Install policies and permissions for local Jupyter environments
You will need to set up the necessary permissions and policies to schedule notebook jobs in a local Jupyter environment. The IAM user needs permissions to submit jobs to SageMaker AI and the IAM role that the notebook job itself assumes needs permissions to access resources, depending on the job tasks. The following will provide instructions on how to set up the necessary permissions and policies.
You will need to install two sets of permissions. The following diagram shows the permission structure for you to schedule notebook jobs in a local Jupyter environment. The IAM user needs to set up IAM permissions in order to submit jobs to SageMaker AI. Once the user submits the notebook job, the job itself assumes an IAM role that has permissions to access resources depending on the job tasks.
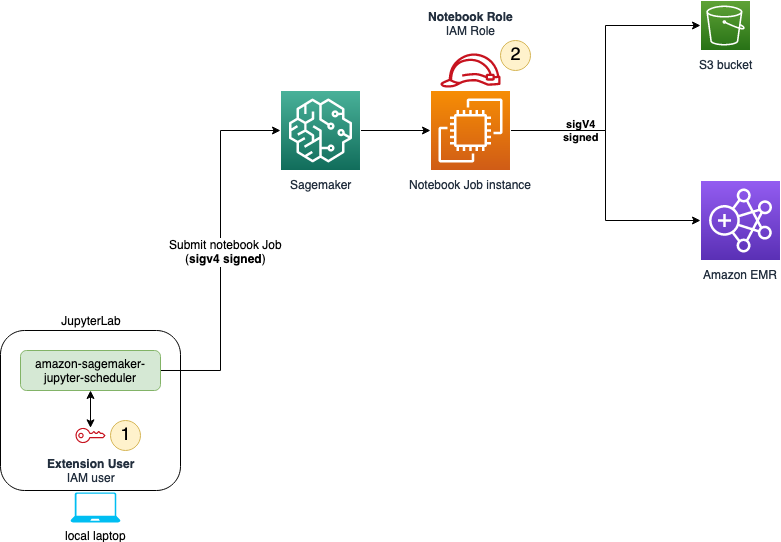
The following sections help you install necessary policies and permissions for both the IAM user and the job execution role.
IAM user permissions
Permissions to submit jobs to SageMaker AI
To add permissions to submit jobs, complete the following steps:
-
Open the IAM console
. -
Select Users in the left panel.
-
Find the IAM user for your notebook job and choose the user name.
-
Choose Add Permissions, and choose Create inline policy from the dropdown menu.
-
Choose the JSON tab.
-
Copy and paste the following policy:
AWS KMS permission policy (optional)
By default, the input and output Amazon S3 buckets are encrypted using server side encryption, but you can specify a custom KMS key to encrypt your data in the output Amazon S3 bucket and the storage volume attached to the notebook job.
If you want to use a custom KMS key, repeat the previous instructions, attaching the following policy, and supply your own KMS key ARN.
Job execution role permissions
Trust relationships
To modify the job execution role trust relationships, complete the following steps:
-
Open the IAM console
. -
Select Roles in the left panel.
-
Find the job execution role for your notebook job and choose the role name.
-
Choose the Trust relationships tab.
-
Choose Edit trust policy.
-
Copy and paste the following policy:
Additional permissions
Once submitted, the notebook job needs permissions to access resources. The following instructions show you how to add a minimal set of permissions. If needed, add more permissions based on your notebook job needs. To add permissions to your job execution role, complete the following steps:
-
Open the IAM console
. -
Select Roles in the left panel.
-
Find the job execution role for your notebook job and choose the role name.
-
Choose Add Permissions, and choose Create inline policy from the dropdown menu.
-
Choose the JSON tab.
-
Copy and paste the following policy:
-
Add permissions to other resources your notebook job accesses.
-
Choose Review policy.
-
Enter a name for your policy.
-
Choose Create policy.