Scan Git repositories for sensitive information and security issues by using git-secrets
Saurabh Singh, Amazon Web Services
Summary
This pattern describes how to use the open-source git-secrets
git-secrets scans commits, commit messages, and merges to prevent sensitive information such as secrets from being added to your Git repositories. For example, if a commit, commit message, or any commit in a merge history matches one of your configured, prohibited regular expression patterns, the commit is rejected.
Prerequisites and limitations
Prerequisites
An active AWS account
A Git repository that requires a security scan
A Git client (version 2.37.1 and later) installed
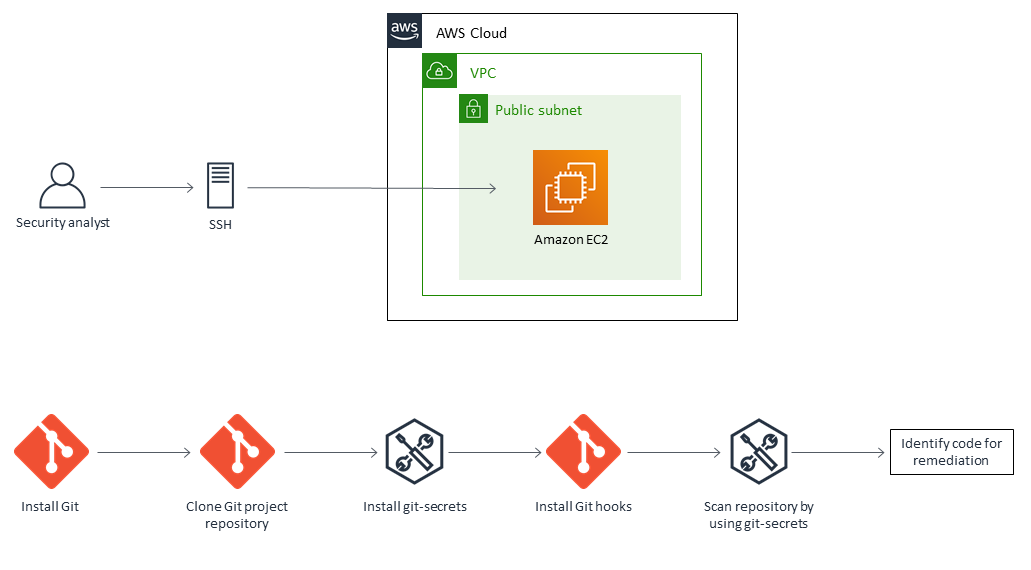
Architecture
Target architecture
Git
git-secrets
Tools
git-secrets
is a tool that prevents you from committing sensitive information into Git repositories. Git
is an open-source distributed version control system.
Best practices
Always scan a Git repository by including all revisions:
git secrets --scan-history
Epics
| Task | Description | Skills required |
|---|---|---|
Connect to an EC2 instance by using SSH. | Connect to an Amazon Elastic Compute Cloud (Amazon EC2) instance by using SSH and a key pair file. You can skip this step if you are scanning a repository on your local machine. | General AWS |
| Task | Description | Skills required |
|---|---|---|
Install Git. | Install Git by using the command:
If you are using your local machine, you can install a Git client for a specific OS version. For more information, see the Git website | General AWS |
| Task | Description | Skills required |
|---|---|---|
Clone the Git source repository. | To clone the Git repository that you want to scan, choose the Git clone command from your home directory. | General AWS |
Clone git-secrets. | Clone the
Place | General AWS |
Install git-secrets. | For Unix and variants (Linux/macOS): You can use the
For Windows: Run the PowerShell
For Homebrew (macOS users): Run:
| General AWS |
| Task | Description | Skills required |
|---|---|---|
Go to the source repository. | Switch to the directory for the Git repository that you want to scan:
| General AWS |
Register the AWS rule set (Git hooks). | To configure
| General AWS |
Scan the repository. | Run the following command to start scanning your repository:
| General AWS |
Review the output file. | The tool generates an output file if it finds a vulnerability in your Git repository. For example:
| General AWS |