This whitepaper is for historical reference only. Some content might be outdated and some links might not be available.
Enable Kerberos Constrained Delegation for the AD Connector Service account
To use smart card authentication with AD Connector, you must enable Kerberos Constrained Delegation (KCD) for the AD Connector Service account to the Lightweight Active Directory Protocol. (LDAP) service in the on-premises AD directory.
Kerberos Constrained Delegation is a feature in Windows Server. This feature enables administrators to specify and enforce application trust boundaries by limiting the scope where application services can act on a user’s behalf. For more information, see Kerberos constrained delegation.
-
Use the
SetSpncommand to set a Service Principal Name (SPN) for the AD Connector service account in the on-premises AD. This enables the service account for delegation configuration. The SPN can be any service or name combination, but not a duplicate of an existing SPN. The-schecks for duplicates. -
Open an elevated command prompt using “Run as administrator”.
-
Run this command:
setspn -s my/spn service_accountThe following figure shows the successful result of running of the
SetSpncommand.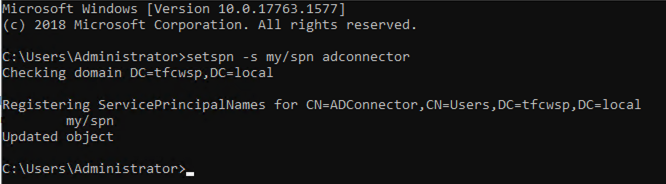
SetSpncommand running -
In AD Users and Computers, right-click on the AD Connector service account and choose Properties.
-
Choose the Delegation tab.
-
Choose the Trust this user for delegation to specified service only and Use any authentication protocol radio buttons.
-
Choose Add, Users or Computers, and then select Advanced.
-
Select Find Now to list all available resources, and then find your domain controller (DC) in the list.
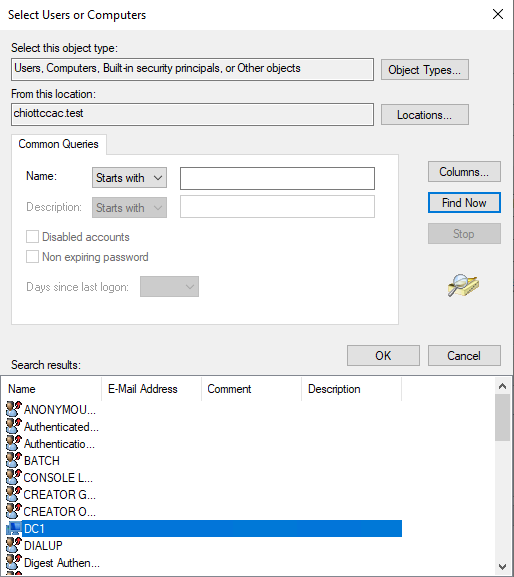 Finding the domain controller in a list of resources
Finding the domain controller in a list of resources -
Select your domain controller and then choose OK to display a list of available services used for delegation.
-
Choose the LDAP service type that has a description of your forest and select OK.
-
Click OK again to save the configuration.
-
Repeat this process for other domain controllers in AD. Alternatively, you can automate the process using PowerShell.