Data and transport security with AWS IoT Core for LoRaWAN
AWS IoT Core for LoRaWAN uses the following methods to secure the data and communication between LoRaWAN devices, gateways, and AWS IoT Core for LoRaWAN:
-
The security best practices that devices follow when communicating with LoRaWAN gateways, as described in the whitepaper LoRaWAN Security
. -
The security that AWS IoT Core uses to connect gateways to AWS IoT Core for LoRaWAN and send the data to other AWS services. For more information, see data protection in AWS IoT Core.
How data is secured throughout the system
This diagram identifies the key elements in a LoRaWAN system connected to AWS IoT Core for LoRaWAN to identify how data is secured throughout.
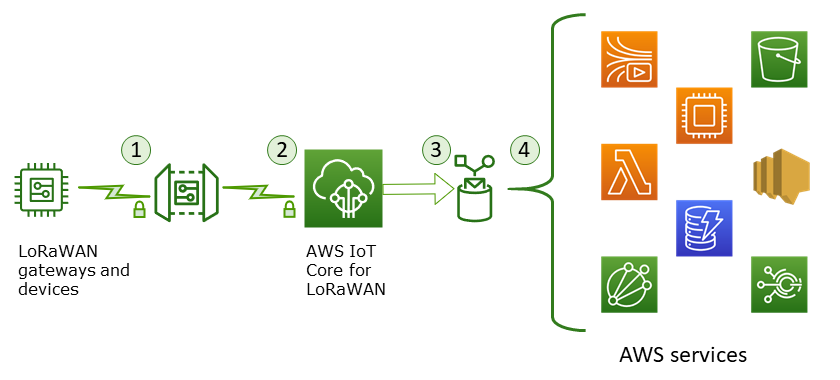
-
The LoRaWAN wireless device encrypts its binary messages using AES128 CTR mode before it transmits them.
-
Gateway connections to AWS IoT Core for LoRaWAN are secured by TLS as described in Transport security in AWS IoT. AWS IoT Core for LoRaWAN decrypts the binary message and encodes the decrypted binary message payload as a base64 string.
-
The resulting base64-encoded message is sent as the message payload to the AWS IoT rule described in the destination assigned to the device. Data within AWS is encrypted using AWS-owned keys.
-
The AWS IoT rule directs the message data to the services described in the rule's configuration. Data within AWS is encrypted using AWS-owned keys.
LoRaWAN device and gateway transport security
LoRaWAN devices and AWS IoT Core for LoRaWAN store pre-shared root keys. Session keys are derived by both LoRaWAN devices and AWS IoT Core for LoRaWAN following the protocols. The symmetric session keys are used for encryption and decryption in a standard AES-128 CTR mode. A 4-byte message integrity code (MIC) is also used to check the data integrity following a standard AES-128 CMAC algorithm. The session keys can be updated by using the Join/Rejoin process.
The security practice for LoRa gateways is described in the LoRaWAN
specifications. LoRa gateways connect to AWS IoT Core for LoRaWAN through a web socket using a
Basics StationBasics
Station version 2.0.4 and later.
Before the web socket connection is established, AWS IoT Core for LoRaWAN uses the TLS Server
and Client Authentication mode to authenticate the gateway. To ensure the
confidentiality of the LoRaWAN protocol, TLS
AWS IoT Core for LoRaWAN also maintains a Configuration and Update Server (CUPS) that configures and updates the certificates and keys used for TLS authentication.