This whitepaper is for historical reference only. Some content might be outdated and some links might not be available.
Centralized Security Management
Many organizations have challenges related to visibility and centralized management of
their environments. As your operational footprint grows, this challenge can be compounded
unless you carefully consider your security designs. Lack of knowledge, combined with
decentralized and uneven management of governance and security processes, can make your
environment vulnerable.
AWS provides tools that help you to address some of the most challenging requirements for
IT management and governance, and tools for supporting a data protection by design
approach.
AWS Control Tower provides a method to set up and govern a new, secure,
multi-account AWS environment. It automates the setup of a landing
zone, which is a multi-account environment that is based on best-practices
blueprints, and enables governance using guardrails that you can choose from a pre-packaged
list. Guardrails implement governance rules for security, compliance, and operations.
AWS Control Tower provides identity management using AWS IAM Identity Center (IAM Identity Center) default directory and
enables cross-account audit using IAM Identity Center and IAM. It also centralizes logs coming from CloudTrail
and AWS Config logs, which are stored in Amazon S3.
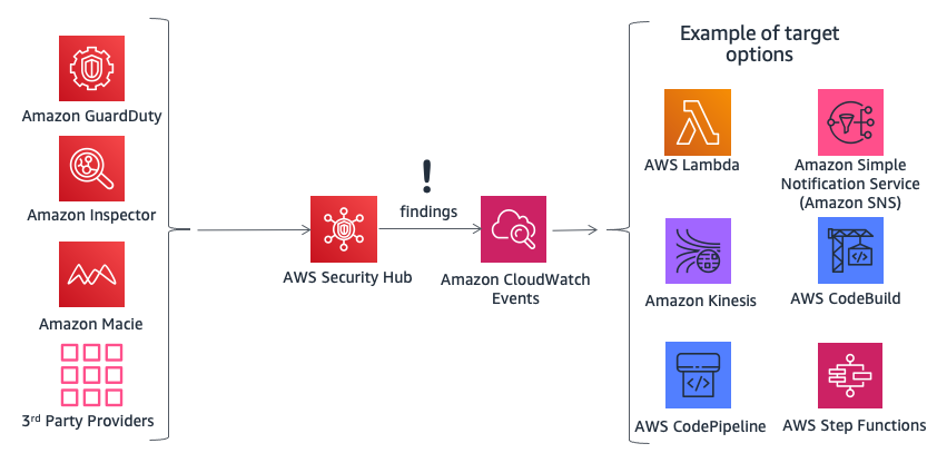
AWS Security Hub is another service that supports centralization and can improve
visibility into an organization. Security Hub centralizes and prioritizes security and
compliance findings from across AWS accounts and services, such as Amazon GuardDuty and Amazon Inspector, and can be integrated with
security software from third-party partners to help you analyze security trends and identify
the highest priority security issues.
Amazon GuardDuty is an intelligent threat detection service that can help
customers more accurately and easily monitor and protect their AWS accounts, workloads, and
data stored in Amazon S3. GuardDuty analyzes billions of events across your AWS accounts from several
sources, including AWS CloudTrail Management Events, CloudTrail Amazon S3 Data Events, Amazon Virtual Private Cloud
Flow Logs, and DNS logs. For example, it detects unusual API calls, suspicious outbound
communications to known malicious IP addresses, or possible data theft using DNS queries as
the transport mechanism. GuardDuty is able to provide more accurate findings by leveraging
machine learning-powered threat intelligence and third-party security partners. GuardDuty Malware Protection helps
you detect the potential presence of malware by scanning the Amazon Elastic Block Store (Amazon EBS) volumes that are attached to
the Amazon Elastic Compute Cloud (Amazon EC2) instances and container workloads. You can include or exclude specific Amazon EC2
instances and container workloads at the time of scanning. You also have an option to retain the
snapshots of Amazon EBS volumes attached to the Amazon EC2 instances or container workloads.
Amazon Inspector is an automated security assessment
service that helps improve the security and compliance of applications deployed on Amazon EC2
instances. Amazon Inspector automatically assesses applications for exposure, vulnerabilities,
and deviations from best practices. After performing an assessment, Amazon Inspector produces
a detailed list of security findings prioritized by level of severity.
Amazon CloudWatch Events enables you to set up
your AWS account to send events to other AWS accounts, or to become a receiver for events from
other accounts or organizations. This mechanism can be very useful for implementing
cross-account incident response scenarios, by taking timely corrective actions (for example,
by calling a Lambda function, or running a command on Amazon EC2 instance) as necessary any time a
security incident event occurs.
Figure 5 – Taking action with AWS Security Hub and Amazon CloudWatch
Events
AWS Organizations helps you centrally manage and govern complex
environments. It enables you to control access, compliance, and security in a multi-account
environment. AWS Organizations supports Service Control Policies (SCPs), which define the AWS service actions available to
use with specific accounts or Organizational Units (OUs) within an organization.
AWS Systems Manager provides you visibility and control of your infrastructure on
AWS. You can view operational data from multiple AWS services from a unified console and
automate operational tasks across them. You can have information about recent API activities,
resource configuration changes, operational alerts, software inventory, and patch compliance
status. Using the integration with other AWS services, you can also take action on resources
depending on your operational needs, to help make your environment in a compliance status.
For example, by integrating Amazon Inspector with AWS Systems Manager, security
assessments are simplified and automated, because you can install Amazon Inspector agent
automatically using Amazon Elastic Compute Cloud Systems Manager when an Amazon EC2 instance is launched. You can also
perform automatic remediations for Amazon Inspector findings by using Amazon EC2 System Manager and
Lambda functions.