, TLS 1.3 security policies are not available for selection.
Elastic Load Balancing provides the following TLS 1.3 security policies for Network Load Balancers:
-
ELBSecurityPolicy-TLS13-1-2-2021-06(Recommended) -
ELBSecurityPolicy-TLS13-1-2-Res-2021-06 -
ELBSecurityPolicy-TLS13-1-2-Ext1-2021-06 -
ELBSecurityPolicy-TLS13-1-2-Ext2-2021-06 -
ELBSecurityPolicy-TLS13-1-1-2021-06 -
ELBSecurityPolicy-TLS13-1-0-2021-06 -
ELBSecurityPolicy-TLS13-1-3-2021-06
FIPS security policies
The Federal Information Processing Standard (FIPS) is a US and Canadian
government standard that specifies the security requirements for cryptographic
modules that protect sensitive information. To learn more, see Federal Information Processing Standard (FIPS) 140
All FIPS policies leverage the AWS-LC FIPS validated cryptographic module. To learn more,
see the
AWS-LC Cryptographic Module
Elastic Load Balancing provides the following FIPS security policies for Network Load Balancer:
-
ELBSecurityPolicy-TLS13-1-3-FIPS-2023-04 -
ELBSecurityPolicy-TLS13-1-2-Res-FIPS-2023-04 -
ELBSecurityPolicy-TLS13-1-2-FIPS-2023-04(Recommended) -
ELBSecurityPolicy-TLS13-1-2-Ext0-FIPS-2023-04 -
ELBSecurityPolicy-TLS13-1-2-Ext1-FIPS-2023-04 -
ELBSecurityPolicy-TLS13-1-2-Ext2-FIPS-2023-04 -
ELBSecurityPolicy-TLS13-1-1-FIPS-2023-04 -
ELBSecurityPolicy-TLS13-1-0-FIPS-2023-04
FS supported policies
Elastic Load Balancing provides the following FS (Forward Secrecy) supported security policies for Network Load Balancers:
-
ELBSecurityPolicy-FS-1-2-Res-2020-10 -
ELBSecurityPolicy-FS-1-2-Res-2019-08 -
ELBSecurityPolicy-FS-1-2-2019-08 -
ELBSecurityPolicy-FS-1-1-2019-08 -
ELBSecurityPolicy-FS-2018-06
TLS 1.0 - 1.2 security policies
Elastic Load Balancing provides the following TLS 1.0 - 1.2 security policies for Network Load Balancers:
-
ELBSecurityPolicy-TLS-1-2-Ext-2018-06 -
ELBSecurityPolicy-TLS-1-2-2017-01 -
ELBSecurityPolicy-TLS-1-1-2017-01 -
ELBSecurityPolicy-2016-08 -
ELBSecurityPolicy-TLS-1-0-2015-04 -
ELBSecurityPolicy-2015-05(identical toELBSecurityPolicy-2016-08)
TLS protocols and ciphers
ALPN policies
Application-Layer Protocol Negotiation (ALPN) is a TLS extension that is sent on the initial TLS handshake hello messages. ALPN enables the application layer to negotiate which protocols should be used over a secure connection, such as HTTP/1 and HTTP/2.
When the client initiates an ALPN connection, the load balancer compares the client ALPN preference list with its ALPN policy. If the client supports a protocol from the ALPN policy, the load balancer establishes the connection based on the preference list of the ALPN policy. Otherwise, the load balancer does not use ALPN.
Supported ALPN Policies
The following are the supported ALPN policies:
HTTP1Only-
Negotiate only HTTP/1.*. The ALPN preference list is http/1.1, http/1.0.
HTTP2Only-
Negotiate only HTTP/2. The ALPN preference list is h2.
HTTP2Optional-
Prefer HTTP/1.* over HTTP/2 (which can be useful for HTTP/2 testing). The ALPN preference list is http/1.1, http/1.0, h2.
HTTP2Preferred-
Prefer HTTP/2 over HTTP/1.*. The ALPN preference list is h2, http/1.1, http/1.0.
None-
Do not negotiate ALPN. This is the default.
Enable ALPN Connections
You can enable ALPN connections when you create or modify a TLS listener. For more information, see Add a listener and Update the ALPN policy.