Control instance traffic with firewalls in Lightsail
The firewall in the Amazon Lightsail console acts as a virtual firewall that controls the traffic allowed to connect to your instance through its public IP address. Each instance that you create in Lightsail has two firewalls; one for IPv4 addresses and another for IPv6 addresses. Each firewall contains a set of rules that filter traffic coming into the instance. Both firewalls are independent of each other; you must configure firewall rules separately for IPv4 and IPv6. Edit your instance's firewall, at any time, by adding and deleting rules to allow or restrict traffic.
Lightsail firewalls
Each Lightsail instance has two firewalls; one for IPv4 addresses and another for IPv6 addresses. All internet traffic into and out of your Lightsail instance passes through its firewalls. An instance's firewalls control the internet traffic that is allowed to flow into your instance. However, they don't control the traffic that flows out of it—the firewalls allow all outbound traffic. Edit your instance's firewalls, at any time, by adding and deleting rules to allow or restrict incoming traffic. Note that both firewalls are independent of each other; you must configure firewall rules separately for IPv4 and IPv6.
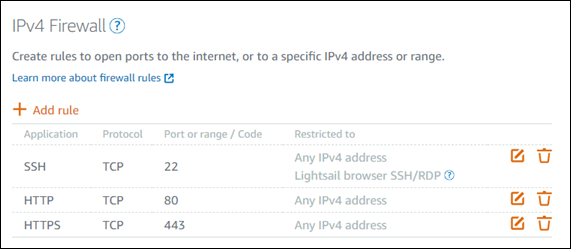
Firewall rules are always permissive; you can't create rules that deny access. You add rules to your instance's firewalls to allow traffic to reach your instance. When you add a rule to your instance's firewall, you specify the protocol to use, the port to open, and the IPv4 and IPv6 addresses that are allowed to connect to your instance, as shown in the following example (for IPv4). You can also specify an application layer protocol type, which is a preset that specifies the protocol and port range for you based on the service that you plan to use on your instance.
Important
Firewall rules affect only traffic that flows in through the public IP address of an instance. It does not affect traffic that flows in through the private IP address of an instance, which can originate from Lightsail resources in your account, in the same AWS Region, or resources in a peered virtual private cloud (VPC), in the same AWS Region.
Firewall rules, and their configurable parameters are explained in the next few sections of this guide.
Create firewall rules
Create a firewall rule to enable a client to establish a connection with your instance, or with an application running on your instance. For example, to enable all web browsers to connect to the WordPress application on your instance, you configure a firewall rule that enables the Transmission Control Protocol (TCP) over port 80 from any IP address. If this rule is already configured on your instance's firewall, then you can delete it to block web browsers from being able to connect to the WordPress application on your instance.
Important
You can use the Lightsail console to add up to 30 source IP addresses at a time. To add up to 60 IP addresses at a time, use the Lightsail API, AWS Command Line Interface (AWS CLI), or an AWS SDK. This quota is enforced separately for IPv4 rules and IPv6 rules. For example, a firewall can have 60 inbound rules for IPv4 traffic and 60 inbound rules for IPv6 traffic. We recommend you consolidate individual IP addresses into CIDR ranges. For more information, see the Specify source IP addresses section of this guide.
You can also enable an SSH client to connect to your instance, to perform administrative tasks on the server, by configuring a firewall rule that enables TCP over port 22 only from the IP address of the computer that needs to establish a connection. In this case, you would not want to allow any IP address to establish an SSH connection to your instance; since doing so could lead to a security risk on your instance.
Note
The firewall rule examples described in this section may exist in your instance's firewall by default. For more information, see Default firewall rules later in this guide.
If there is more than one rule for a specific port, we apply the most permissive rule. For example, if you add a rule that allows access to TCP port 22 (SSH) from IP address 192.0.2.1. Then, you add another rule that allows access to TCP port 22 from everyone. As a result, everyone has access to TCP port 22.
Specify protocols
A protocol is the format in which data is transmitted between two computers. Lightsail allows you to specify the following protocols in a firewall rule:
-
Transmission Control Protocol (TCP) is primarily used for establishing and maintaining a connection between clients and the application running on your instance, until the exchange of data is complete. It is a widely used protocol, and one which you might often specify in your firewall rules. TCP guarantees that no transmitted data is missing, and that all of the data that's sent makes it to the intended recipient. It is ideal use is for network applications that need high reliability, and for which transmission time is relatively less critical, such as web browsing, financial transactions, and text messaging. These use-cases will lose significant value if parts of the data is lost.
