Use case: multicloud virtual desktop infrastructure
This use case covers a scenario where you have a virtual desktop infrastructure (VDI) running in another cloud provider that has a private connection to Megaport and is used as an on-ramp to AWS Direct Connect
Using Megaport MCR with AWS Direct Connect gives your VDI users private connectivity to Salesforce Hyperforce. VDI users use their desktops for their daily work, and the VDI provides an on-ramp to AWS Direct Connect by using a Megaport location.
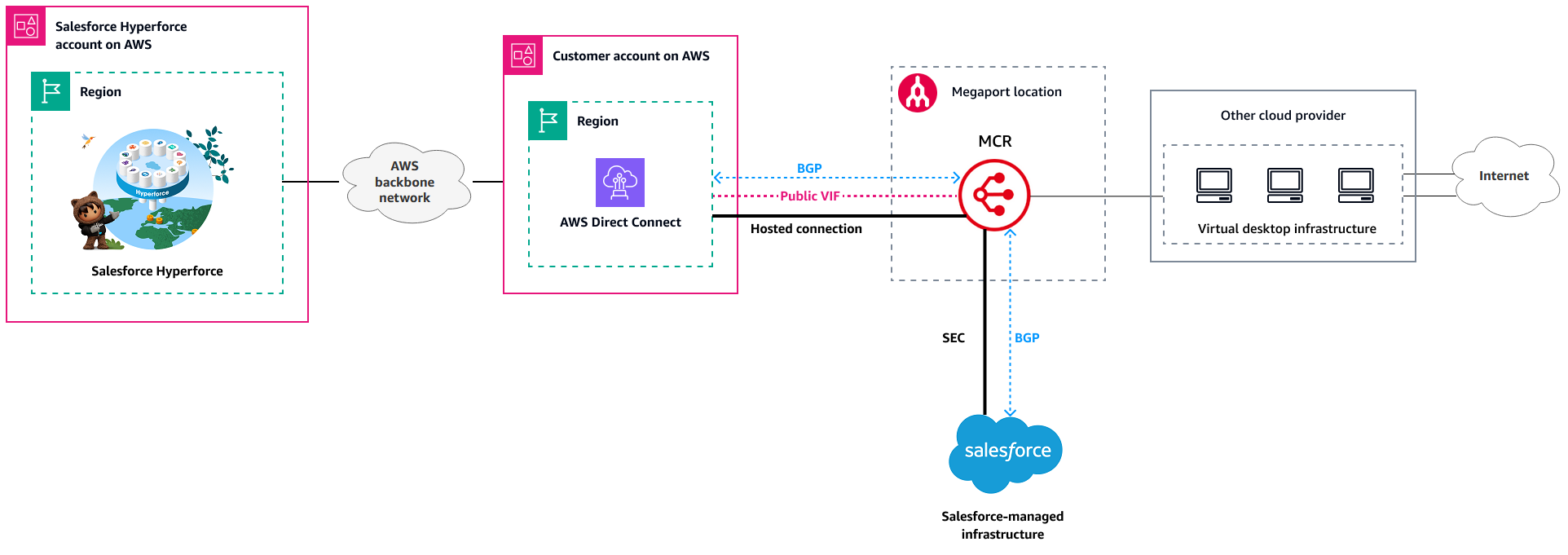
Requirements
-
Users access Salesforce over private network connections.
-
Users use a VDI.
-
The VDI runs in an alternate cloud provider and has a private connection established to Megaport.
-
You own an AWS account to manage the AWS Direct Connect hosted connection with Megaport.
Configuring Megaport MCR with VXC
For step-by-step instructions, see the following Megaport documentation:
Notes
-
The BGP prefixes advertised from your router to AWS are configured in the AWS Management Console when you create the public VIF.
-
The prefixes advertised by AWS Direct Connect must not be advertised beyond the network boundaries of your connection. For example, these prefixes must not be included in any public internet routing table. For more information, see Public virtual interface routing policies in the AWS Direct Connect documentation.
Configuring AWS Direct Connect
Accept a hosted connection
In your AWS account, accept the VXC created previously as a hosted connection. For instructions, see the AWS Direct Connect documentation.
Create a public VIF
In your account, provision a public VIF under the connection you accepted from Megaport. Before you create this VIF, you need to obtain the following:
-
The BGP ASN of the MCR.
-
Public IPv4 addresses for peering (typically
/31CIDR). You can own these or request them from Support. For more information, see Peer IP addresses in the section Prerequisites for virtual interfaces in the AWS Direct Connect documentation.
To create a public VIF, follow the steps in the AWS Direct Connect documentation.
After you create the public VIF, you need to make sure that the BGP authentication key matches both ends of the BGP peer for the peering state to become available.
Note
Using a public VIF to connect to AWS from your on-premises or multicloud
environment changes the way traffic is routed from AWS public prefixes to your
users. We recommend that you use a prefix filter (route map) to make sure that
the accepted Amazon prefixes are limited to the Hyperforce infrastructure and
any other necessary AWS resources. For more information, see Public virtual interface prefix advertisement rules in the AWS Direct Connect
documentation and Hyperforce External IPs
Configuring Megaport MCR with SEC
For step-by-step instructions, see Creating MCR Connections
to Salesforce Express Connect
Configure Salesforce Hyperforce
To enable inbound connections from your corporate network into Salesforce, you
need to configure inbound access to Hyperforce as a security measure. To allow
the required domains