Making authenticated Amazon Q Business API calls using IAM Identity Center
Important
This documentation is for developers building custom applications that integrate with Amazon Q Business APIs. These instructions help you create a trusted backend component in your custom application that can make authenticated API calls on behalf of your users. This is NOT for the built-in Amazon Q Business web experience — that handles authentication automatically through the AWS console.
Amazon Q Business can securely handle data with integrated authentication and authorization. During data ingestion, Amazon Q Business preserves the authorization information—access control lists (ACLs)—from the data source so users can only request answers from the data they already have access to. Through IAM Identity Center, Amazon Q Business uses trusted identity propagation to ensure that an end user is authenticated and receives fine-grained authorization to their user ID and group-based resources.
In order to achieve this, a subset of the Amazon Q Business APIs (Chat, ChatSync, SearchRelevantContent, ListConversations, ListMessages, DeleteConversation, PutFeedback) require identity-aware AWS Sig V4 credentials for the authenticated user on whose behalf the API call is being made.
Note
This page provides an overview of the workflows needed to obtain AWS Sig V4 credentials for a user authenticated using an OIDC-compliant external identity provider (IdP), such as Okta. While we use Okta as an example, the same principles and steps apply to any other identity provider synced with your IAM Identity Center instance.
Architecture overview
The following diagram shows how your custom application components interact with AWS services to make authenticated API calls:
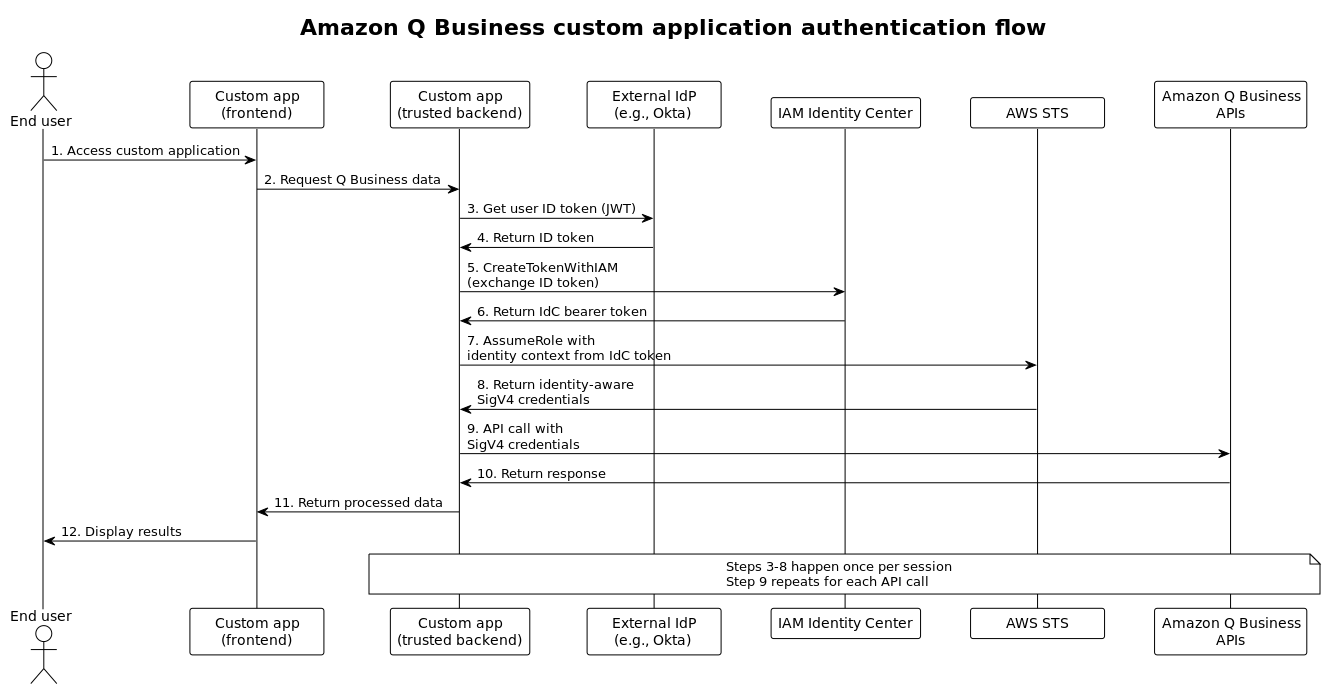
Key components:
-
Custom app frontend: Your user-facing application (web, mobile, etc.)