-
User Datagram Protocol (UDP) is primarily used for establishing low-latency and loss-tolerating connections between clients and the application running on your instance. It is ideal use is for network applications in which perceived latency is critical, such as gaming, voice, and video communications. These use-cases can suffer some data loss without adversely affecting perceived quality.
-
Internet Control Message Protocol (ICMP) is primarily used to diagnose network communication issues, such as to determine if data is reaching its intended destination in a timely manner. It is ideal use is for the Ping utility, which you can use to test the speed of the connection between your local computer and your instance. It reports how long it takes data to reach your instance and come back to your local computer.
Note
When you add an ICMP rule to the IPv6 firewall of your instance using the Lightsail console, the rule is automatically configured to use ICMPv6. For more information, see Internet Control Message Protocol for IPv6
on Wikipedia. -
All is used to allow all protocol traffic to flow into your instance. Specify this protocol when you're unsure which protocol to specify. This includes all internet protocols; not just the ones specified above. For more information, see Protocol Numbers
on the Internet Assigned Numbers Authority website.
Specifying ports
Similar to physical ports on your computer, which allow your computer to communicate with peripherals like your keyboard and mouse, network ports serve as internet communications endpoints for your instance. When a computer seeks to connect with your instance, it will expose a port to establish the communication.
The ports that you can specify in a firewall rule can range from 0 to 65535. When you create a firewall rule to enable a client to establish a connection with your instance, you specify the protocol that will be used (covered earlier in this guide), and the port numbers through which the connection can be established. You can also specify the IP addresses that are allowed to establish a using the protocol and port; this is covered in the next section of this guide.
Here are some of the commonly used ports along with the services that use them:
-
Data transfer over File Transfer Protocol (FTP) uses port 20.
-
Command control over FTP uses port 21.
-
Secure Shell (SSH) uses port 22.
-
Telnet remote login service, and unencrypted text messages uses port 23.
-
Simple Mail Transfer Protocol (SMTP) email routing uses port 25.
Important
To enable SMTP on your instance, you must also configure reverse DNS for your instance. Otherwise, your email might be limited over TCP port 25. For more information, see Configuring reverse DNS for an email server on your Amazon Lightsail instance.
-
Domain Name System (DNS) service uses port 53.
-
Hypertext Transfer Protocol (HTTP) used by web browsers to connect to websites uses port 80.
-
Post Office Protocol (POP3) used by email clients to retrieve email from a server uses port 110.
-
Network News Transfer Protocol (NNTP) uses port 119.
-
Network Time Protocol (NTP) uses port 123.
-
Internet Message Access Protocol (IMAP) used to manage digital mail uses port 143.
-
Simple Network Management Protocol (SNMP) uses port 161.
-
HTTP Secure (HTTPS) HTTP over TLS/SSL used by web browsers to establish an encrypted connection to websites uses port 443.
For more information, see Service Name and Transport Protocol Port Number Registry
Specify application layer protocol types
You can specify an application layer protocol type when you create a firewall rule, which are presets that specify the rule's protocol and port range for you based on the service that you want to enable on your instance. This way, you don't have to search for the common protocol and ports to use for services like SSH, RDP, HTTP, and others. You can simply choose those application layer protocol types, and the protocol and port is specified for you. If you prefer to specify your own protocol and port, then you can choose the Custom rule application layer protocol type, which gives you control of those parameters.
Note
You can specify the application layer protocol type only by using the Lightsail console. You cannot specify the application layer protocol type using the Lightsail API, AWS Command Line Interface (AWS CLI), or SDKs.
The following application layer protocol types are available in the Lightsail console:
-
Custom – Choose this option to specify your own protocol and ports.
-
All protocols – Choose this option to specify all protocols, and specify your own ports.
-
All TCP – Choose this option to use the TCP protocol but you're unsure of which port to open. This enables the TCP over all ports (0-65535).
-
All UDP – Choose this option to use the UDP protocol but you're unsure of which port to open. This enables the UDP over all ports (0-65535).
-
All ICMP – Choose this option to specify all ICMP types and codes.
-
Custom ICMP – Choose this option to use the ICMP protocol and define an ICMP type and code. For more information about ICMP types and codes, see Control Messages
on Wikipedia. -
DNS – Choose this option when you want to enable DNS on your instance. This enables TCP and UDP over ports 53.
