Cyber threat intelligence architecture on AWS
The following figure depicts a generalized architecture for using a threat feed to integrate cyber threat intelligence (CTI) into your AWS environment. The CTI is shared between your threat intelligence platform in the AWS Cloud, the selected cyber authority, and other trust community members.
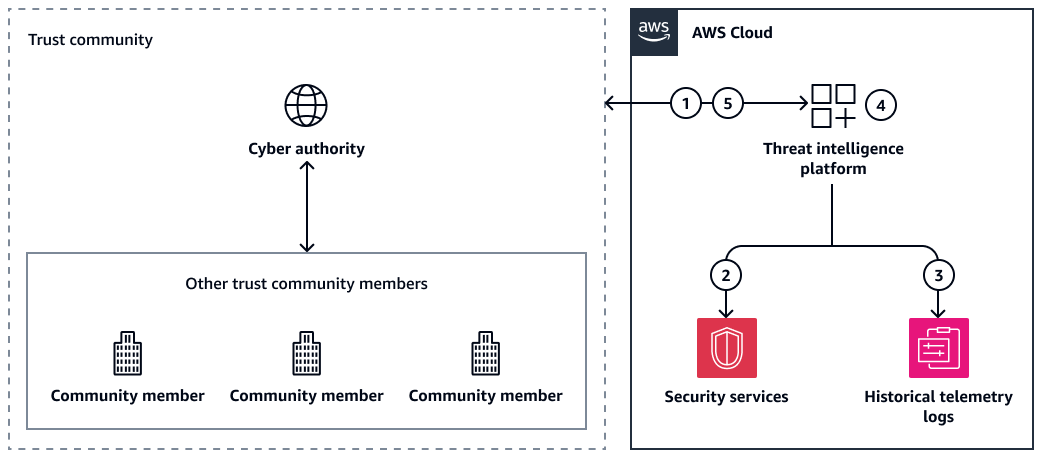
It shows the following workflow:
-
The threat intelligence platform receives actionable CTI from the cyber authority or from other trust community members.
-
The threat intelligence platform tasks AWS security services to detect and prevent events.
-
The threat intelligence platform receives threat intelligence from AWS services.
-
If an event occurs, the threat intelligence platform curates new CTI.
-
The threat intelligence platform shares the new CTI with the cyber authority. It can also share the CTI with other trust community members.
There are many cyber authorities that offer CTI feeds. Examples include the Australian Cyber Security Centre (ACSC)
To get started with CTI sharing, we recommend that you do the following:
-
Deploying a threat intelligence platform – Deploy a platform that ingests, aggregates and organizes threat intelligence data from multiple sources and in different formats.
-
Ingesting cyber threat intelligence – Integrate your threat intelligence platform with one or more threat feed providers. When you're receiving a threat feed, use your threat intelligence platform to process the new CTI and identify the actionable intelligence that is relevant to the security operations in your environment. Automate as much as possible, but there are some situations that require a human-in-the-loop decision.
-
Automating preventative and detective security controls – Deploy CTI to security services in your architecture that provide preventative and detective controls. These services are commonly known as intrusion prevention systems (IPS). On AWS, you use service APIs to configure block lists that deny access from the IP addresses and domain names provided in the threat feeds.
-
Gaining visibility with observability mechanisms – While security operations take place in your environment, you are collecting new CTI. For example, you might observe a threat that was included in the threat feed, or you might observe indicators of compromise associated with an intrusion (such as a zero-day exploit). Centralizing threat intelligence provides increased situational awareness across your environment, so that you can review existing CTI and newly discovered CTI in one system.
-
Sharing CTI with your trust community – To complete the CTI sharing life cycle, generate your own CTI and share it back into your trust community.
The following video, Scaling cyber
threat intelligence sharing with the AUS Cyber Security Center