Security OU
The Security OU is a foundational OU. Your security organization should own and manage this OU along with any child OUs and associated accounts.
We recommend that you create the following accounts in the Security OU:
-
Log Archive
-
Security Tooling (Audit)
Note
A default deployment of AWS Control Tower will create a Log Archive and Audit (also referred to as Security Tooling) accounts.
Depending on your initial requirements, you might not need to establish all of these accounts. Refer to Patterns for organizing your AWS accounts for example sets of OUs and accounts that are commonly used in the early stages of adopting AWS.
Log Archive account
The Log Archive is an account that acts as a consolidation point for log data that is gathered from all the accounts in the organization and primarily used by your security, operations, audit, and compliance teams. This account contains a centralized storage location for copies of every account’s audit, configuration compliance, and operational logs. It also provides a storage location for any other audit/compliance logs, as well as application/OS logs. For example, in this account, we recommend that you consolidate AWS API access logs recorded in AWS CloudTrail, logs of changes to AWS resources recorded in AWS Config, and other logs that have security implications. If you use VPC peering between accounts, then you might also benefit from consolidating VPC Flow Logs data in this account. Logs should generally be made directly available for local use by teams working in any account on a shorter-term retention basis. It is common practice to auto-ingest logs from the log archive account into a security information and event management (SIEM) solution.
Note
By utilizing AWS Control Tower for AWS environment management, it automatically enforces best practices, deploying AWS Config and AWS CloudTrail seamlessly across your environment. Their logs are consolidated in an Amazon S3 bucket within the Log Archive account.
Recommended AWS Organization Integrated Service Delegation
| AWS service | Implementation Details | Control Tower Enabled |
|---|---|---|
|
Amazon Security Lake centralizes security data from cloud, on-premises, and custom sources into a data lake that's stored in your account. |
No |
Services in the Log Archive account
With Amazon Security Lake, you can automatically centralize security data from AWS and third-party sources into a data lake that's stored in your Log Archive account. Review Managing access in this account in the following sections to learn how to grant access to the logs from other accounts in your AWS organization.
Logs should be available within the workload account for use by teams on short-term retention basis. It is common practice to auto-ingest logs from the log archive account into a security information and event management (SIEM) solution.
If you are using AWS Control Tower
Operational log data
Operational log data used by your infrastructure, operations, and workload owning teams often overlaps with the log data used by security, audit, and compliance teams.
We recommend that you consolidate your operational log data into the Log Archive account. Based on your specific security and governance requirements, you might need to filter operational log data saved to this account. You might also need to specify who and what has access to the operational log data in the log archive account.
Immutable log data
Log data housed in the Log Archive account is considered immutable in that it is protected from being changed or deleted. Data retention policies and legislation that apply to your organization might also apply to the data in your log archive account.
Managing access to this account
We strongly recommend that you only house log data in this account. By doing so, access to this account can be greatly limited.
Workloads and tools that need to consume the consolidated log data are typically housed in your other accounts and are granted access through read-only IAM roles to access the log data in a read-only, least privileged manner.
Additionally, to ensure log data is properly protected, we recommend SCPs be applied to the Security OU preventing modification or deletion of files within the centralized logging S3 bucket(s). Additionally, the use of S3 bucket versioning provides visibility into the complete history of all log files.
Security Tooling (Audit) account
In the context of AWS services, this account is used to provide centralized delegated admin access to AWS security tooling and consoles, as well as provide view-only access for investigative purposes into all accounts in the organization. The security tooling account should be restricted to authorized security and compliance personnel and related security. This account is an aggregation point (or points for organizations that split the functionality across multiple accounts) for AWS security services, including AWS Security Hub
Note
ViewOnlyAccess and ReadOnlyAccess IAM managed policies provide permissions that do not include mutable actions. The ReadOnlyAccess grants read access to all AWS services and resources whereas the ViewOnlyAccess access provides read-only access and further restricts read operations to view resources and only metadata.