-
HTTP – Choose this option when you want to enable web browsers to connect to a website that is hosted on your instance. This enables TCP over port 80.
-
HTTPS – Choose this option when you want to enable web browsers to establish an encrypted connection to a website that is hosted on your instance. This enables TCP over port 443.
-
MySQL/Aurora – Choose this option to enable a client to connect to a MySQL or Aurora database hosted on your instance. This enables TCP over port 3306.
-
Oracle-RDS – Choose this option to enable a client to connect to an Oracle or RDS database hosted on your instance. This enables TCP over port 1521.
-
Ping (ICMP) – Choose this option to enable your instance to respond to requests using the Ping utility. On the IPv4 firewall, this enables ICMP type 8 (echo) and code -1 (all codes). On the IPv6 firewall, this enables ICMP type 129 (echo reply) and code 0.
-
RDP – Choose this option to enable an RDP client to connect to your instance. This enables TCP over port 3389.
-
SSH – Choose this option to enable an SSH client to connect to your instance. This enables TCP over port 22.
Specify source IP addresses
By default, firewall rules allow all IP addresses to connect to your instance through the specified protocol and port. This is ideal for traffic such as web browsers over HTTP and HTTPS. However, this poses a security risk for traffic such as SSH and RDP, since you would not want to allow all IP addresses to be able to connect to your instance using those applications. For that reason, you can choose to restrict a firewall rule to an IPv4 or IPv6 address or range of IP addresses.
-
For the IPv4 firewall - You can specify a single IPv4 address (for example, 203.0.113.1), or a range of IPv4 addresses. In the Lightsail console, the range can be specified using a dash (for example, 192.0.2.0-192.0.2.255) or in CIDR block notation (for example, 192.0.2.0/24). For more information about CIDR block notation, see Classless Inter-Domain Routing
on Wikipedia. -
For the IPv6 firewall - You can specify a single IPv6 address (for example, 2001:0db8:85a3:0000:0000:8a2e:0370:7334), or a range of IPv6 addresses. In the Lightsail console, the IPv6 range can be specified using only CIDR block notation (for example, 2001:db8::/32). For more information about IPv6 CIDR block notation, see IPv6 CIDR blocks
on Wikipedia.
Default Lightsail firewall rules
When you create a new instance, its IPv4 and IPv6 firewalls are preconfigured with the following set of default rules that allow basic access to your instance. The default rules are different depending on the type of instance that you create. These rules are listed as application, protocol, port, and source IP address (for example, application - protocol - port - source IP address).
- AlmaLinux, Amazon Linux 2, Amazon Linux 2023, CentOS, Debian, FreeBSD, openSUSE, and Ubuntu (base operating systems)
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
- WordPress, Ghost, Joomla!, PrestaShop, and Drupal (CMS applications)
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
HTTPS - TCP - 443 - all IP addresses
- cPanel & WHM (CMS application)
-
SSH - TCP - 22 - all IP addresses
DNS (UDP) - UDP - 53 - all IP addresses
DNS (TCP) - TCP - 53 - all IP addresses
HTTP - TCP - 80 - all IP addresses
HTTPS - TCP - 443 - all IP addresses
Custom - TCP - 2078 - all IP addresses
Custom - TCP - 2083 - all IP addresses
Custom - TCP - 2087 - all IP addresses
Custom - TCP - 2089 - all IP addresses
- LAMP, Django, Node.js, MEAN, GitLab, and Nginx (development stacks)
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
HTTPS - TCP - 443 - all IP addresses
- Magento (eCommerce application)
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
HTTPS - TCP - 443 - all IP addresses
- Redmine (project management application)
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
HTTPS - TCP - 443 - all IP addresses
- Plesk (hosting stack)
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
HTTPS - TCP - 443 - all IP addresses
Custom - TCP - 53 - all IP addresses
Custom - UDP - 53 - all IP addresses
Custom - TCP - 8443 - all IP addresses
Custom - TCP - 8447 - all IP addresses
- Windows Server 2022, Windows Server 2019, and Windows Server 2016
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
RDP - TCP - 3389 - all IP addresses
- SQL Server Express 2022, SQL Server Express 2019, and SQL Server Express 2016
-
SSH - TCP - 22 - all IP addresses
HTTP - TCP - 80 - all IP addresses
RDP - TCP - 3389 - all IP addresses