-
Custom app trusted backend: Your server-side component that handles AWS API calls
-
External IdP: Your identity provider (Okta, Azure AD, etc.)
-
IAM Identity Center: AWS service that manages identity federation
-
Amazon Q Business APIs: The APIs your application calls (
Chat,SearchRelevantContent, etc.)
Note
Your custom application's backend component must implement this authentication flow. End users interact with your frontend, which communicates with your trusted backend to make Amazon Q Business API calls.
Topics
Prerequisites
Before you begin setting up for making Sig V4 authenticated API calls, make sure you've done the following:
-
Created an Okta IdP instance and configured users and groups within it. While we use Okta as an example, the same principles and steps apply to any other OIDC-compliant external identity provider synced with your IAM Identity Center instance.
-
Created an IAM Identity Center instance for your Amazon Q Business application that uses Okta as your as the identity source.
-
Synchronized the users and groups from Okta with IAM Identity Center.
-
Configured access to the AWS CLI.
One-time setup
The following section outlines the steps to set up the Amazon Q Business control plane. You only need to perform these steps once.
-
Create an OIDC app integration
in Okta. -
Then, in the IAM Identity Center instance you have created, create a Trusted Token Issuer to trust IdP issuer with the issuer URL
. For example, https://<your-okta-instance>.okta.com/oauth2/default. -
In your IAM Identity Center instance, create a customer managed custom application using the following AWS CLI command:
aws sso-admin create-application \ --application-provider-arn arn:aws:sso::aws:applicationProvider/custom \ --instance-arnyour-identity-center-arn\ --nameyour-custom-application-name -
Then, disable user assignment or provide explicit user assignments to the custom application you created using the following AWS CLI command:
aws sso-admin put-application-assignment-configuration \ --application-arnyour-custom-application-arn\ --no-assignment-required -
Then, add a JWT bearer grant to your application environment using the put application environment grant CLI command. For example:
aws sso-admin put-application-grant \ --cli-input-json '{ "ApplicationArn":"identity-center-custom-application-arn", "Grant":{ "JwtBearer":{ "AuthorizedTokenIssuers":[ { "AuthorizedAudiences":[ "idp-authorized-audience" ], "TrustedTokenIssuerArn":"trusted-token-issuer-arn" } ] } }, "GrantType":"urn:ietf:params:oauth:grant-type:jwt-bearer" }' -
You will then need to add an authentication method for a Amazon Q Business application environment using the put application environment authentication method AWS CLI command:
aws sso-admin put-application-authentication-method \ --cli-input-json '{ "ApplicationArn": "identity-center-custom-application-arn", "AuthenticationMethod": { "Iam": { "ActorPolicy": { "Version": "2012-10-17", "Statement": [{ "Effect": "Allow", "Principal": { "AWS": "your-aws-account-id", "Service": "qbusiness.amazonaws.com" }, "Action": [ "sso-oauth:CreateTokenWithIAM" ], "Resource": "your-identity-center-custom-application-arn", "Condition": { "ArnEquals": { "aws:SourceArn": "arn:${ArnPartition}:${Service}:${Region}:${AppAccountId}:${Resource}" }, "StringEquals": { "aws:SourceAccount": "${AppAccountId}" } } }] } } }, "AuthenticationMethodType": "IAM" }' -
Next, add a list of authorized targets for an IAM Identity Center access scope for an Amazon Q Business application environment using the following put application environment access scope AWS CLI command:
aws sso-admin put-application-access-scope \ --application-arnidentity-center-custom-application-arn\ --scope "qbusiness:conversations:access" -
Then, create an IAM role that your application environment will use to call AssumeRole API with the following policies:
Trust policy
Permissions policy
-
Then, get the list of synced users and groups in your IAM Identity Center-integrated Amazon Q Business application using the following AWS CLI command:
aws sso-admin list-application-assignments \ --application-arnyour-custom-application-arn -
Finally, add a subscription for each user or group in your IAM Identity Center-integrated Amazon Q Business application using the following AWS CLI commands:
To provision a user subscription
aws qbusiness create-subscription \ --application-idapplication-id\ --principal user=idc-user-id\ --typesubscription-typeTo provision a group subscription
aws qbusiness create-subscription \ --application-idapplication-id\ --principal group=idc-group-id\ --typesubscription-type
Workflow for custom application backend API calls for an authenticated user
After you've completed the one-time setup tasks, you can use one of two workflows to generate identity-aware credentials to make API calls for your IAM Identity Center-integrated Amazon Q Business application:
-
the AWS SDK trusted identity propagation plugin (TIP_ workflow (recommended), or a longer API workflow.
