インフラストラクチャドメインのインシデント
インフラストラクチャドメインには、通常、アプリケーションのデータやネットワークに関連するアクティビティが含まれます。VPC 内の Amazon EC2 インスタンスへのトラフィックや、Amazon EC2 インスタンスのオペレーティングシステムで実行しているプロセスなどが該当します。
例えば、モニタリングソリューションから Amazon EC2 インスタンスの潜在的なセキュリティ異常の通知を受けたとします。この問題に対処する一般的な手順は次のとおりです。
-
環境を変更する前に、Amazon EC2 インスタンスからメタデータをキャプチャします。
-
インスタンスの終了保護を有効にして、Amazon EC2 インスタンスを誤って終了しないように保護します。
-
VPC セキュリティグループを切り替えて Amazon EC2 インスタンスを隔離します。ただし、VPC 接続の追跡やその他の封じ込め手法
に注意してください。 -
Amazon EC2 インスタンスをあらゆる AWS Auto Scaling
グループからデタッチします。 -
関連する Elastic Load Balancing
サービスから Amazon EC2 インスタンスの登録を解除します。 -
EC2 インスタンスにアタッチされた Amazon EBS データボリュームのスナップショットを作成し、保存とフォローアップ調査を行います。
-
Amazon EC2 インスタンスに対して調査のために隔離済みとしてタグ付けし、調査に関連するトラブルチケットなど、関連するメタデータを追加します。
上記のすべてのステップは、AWS API、AWS SDK、AWS CLI、AWS Management Console を使用して実行できます。これらの方法を使用して AWS とやり取りするには、IAM サービスを使用して AWS リソースへのアクセスを安全にコントロールできます。IAM を使用して、アカウントレベルでリソースの使用を許可するために誰を認証および認可するかを制御します。IAM サービスは、お客様がこれらのアクションを実行し、サービスドメインとやり取りするための認証と認可を提供します。
Amazon EBS ボリュームのスナップショットは、EBS データボリュームの特定の時点におけるブロックレベルのコピーです。非同期のコピーであり、完了までに時間がかかる場合がありますが、特定の時点の前と後の差分となります。これらのコピーから新しい EBS ボリュームを作成して、フォレンジック EC2 インスタンスにマウントし、フォレンジック調査員がオフラインで詳細に分析できます。次の図は、簡略化した結果です。すべてのネットワークコンポーネント (サブネット、ルーティングテーブル、ネットワークアクセスコントロールリストなど) を網羅しているわけではありません。
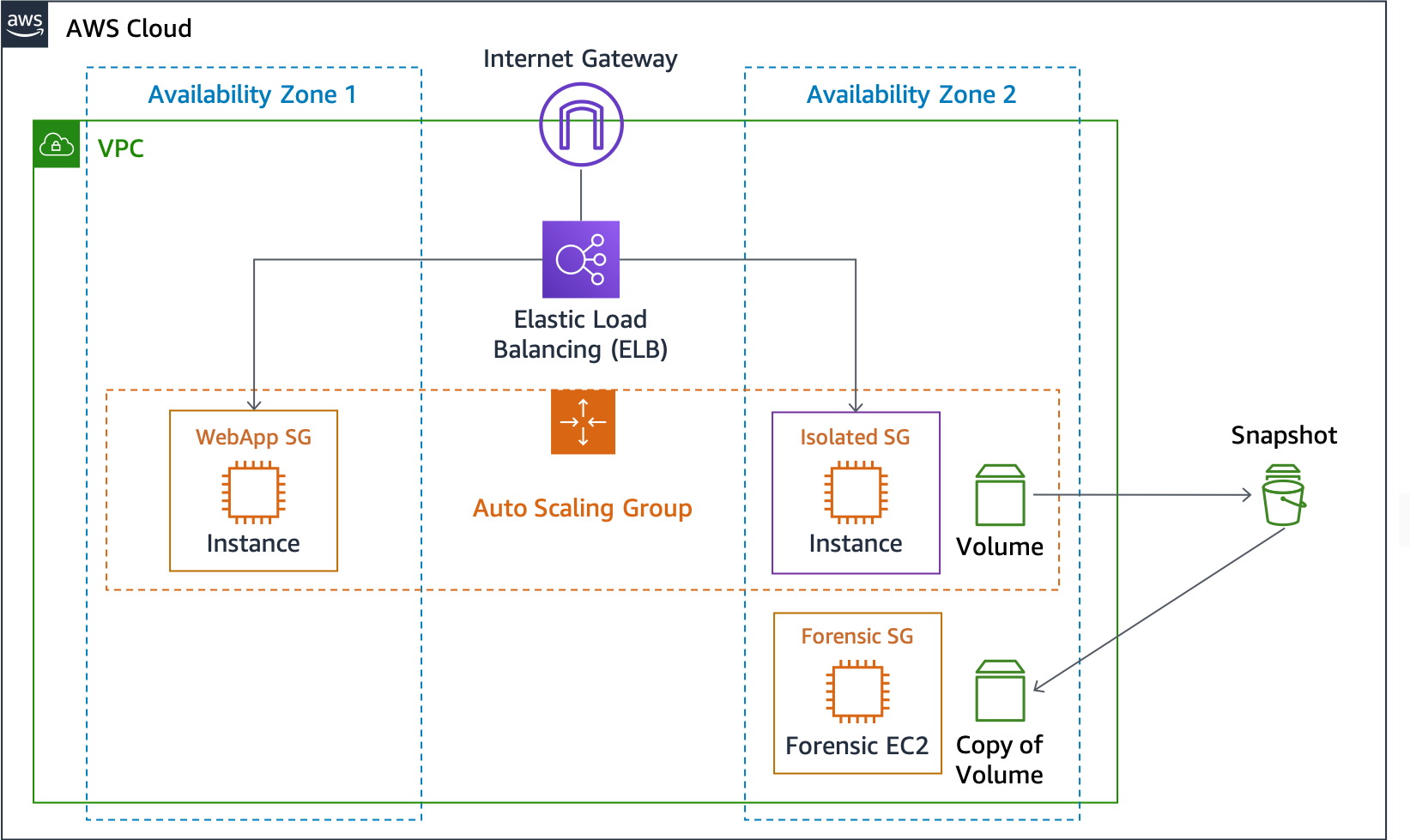
図 6: EC2 インスタンスの分離とスナップショット