Amazon EBS volume encryption
Amazon EBS offers volume encryption capability. Each volume is encrypted using AES-256-XTS
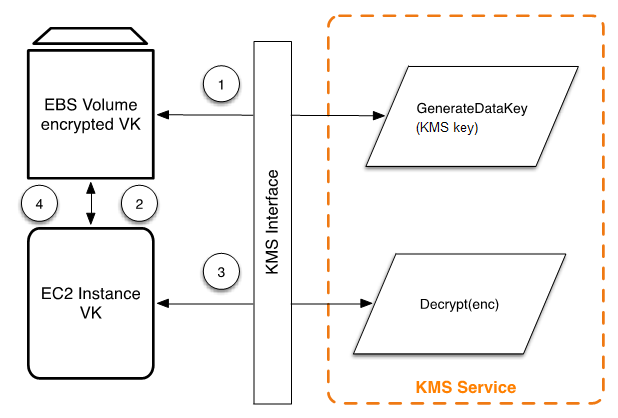
The following workflow encrypts data that is being written to an Amazon EBS volume:
-
Amazon EBS obtains an encrypted volume key under a KMS key through AWS KMS over a TLS session and stores the encrypted key with the volume metadata.
-
When the Amazon EBS volume is mounted, the encrypted volume key is retrieved.
-
A call to AWS KMS over TLS is made to decrypt the encrypted volume key. AWS KMS identifies the KMS key and makes an internal request to an HSM in the fleet to decrypt the encrypted volume key. AWS KMS then returns the volume key back to the Amazon Elastic Compute Cloud (Amazon EC2) host that contains your instance over the TLS session.
-
The volume key is used to encrypt and decrypt all data going to and from the attached Amazon EBS volume. Amazon EBS retains the encrypted volume key for later use in case the volume key in memory is no longer available.
For more information about encrypting Amazon EBS volumes with KMS keys, see How Amazon Elastic Block Store uses AWS KMS in the AWS Key Management Service Developer Guide and Amazon EBS encryption in the Amazon EC2 User Guide and Amazon EC2 User Guide.