This whitepaper is for historical reference only. Some content might be outdated and some links might not be available.
Smart card authentication requirements
CA certificate requirements
AD Connector requires a CA certificate, which represents the issuer of your user certificates, for smart card authentication. AD Connector matches CA certificates with the certificates presented by your users with their smart cards. Note the following CA certificate requirements:
-
Before you can register a CA certificate, it must be more than 90 days away from expiration.
-
CA certificates must be in Privacy-Enhanced Mail (PEM) format. If you export CA certificates from inside Active Directory, choose
Base64-encoded X.509 (.CER)as the export file format. -
All root and intermediary CA certificates that chain from an issuing CA to user certificates must be uploaded for smart card authentication to succeed.
-
A maximum of 100 CA certificates can be stored per AD Connector directory.
-
AD Connector does not support the
RSASSA-PSSsignature algorithm for CA certificates.
Certificate revocation checking process
To perform smart card authentication, AD Connector must check the revocation status of user certificates using Online Certificate Status Protocol (OCSP). To perform certificate revocation checking, an OCSP responder URL must be internet accessible.
Obtain Department of Defense Certificates
The most current DoD approved external PKI certificate trust chains can be downloaded from the DoD Cyber Exchange website. This zip file contains certificate trust chains for DoD Approved External PKIs. Version 7.3 adds a rekeyed Treasury PKI root and new NASA issuance chain and removes several expired CAs.
-
Open a web browser and navigate to the DoD Cyber Exchange Public Tools and Configuration Files
page. -
Download the latest DoD Approved External PKI Certificate Trust Chains - Version 7.3 under the Tools heading.
-
All DoD certificates have a OCSP responder URL of
http://ocsp.disa.mil.
Alternatively, InstallRoot can extract certificates directly to
PEM format (required for import to AWS Directory Services):
-
Open the InstallRoot application.
-
Choose the Certificate menu option.
-
Choose all installed DoD root and intermediate certificates that are desired for export.
-
Under Export, choose PEM.
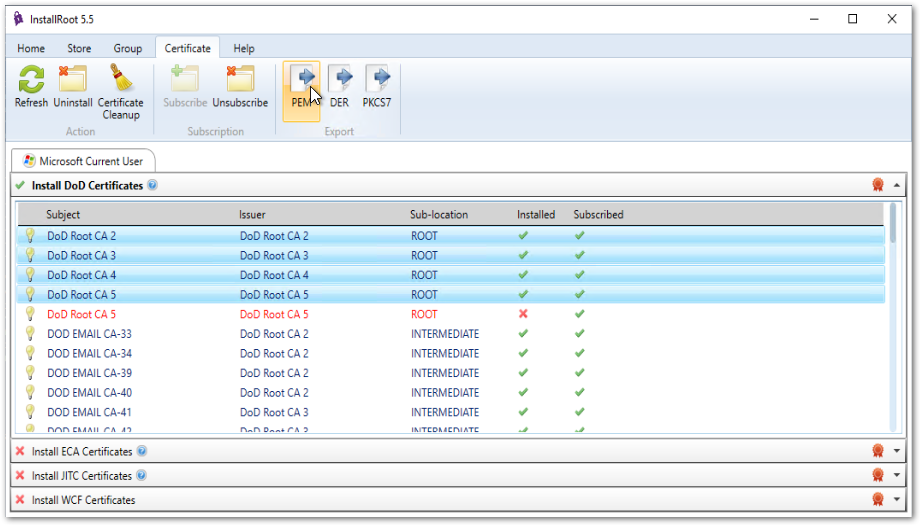
Export root and intermediate certificates with InstallRoot
-
Choose a directory to save the exported certificates, and click OK.