Use encryption with EBS-backed AMIs
AMIs that are backed by Amazon EBS snapshots can take advantage of Amazon EBS encryption. Snapshots of both data and root volumes can be encrypted and attached to an AMI. You can launch instances and copy images with full EBS encryption support included. Encryption parameters for these operations are supported in all Regions where AWS KMS is available.
EC2 instances with encrypted EBS volumes are launched from AMIs in the same way as other instances. In addition, when you launch an instance from an AMI backed by unencrypted EBS snapshots, you can encrypt some or all of the volumes during launch.
Like EBS volumes, snapshots in AMIs can be encrypted by either your default AWS KMS key, or to a customer managed key that you specify. You must in all cases have permission to use the selected KMS key.
AMIs with encrypted snapshots can be shared across AWS accounts. For more information, see Understand shared AMI usage in Amazon EC2.
Encryption with EBS-backed AMIs topics
Instance-launching scenarios
Amazon EC2 instances are launched from AMIs using the RunInstances action with
parameters supplied through block device mapping, either by means of the AWS Management Console or
directly using the Amazon EC2 API or CLI. For more information,
see Block device mappings for volumes on Amazon EC2 instances.
For examples of controlling block device mapping from the AWS CLI,
see Launch, List, and Terminate EC2 Instances.
By default, without explicit encryption parameters, a RunInstances action
maintains the existing encryption state of an AMI's source snapshots while restoring EBS
volumes from them. If encryption by default is enabled, all volumes created from the AMI
(whether from encrypted or unencrypted snapshots) are encrypted. If encryption by
default is not enabled, the instance maintains the encryption state of the AMI.
You can also launch an instance and simultaneously apply a new encryption state to the resulting volumes by supplying encryption parameters. Consequently, the following behaviors are observed:
Launch with no encryption parameters
-
An unencrypted snapshot is restored to an unencrypted volume, unless encryption by default is enabled, in which case all the newly created volumes will be encrypted.
-
An encrypted snapshot that you own is restored to a volume that is encrypted to the same KMS key.
-
An encrypted snapshot that you do not own (for example, the AMI is shared with you) is restored to a volume that is encrypted by your AWS account's default KMS key.
The default behaviors can be overridden by supplying encryption parameters. The
available parameters are Encrypted and KmsKeyId. Setting only
the Encrypted parameter results in the following:
Instance launch behaviors with Encrypted set, but
no KmsKeyId specified
-
An unencrypted snapshot is restored to an EBS volume that is encrypted by your AWS account's default KMS key.
-
An encrypted snapshot that you own is restored to an EBS volume encrypted by the same KMS key. (In other words, the
Encryptedparameter has no effect.) -
An encrypted snapshot that you do not own (i.e., the AMI is shared with you) is restored to a volume that is encrypted by your AWS account's default KMS key. (In other words, the
Encryptedparameter has no effect.)
Setting both the Encrypted and KmsKeyId parameters allows
you to specify a non-default KMS key for an encryption operation. The following behaviors
result:
Instance with both Encrypted and
KmsKeyId set
-
An unencrypted snapshot is restored to an EBS volume encrypted by the specified KMS key.
-
An encrypted snapshot is restored to an EBS volume encrypted not to the original KMS key, but instead to the specified KMS key.
Submitting a KmsKeyId without also setting the Encrypted
parameter results in an error.
The following sections provide examples of launching instances from AMIs using
non-default encryption parameters. In each of these scenarios, parameters supplied to
the RunInstances action result in a change of encryption state during
restoration of a volume from a snapshot.
For information about using the console to launch an instance from an AMI, see Launch an Amazon EC2 instance.
Encrypt a volume during launch
In this example, an AMI backed by an unencrypted snapshot is used to launch an EC2 instance with an encrypted EBS volume.
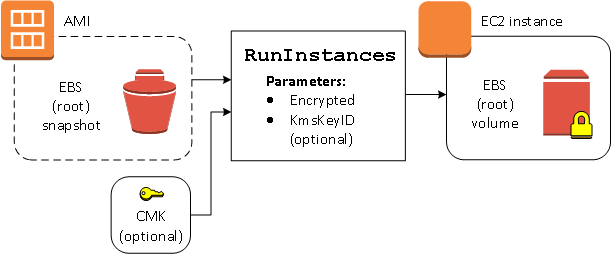
The Encrypted parameter alone results in the volume for this instance
being encrypted. Providing a KmsKeyId parameter is optional. If no KMS key
ID is specified, the AWS account's default KMS key is used to encrypt the volume. To
encrypt the volume to a different KMS key that you own, supply the KmsKeyId
parameter.
Re-encrypt a volume during launch
In this example, an AMI backed by an encrypted snapshot is used to launch an EC2 instance with an EBS volume encrypted by a new KMS key.
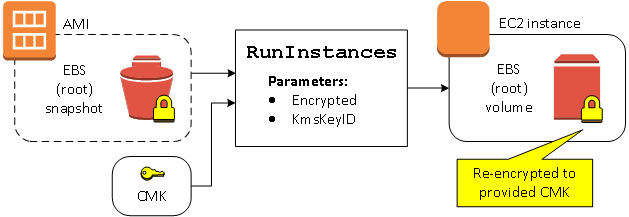
If you own the AMI and supply no encryption parameters, the resulting instance has a volume encrypted by the same KMS key as the snapshot. If the AMI is shared rather than owned by you, and you supply no encryption parameters, the volume is encrypted by your default KMS key. With encryption parameters supplied as shown, the volume is encrypted by the specified KMS key.
