This whitepaper is for historical reference only. Some content might be outdated and some links might not be available.
Security
Create a secure, high-performing, and resilient foundation for your cloud environment. The capabilities within this area enable you to design and implement security policies and controls across different levels of the stack to protect your resources from external or internal vulnerabilities and threats. They ensure confidentiality, availability, integrity, and usability, while providing priorities and advice to assist with remediation.
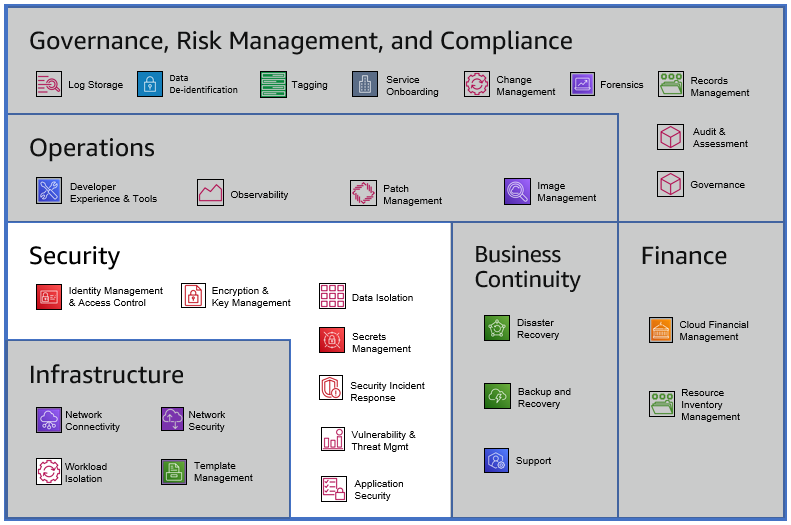
Security Category
Security capabilities include:
-
Identity Management & Access Control helps you build and monitor permissions in your environment. Use this capability to structure access to your resources within defined isolated groups following the principal of least privilege (PoLP). This capability will help your team develop a framework to manage your environment and provide access to your services.
-
Data Isolation enables you to limit access to data at rest and in transit so that data is only accessible to appropriate and authorized entities. This capability also includes the ability to detect misuse and/or unauthorized access, leak, and theft of data.
-
Application Security enables the protection of application software, and the detection of anomalous behavior in the context of the applications’ interactions with customers. Threats to be addressed include unauthorized access, privilege escalation, and other application-level threats typically characterized in threat frameworks.
-
Encryption and Key Management enables you to implement a key management strategy. This includes the ability to encrypt data at rest and in transit, provide least privileged access to keys, report on anomalies, and rotate keys based on requirements.
-
Secrets Management enables you to manage secrets such as passwords, access keys, other API keys, X.509, or SSH private keys. This capability includes storage, access control, access logging, revocation, and rotation aspects for managing secrets.
-
Security Incident Response enables you to effectively respond to a security incident based on decisions specified in policy. The response involves characterizing the nature of the incident and making changes (which may involve activities including restoration of operational status, identification and remediation of root cause, and gathering evidence pursuant to civil or criminal prosecution).
-
Vulnerability & Threat Management is the ability to identify vulnerabilities that can affect the environment (availability, performance, or security). This capability enables you to assess the impact and scope (such as blast radius) of vulnerabilities and threats, and address/remediate them.