Initiating sign-on from the identity provider (IdP)
| Applies to: Enterprise Edition and Standard Edition |
| Intended audience: System administrators |
Note
IAM identity federation doesn't support syncing identity provider groups with Amazon QuickSight.
In this scenario, your users initiate the sign-on process from the identity provider's portal. After the users are authenticated, they sign in to QuickSight. After QuickSight checks that they are authorized, your users can access QuickSight.
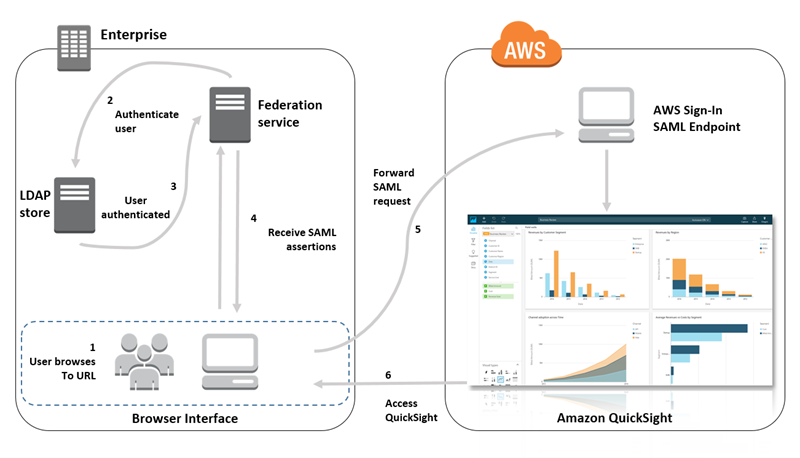
Beginning with a user signing into the IdP, authentication flows through these steps:
-
The user browses to
https://applications.example.comand signs on to the IdP. At this point, the user isn't signed in to the service provider. -
The federation service and the IdP authenticate the user:
-
The federation service requests authentication from the organization's identity store.
-
The identity store authenticates the user and returns the authentication response to the federation service.
-
When authentication is successful, the federation service posts the SAML assertion to the user’s browser.
-
-
The user opens QuickSight:
-
The user's browser posts the SAML assertion to the AWS Sign-In SAML endpoint (
https://signin.aws.amazon.com/saml). -
AWS Sign-In receives the SAML request, processes the request, authenticates the user, and forwards the authentication token to the Amazon QuickSight service.
-
-
Amazon QuickSight accepts the authentication token from AWS and presents QuickSight to the user.
From the user's perspective, the process happens transparently. The user starts at your organization's internal portal and lands at an Amazon QuickSight application portal, without ever having to supply any AWS credentials.
In the following diagram, you can find an authentication flow between Amazon QuickSight and a
third-party identity provider (IdP). In this example, the administrator has set up a
sign-in page to access Amazon QuickSight, called applications.example.com. When a
user signs in, the sign-in page posts a request to a federation service that
complies with SAML 2.0. The end user initiates authentication from the sign-on page
of the IdP.