Generate a static outbound IP address using a Lambda function, Amazon VPC, and a serverless architecture
Created by Thomas Scott (AWS)
Environment: Production | Technologies: Containers & microservices; Software development & testing | AWS services: AWS Lambda |
Summary
This pattern describes how to generate a static outbound IP address in the Amazon Web Services (AWS) Cloud by using a serverless architecture. Your organization can benefit from this approach if it wants to send files to a separate business entity by using Secure File Transfer Protocol (SFTP). This means that the business entity must have access to an IP address that allows files through its firewall.
The pattern’s approach helps you create an AWS Lambda function that uses an Elastic IP address as the outbound IP address. By following the steps in this pattern, you can create a Lambda function and a virtual private cloud (VPC) that routes outbound traffic through an internet gateway with a static IP address. To use the static IP address, you attach the Lambda function to the VPC and its subnets.
Prerequisites and limitations
Prerequisites
An active AWS account.
AWS Identity and Access Management (IAM) permissions to create and deploy a Lambda function, and to create a VPC and its subnets. For more information about this, see Execution role and user permissions in the AWS Lambda documentation.
If you plan to use infrastructure as code (IaC) to implement this pattern’s approach, you need an integrated development environment (IDE) such as AWS Cloud9. For more information about this, see What is AWS Cloud9? in the AWS Cloud9 documentation.
Architecture
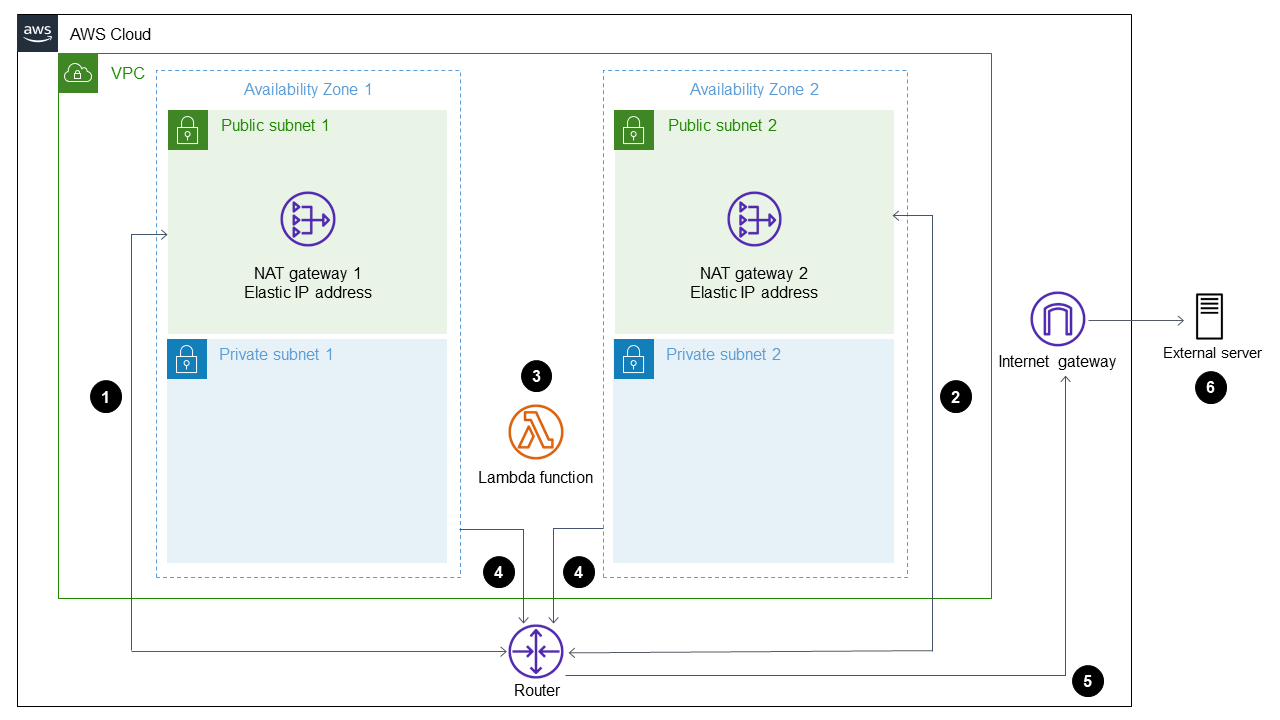
The following diagram shows the serverless architecture for this pattern.
