Forensic investigation and reporting service
The diagram below represents the logical interaction view of forensic memory and disk investigation service. Once forensic acquisition is completed, forensic investigation flow is initiated, isolation of EC2 instance or EKS cluster is done based on the AWS Security Hub event type.
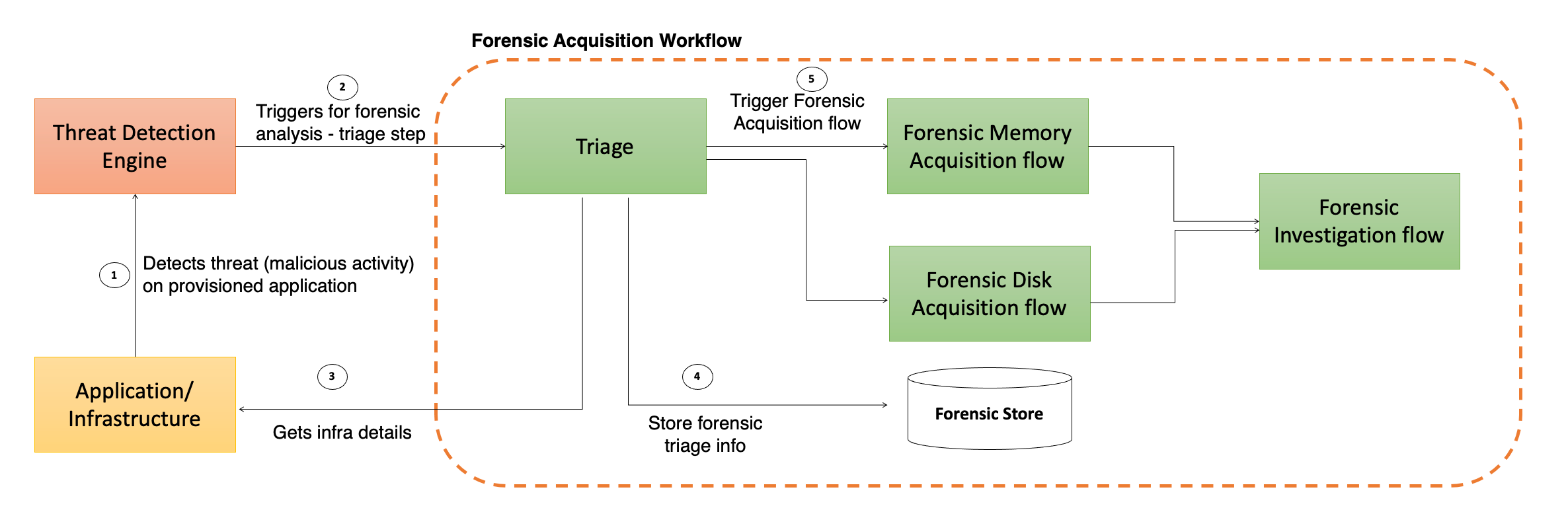
Interaction view
Forensic investigation and reporting service - interaction view
Implementation view
Forensic investigation and reporting service
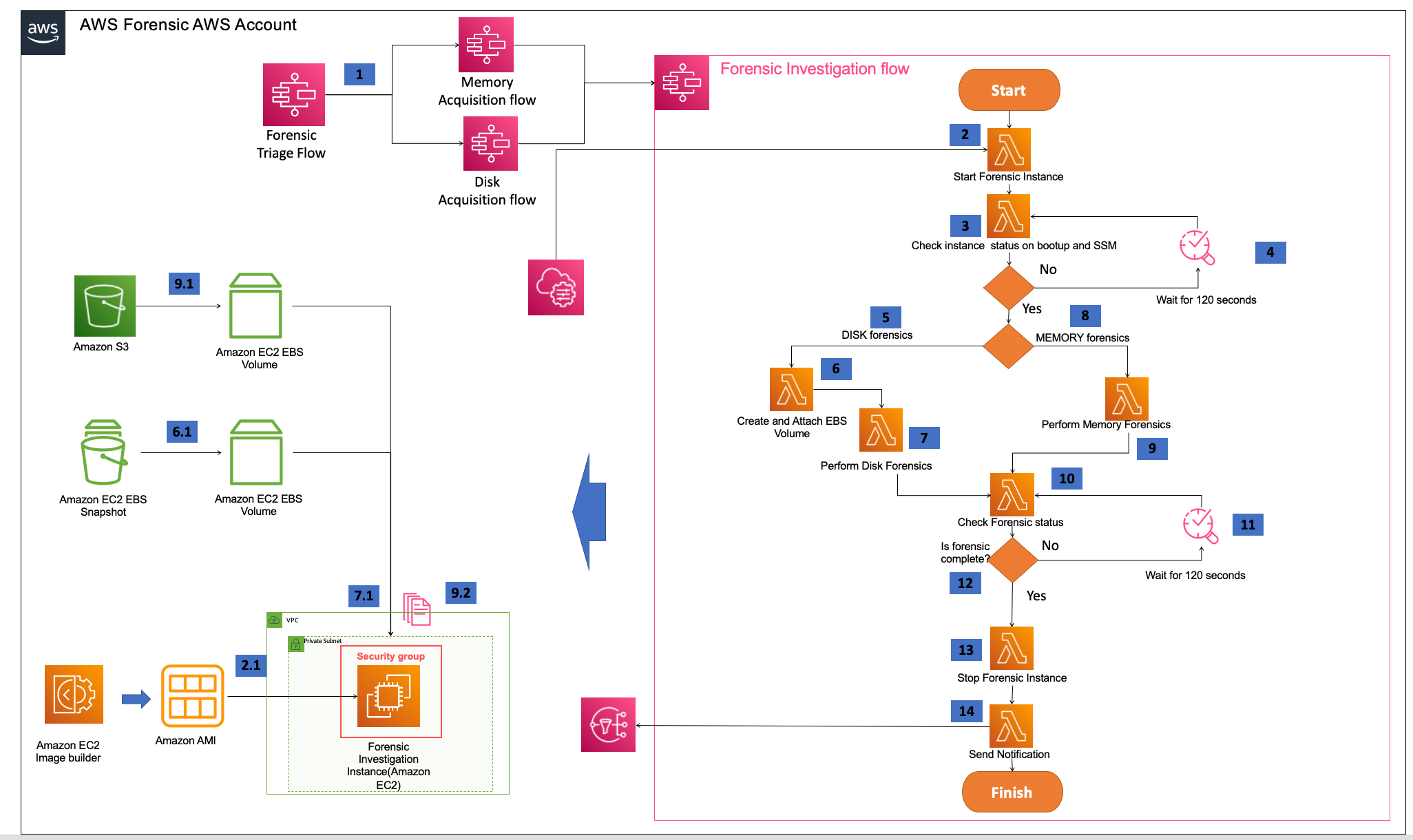
Forensic investigation and reporting workflow
-
After the acquisition flow, the investigation flow (Step Functions) is initiated.
-
The Create Instance Lambda function retrieves the AMI information from AWS Systems Manager Parameter Store and starts an instance in the forensic account.
-
The Check Instance Lambda function validates the instance has the necessary tools required for forensic investigation, such as determining the instance is in the running state, AWS Systems Manager is installed and forensic tools are up and running.
-
If the response from SSM Command is
PendingorIn Progressit waits for 120 seconds and checks again. -
Disk forensics investigation flow is initiated for forensictype variable set to
DISK. -
Disk forensics investigation lambda function creates a volume from the snapshot shared with the forensic account and attaches the volume to the instance started in step 2.
-
The Disk forensics investigation Lambda function leverages the SSM document to perform disk forensics.
-
The Memory forensics investigation flow is initiated for forensictype variable set to
MEMORY. -
The Lambda function leverages the SSM document to load memory dump from S3 to the EBS volume for memory analysis.
-
The SSM document containing details of the forensic investigation is initiated to perform disk or memory forensics.
-
The Memory forensics flow retrieves the appropriate meta data tag associated with the memory dump and loads the matching kernel Volatility symbol table from a configurable S3 location.
-
-
The Lambda function checks if AWS Systems Manager Run Command is complete.
-
The Lambda function waits for 120 seconds before checking again if AWS Systems Manager Run Command is complete.
-
Once complete, the Terminate Forensic Instance Lambda function is initiated.
-
The forensic instance is terminated.
-
Details about forensic ID, compromised Amazon EC2 instance or EKS cluster, Amazon S3 bucket location of the results, and Amazon DynamoDB table details about disk and memory analysis are sent as SNS.