Securing workloads with public endpoints
For workloads that are accessible publicly, AWS provides a number of features and services that can help mitigate certain risks. This section covers authentication and authorization of application users and protecting API endpoints.
Authentication and authorization
Authentication relates to identity and authorization refers to actions. Use authentication to control who can invoke a Lambda function, and then use authorization to control what they can do. For many applications, IAM is sufficient for managing both control mechanisms.
For applications with external users, such as web or mobile applications, it is common to use
JSON Web Tokens
You can
implement JWTs with Amazon Cognito, a user directory service that can handle registration, authentication,
account recovery, and other common account management operations.
Amplify Framework
Given the critical security role of an identity provider service, it’s important to use professional tooling to safeguard your application. It’s not recommended that you write your own services to handle authentication or authorization. Any vulnerabilities in custom libraries may have significant implications for the security of your workload and its data.
Protecting API endpoints
For serverless applications, the preferred way to serve a backend application publicly is to use Amazon API Gateway. This can help you protect an API from malicious users or spikes in traffic.
API Gateway offers two endpoint types for serverless developers: REST APIs and HTTP APIs. Both support authorization using AWS Lambda, IAM, or Amazon Cognito. When using IAM or Amazon Cognito, incoming requests are evaluated and if they are missing a required token or contain invalid authentication, the request is rejected. You are not charged for these requests and they do not count towards any throttling quotas.
Unauthenticated API routes may be accessed by anyone on the public internet so it’s recommended that you
limit the use of unauthenticated APIs. If you must use unauthenticated APIs, it’s important to protect these
against common risks, such as
denial-of-service
In many cases, the functionality provided by unauthenticated API can be achieved with an alternative approach. For example, a web application may provide a list of customer retail stores from a DynamoDB table to users who are not logged in. This request may originate from a frontend web application or from any other source that calls the URL endpoint. This diagram compares three solutions:
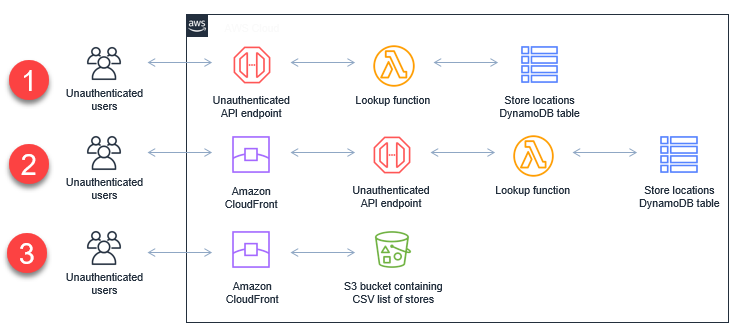
-
This unauthenticated API can be called by anyone on the internet. In a denial of service attack, it’s possible to exhaust API throttling limits, Lambda concurrency, or DynamoDB provisioned read capacity on an underlying table.
-
A CloudFront distribution in front of the API endpoint with an appropriate time-to-live (TTL) configuration would absorb most of the traffic in a DoS attack, without changing the underlying solution for fetching the data.
-
Alternatively, for static data that rarely changes, the CloudFront distribution could serve the data' from an Amazon S3 bucket.