The diagram shows the following workflow:
Outbound traffic leaves NAT gateway 1 in Public subnet 1.
Outbound traffic leaves NAT gateway 2 in Public subnet 2.
The Lambda function can run in Private subnet 1 or Private subnet 2.
Private subnet 1 and Private subnet 2 route traffic to the NAT gateways in the public subnets.
The NAT gateways send outbound traffic to the internet gateway from the public subnets.
Outbound data is transferred from the internet gateway to the external server.
Technology stack
Automation and scale
You can ensure high availability (HA) by using two public and two private subnets in different Availability Zones. Even if one Availability Zone becomes unavailable, the pattern’s solution continues to work.
AWS Lambda – AWS Lambda is a compute service that supports running code without provisioning or managing servers. Lambda runs your code only when needed and scales automatically, from a few requests per day to thousands per second. You pay only for the compute time that you consume—there is no charge when your code is not running.
Amazon VPC – Amazon Virtual Private Cloud (Amazon VPC) provisions a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you've defined. This virtual network closely resembles a traditional network that you'd operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
Epics
| Task | Description | Skills required |
|---|
| Create a new VPC. | Sign in to the AWS Management Console, open the Amazon VPC console, and then create a VPC named Lambda VPC that has 10.0.0.0/25 as the IPv4 CIDR range. For more information about creating a VPC, see Getting started with Amazon VPC in the Amazon VPC documentation. | AWS administrator |
| Task | Description | Skills required |
|---|
| Create the first public subnet. | On the Amazon VPC console, choose Subnets and then choose Create Subnet. For Name tag, enter public-one. For VPC, choose Lambda VPC. Choose an Availability Zone and record it. For IPv4 CIDR block, enter 10.0.0.0/28 and then choose Create subnet.
| AWS administrator |
| Create the second public subnet. | On the Amazon VPC console, choose Subnets and then choose Create Subnet. For Name tag, enter public-two. For VPC, choose Lambda VPC. Choose an Availability Zone and record it. Important: You cannot use the Availability Zone that contains the public-one subnet. For IPv4 CIDR block, enter 10.0.0.16/28 and then choose Create subnet.
| AWS administrator |
| Task | Description | Skills required |
|---|
| Create the first private subnet. | On the Amazon VPC console, choose Subnets and then choose Create Subnet. For Name tag, enter private-one. For VPC, choose Lambda VPC. Choose the Availability Zone that contains the public-one subnet that you created earlier. For IPv4 CIDR block, enter 10.0.0.32/28 and then choose Create subnet.
| AWS administrator |
| Create the second private subnet. | On the Amazon VPC console, choose Subnets and then choose Create Subnet. For Name tag, enter private-two. For VPC, choose Lambda VPC. Choose the same Availability Zone that contains the public-two subnet that you created earlier. For IPv4 CIDR block, enter 10.0.0.64/28 and then choose Create subnet.
| AWS administrator |
| Task | Description | Skills required |
|---|
| Create the first Elastic IP address. | On the Amazon VPC console, choose Elastic IPs and then choose Allocate new address. Choose Allocate and record the Allocation ID for your newly created Elastic IP address.
Note: This Elastic IP address is used for your first NAT gateway. | AWS administrator |
| Create the second Elastic IP address. | On the Amazon VPC console, choose Elastic IPs and then choose Allocate new address. Choose Allocate and record the Allocation ID for this second Elastic IP address.