Recommended AWS Organization Integrated Service Delegation
| AWS service | Implementation Details | Control Tower Enabled |
|---|---|---|
|
Continuously audit your AWS use across multiple accounts in your organization to simplify how you assess risk and compliance.Recommended to be in same AWS account AWS Security Hub delegated admin exists. Delegation needs to be done on home and operational AWS Regions. |
No |
|
|
CloudFormation Stacksets can be delegated to multiple accounts within your AWS Organization. Delegation of the service needs to be completed at only one AWS region for the AWS account. |
Yes, delegation not configured |
|
|
The management of CloudTrail Org Trails can be delegated to one account. It is recommended that the Security team manage the implementation. |
Yes, delegation not configured |
|
|
Organization-wide aggregated view of your AWS resources, your AWS Config rules, and the AWS resources’ compliance state. Creating an Organization aggregator can be done across multiple AWS regions into the region the aggregator is being deploye to. Multiple accounts can be delegated the AWS Config aggregator. |
Yes, delegation not configured |
|
|
Required to be deployed to same account which is managing Amazon GuardDuty and AWS Security Hub. Requires GuardDuty to be enabled on Security Tooling account prior to delegating AWS Detective. Delegation needs to be done on home and operational AWS Regions. |
No |
|
|
Configure full delegated administration support for Security Tooling account. Firewall Manager delegation is a global configuration for all AWS Regions and only needs to be delegated from your home AWS Region. |
No |
|
|
Amazon GuardDuty allows for one delegated admin per AWS Organization. It is recommended to delegated Amazon GuardDuty to the same account AWS Security Hub and Amazon Macie are delegatd to. Delegation needs to be done on home and operational AWS Regions. |
No |
|
|
Delegate an administrator to enable or disable scans for member accounts, view aggregated finding data from the entire organization, create and manage suppression rules. Delegation needs to be done on home and operational AWS Regions. |
No |
|
|
Amazon Macie allows for one delegated admin per AWS Organization. It is recommended to delegated Amazon Macie to the same account AWS Security Hub and Amazon GuardDuty are delegatd to. Delegation needs to be done on home and operational AWS Regions. |
No |
|
|
AWS Security Hub allows for one delegated admin per AWS Organization. It is recmomended to delegated AWS Security Hub to the same account Amazon GuardDuty and Amazon Macie are delegated to, for ease of pivoting between these services in the AWS Console. Delegation needs to be done on each operational Region. |
No |
|
|
Allows for multiple delegated admin accounts per AWS Organization. Service is global and only needs to be delegated from the home AWS Region |
No |
|
|
Allows for centralized view of AWS Trusted Advisor information. Requires the management account in your organization must have a Business, Enterprise On-Ramp, or Enterprise Support plan. Service is global and only needs to be delegated from the home AWS Region. |
No |
|
|
Configured with the entire AWS organization as the zone of trust so that it’s easier for you to quickly look across resource policies and identify resources with public or cross-account access you might not intend. We recommend that you configure this analyzer in one of your security tooling accounts. |
No |
Additional Services and Functionalities
Common examples of security capabilities that can be centrally accessed and managed using the Security Tooling account include:
-
Third-party cloud security monitoring tools — You can also house third-party cloud security monitoring services and tools in your security tooling accounts. For example, these accounts typically contain security information and event management (SIEM) tools and vulnerability scanners
-
Automated detection and response workflows — Automated detection and response workflows that act on data collected through these types of services are normally contained in your security tooling accounts.
-
Incident response (IR) support — Tools to support manual incident response (IR) procedures are typically housed in your security tooling accounts. Refer to the AWS Security Incident Response Guide for more information.
AWS Solutions
| AWS Solution | Description |
|---|---|
|
Add-on that works with AWS Security Hub and provides predefined response and remediation actions based on industry compliance standards and best practices for security threats. It helps Security Hub customers to resolve common security findings and to improve their security posture in AWS. |
|
|
Allows you to centrally configure, manage, and audit firewall rules across all your accounts and resources in AWS Organizations. This solution is a reference implementation to automate the process to set up AWS Firewall Manager security policies. |
|
|
Automatically deploys a set of AWS WAF (web application firewall) rules that filter common web-based attacks. Users can select from preconfigured protective features that define the rules included in an AWS WAF web access control list (web ACL). |
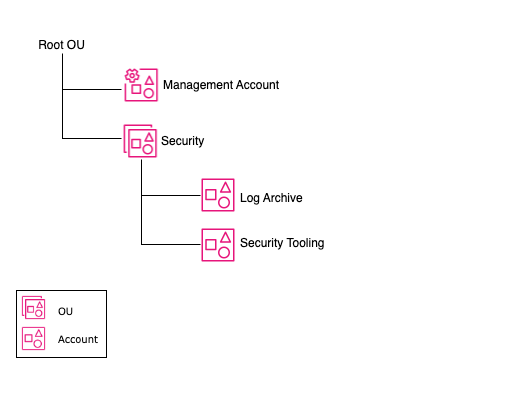
Example structure
The following example structure represents the recommended Security OU at a basic level. Note that within Control Tower governed environments, the accounts within the Security OU are limited to the Log Archive and Security Tooling (also known as Audit by default for AWS Control Tower deployments).
Example structure of Security OU