Change encryption state of multiple volumes during launch
In this more complex example, an AMI backed by multiple snapshots (each with its own encryption state) is used to launch an EC2 instance with a newly encrypted volume and a re-encrypted volume.
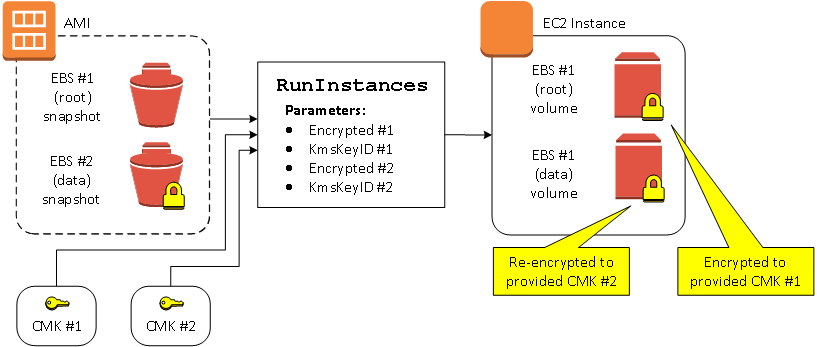
In this scenario, the RunInstances action is supplied with encryption
parameters for each of the source snapshots. When all possible encryption parameters are
specified, the resulting instance is the same regardless of whether you own the
AMI.
Image-copying scenarios
Amazon EC2 AMIs are copied using the CopyImage action, either through the
AWS Management Console or directly using the Amazon EC2 API or CLI.
By default, without explicit encryption parameters, a CopyImage action
maintains the existing encryption state of an AMI's source snapshots during copy. You
can also copy an AMI and simultaneously apply a new encryption state to its associated
EBS snapshots by supplying encryption parameters. Consequently, the following behaviors
are observed:
Copy with no encryption parameters
-
An unencrypted snapshot is copied to another unencrypted snapshot, unless encryption by default is enabled, in which case all the newly created snapshots will be encrypted.
-
An encrypted snapshot that you own is copied to a snapshot encrypted with the same KMS key.
-
An encrypted snapshot that you do not own (that is, the AMI is shared with you) is copied to a snapshot that is encrypted by your AWS account's default KMS key.
All of these default behaviors can be overridden by supplying encryption parameters. The
available parameters are Encrypted and KmsKeyId. Setting only
the Encrypted parameter results in the following:
Copy-image behaviors with Encrypted set, but no
KmsKeyId specified
-
An unencrypted snapshot is copied to a snapshot encrypted by the AWS account's default KMS key.
-
An encrypted snapshot is copied to a snapshot encrypted by the same KMS key. (In other words, the
Encryptedparameter has no effect.) -
An encrypted snapshot that you do not own (i.e., the AMI is shared with you) is copied to a volume that is encrypted by your AWS account's default KMS key. (In other words, the
Encryptedparameter has no effect.)
Setting both the Encrypted and KmsKeyId parameters allows you to
specify a customer managed KMS key for an encryption operation. The following behaviors result:
Copy-image behaviors with both Encrypted and
KmsKeyId set
-
An unencrypted snapshot is copied to a snapshot encrypted by the specified KMS key.
-
An encrypted snapshot is copied to a snapshot encrypted not to the original KMS key, but instead to the specified KMS key.
Submitting a KmsKeyId without also setting the Encrypted parameter
results in an error.
The following section provides an example of copying an AMI using non-default encryption parameters, resulting in a change of encryption state.
For detailed instructions using the console, see Copy an Amazon EC2 AMI.
Encrypt an unencrypted image during copy
In this scenario, an AMI backed by an unencrypted root snapshot is copied to an AMI
with an encrypted root snapshot. The CopyImage action is invoked with
two encryption parameters, including a customer managed key. As a result, the
encryption status of the root snapshot changes, so that the target AMI is backed
by a root snapshot containing the same data as the source snapshot, but encrypted
using the specified key. You incur storage costs for the snapshots in both
AMIs, as well as charges for any instances you launch from either AMI.
Note
Enabling encryption by default has the same effect as setting the Encrypted
parameter to true for all snapshots in the AMI.
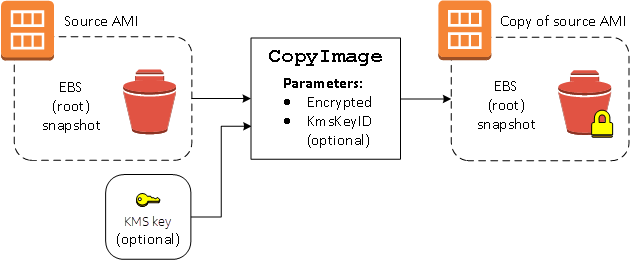
Setting the Encrypted parameter encrypts the single snapshot for this
instance. If you do not specify the KmsKeyId parameter, the default
customer managed key is used to encrypt the snapshot copy.
Note
You can also copy an image with multiple snapshots and configure the encryption state of each individually.