Note: This Elastic IP address is used for your second NAT gateway. | AWS administrator |
| Task | Description | Skills required |
|---|
| Create an internet gateway. | On the Amazon VPC console, choose Internet Gateways and then choose Create internet gateway. Enter Lambda internet gateway as the name and then choose Create internet gateway. Make sure that you record the internet gateway ID.
| AWS administrator |
| Attach the internet gateway to the VPC. | Select the internet gateway that you just created, and then choose Actions, Attach to VPC. | AWS administrator |
| Task | Description | Skills required |
|---|
| Create the first NAT gateway. | On the Amazon VPC console, choose NAT Gateways and then choose Create NAT Gateway. Enter nat-one as the NAT gateway name. Choose public-one as the subnet to create the NAT gateway in. For Connectivity type, choose Public. For Elastic IP allocation ID, choose the first Elastic IP address that you created earlier and associate it with the NAT gateway. Choose Create NAT gateway.
| AWS administrator |
| Create the second NAT gateway. | On the Amazon VPC console, choose NAT Gateways and then choose Create NAT Gateway. Enter nat-two as the NAT gateway name. Choose public-two as the subnet to create the NAT gateway in. For Connectivity type, choose Public. For Elastic IP allocation ID, choose the second Elastic IP address that you created earlier and associate it with the NAT gateway. Choose Create NAT gateway.
| AWS administrator |
| Task | Description | Skills required |
|---|
| Create the route table for the public-one subnet. | On the Amazon VPC console, choose Route Tables and then choose Create route table. Enter public-one-subnet as the route table name and then choose Create route table. Choose the public-one-subnet route table, choose Edit routes, and then choose Add route. Specify 0.0.0.0 in the Destination box and then choose the internet gateway ID in the Target list. On the Subnet associations tab, choose Edit subnet associations, choose the public-one subnet with the 10.0.0.0/28 CIDR range, and then choose Save associations. Choose Save Changes.
| AWS administrator |
| Create the route table for the public-two subnet. | On the Amazon VPC console, choose Route Tables and then choose Create route table. Enter public-two-subnet as the route table name and then choose Create route table. Choose the public-two-subnet route table, choose Edit routes, and then choose Add route. Specify 0.0.0.0 in the Destination box and then choose the internet gateway ID in the Target list. On the Subnet associations tab, choose Edit subnet associations, choose the public-two subnet with the 10.0.0.16/28 CIDR range, and then choose Save associations. Choose Save Changes.
| AWS administrator |
| Create the route table for the private-one subnet. | On the Amazon VPC console, choose Route Tables and then choose Create route table. Enter private-one-subnet as the route table name and then choose Create route table. Choose the private-one-subnet route table, choose Edit routes, and then choose Add route. Specify 0.0.0.0 in the Destination box and then choose the NAT gateway in the public-one subnet in the Target list. On the Subnet associations tab, choose Edit subnet associations, choose the private-onesubnet with the 10.0.0.32/28 CIDR range, and then choose Save associations. Choose Save Changes.
| AWS administrator |
| Create the route table for the private-two subnet. | On the Amazon VPC console, choose Route Tables and then choose Create route table. Enter private-two-subnet as the route table name and then choose Create route table. Choose the private-two-subnet route table, choose Edit routes, and then choose Add route. Specify 0.0.0.0 in the Destination box and then choose the NAT gateway in the public-two subnet in the Target list. On the Subnet associations tab, choose Edit subnet associations, choose the private-two subnet with the 10.0.0.64/28 CIDR range, and then choose Save associations. Choose Save Changes.
| AWS administrator |
| Task | Description | Skills required |
|---|
| Create a new Lambda function. | Open the AWS Lambda console and choose Create function. Under Basic information, enter Lambda test under Function name and then choose the language of your choice under Runtime. Choose Create function.
| AWS administrator |
| Add the Lambda function to your VPC. | On the AWS Lambda console, choose Functions and then choose the function that you created earlier. Choose Configuration and then choose VPC. Choose Edit and then choose Lambda VPC and both private subnets. Choose Default security group for testing purposes and then choose Save.
| AWS administrator |
| Write code to call an external service. | In the programming language of your choice, write code to call an external service that returns your IP address. Verify that the returned IP address matches one of your Elastic IP addresses.
| AWS administrator |
Related resources