-
The API workflow requires a manual token exchange with IAM Identity Center and uses AWS STS to generate identity-aware credentials for your Amazon Q Business application.
The AWS SDK TIP plugin workflow streamlines the authorization process by eliminating the need for manual token exchange and credential generation. Once set up, it automatically handles token exchange and credential management.
The TIP plugin workflow is the recommended approach for implementing identity-aware authorization. It is currently supported by the Java and JavaScript SDK. For more information, see Trusted identity propagation (TIP) plugin in the AWS SDKs and Tools Reference Guide.
Use the Java or JavaScript SDK to create the plugin and make calls to Amazon Q Business using the following:
-
idToken– The token ID (JWT token). -
ssoClientId– The Amazon Resource Name (ARN) of the custom IAM Identity Center application you created in Step 3 of one-time setup. -
roleArn– The Amazon Resource Name (ARN) of the IAM role you created in Step 8 of one-time setup.
TrustedIdentityPropagationPlugin tipPlugin = TrustedIdentityPropagationPlugin.builder() .webTokenProvider(() -> id token from Okta) .applicationArn(your custom IdC application arn) .accessRoleArn(AccessRoleArn)) .build(); QBusinessClient qbiz = QBusinessClient.builder() .addPlugin(tipPlugin) .build(); qbiz.chatSync(...)
-
First, use the CreateTokenWithIAM API call to obtain an IAM Identity Center-provided JWT bearer grant token using your:
-
clientID: Your IAM Identity Center custom application environment ARN. -
grantType: For example,'urn:ietf:params:oauth:grant-type:jwt-bearer'. -
assertion: The user authenticated ID token obtained from Okta.
-
-
Then, use the AssumeRole API call to obtain user decorated AWS Sig V4 credentials using your:
-
RoleArn: The IAM role ARN. -
RoleSessionName: A unique session name. -
DurationSeconds: The session duration in seconds. -
ProvidedContexts: A list of previously acquired trusted context assertions in the format of a JSON array. The trusted context assertion is signed and encrypted by AWS STS. For example:[{ 'ProviderArn': "arn:aws:iam::aws:contextProvider/IdentityCenter", 'ContextAssertion': claims["sts:identity_context"] }]Note
The
ContextAssertionuses the “sts:identity_context” object from the claims object of the decoded JWT bearer grant token obtained as part of Step 1 in this procedure.
-
-
Use the identity-aware AWS Sig V4 credentials in the previous step to initialize the AWS SDK client and then make Amazon Q Business API calls using that client.
First, set the following environment variables in your command line environment:
AWS_ACCESS_KEY_ID="identity-aware-sigv4-access-key" AWS_SECRET_ACCESS_KEY="identity-aware-sigv4-secret-key" AWS_SESSION_TOKEN="identity-aware-sigv4-session-token"Then, run the following Python script from the same window:
import boto3 import json import random import boto3 aq_client = boto3.client( "qbusiness", region_name="your-aws-region" ) resp = aq_client.chat_sync( applicationId = "amazon-qbusiness-application-id", userMessage = "chat-request", clientToken = str(random.randint(0,10000) ) print(f"Amazon Q Business response: {resp["systemMessage"]}")Important
As a security best practice, the credentials should not be hard coded in your scripts or code. For more information, refer to Boto 3 documentation on using credentials
.