Granting Amazon OpenSearch Ingestion pipelines access to domains
An Amazon OpenSearch Ingestion pipeline needs permission to write to the OpenSearch Service domain that is configured as its sink. To provide access, you configure an AWS Identity and Access Management (IAM) role with a restrictive permissions policy that limits access to the domain that a pipeline is sending data to. For example, you might want to limit an ingestion pipeline to only the domain and indexes that are required to support its use case.
Important
You can choose to manually create the pipeline role, or you can have OpenSearch Ingestion
create it for you during pipeline creation. If you choose automatic role creation,
OpenSearch Ingestion adds all required permissions to the pipeline role access policy based
on the source and sink that you choose. It creates a pipeline role in IAM with the
prefix OpenSearchIngestion- and the suffix that you enter. For more
information, see Pipeline role.
If you have OpenSearch Ingestion create the pipeline role for you, you still need to include the role in the domain access policy and map it to a backend role (if the domain uses fine-graned access control), either before or after you create the pipeline. See step 2 for instructions.
Step 1: Create the pipeline role
The pipeline role must have an attached permissions policy that allows it to send data to the domain sink. It must also have a trust relationship that allows OpenSearch Ingestion to assume the role. For instructions on how to attach a policy to a role, see Adding IAM identity permissions in the IAM User Guide.
The following sample policy demonstrates the least privilege that you can provide in a pipeline role for it to write to a single domain:
If you plan to reuse the role to write to multiple domains, you can make the policy
more broad by replacing the domain name with a wildcard character
(*).
The role must have the following trust relationship, which allows OpenSearch Ingestion to assume the pipeline role:
Step 2: Configure data access for the domain
In order for a pipeline to write data to a domain, the domain must have a domain-level access policy that allows the pipeline role to access it.
The following sample domain access policy allows the pipeline role named
pipeline-role to write data to the domain named
ingestion-domain:
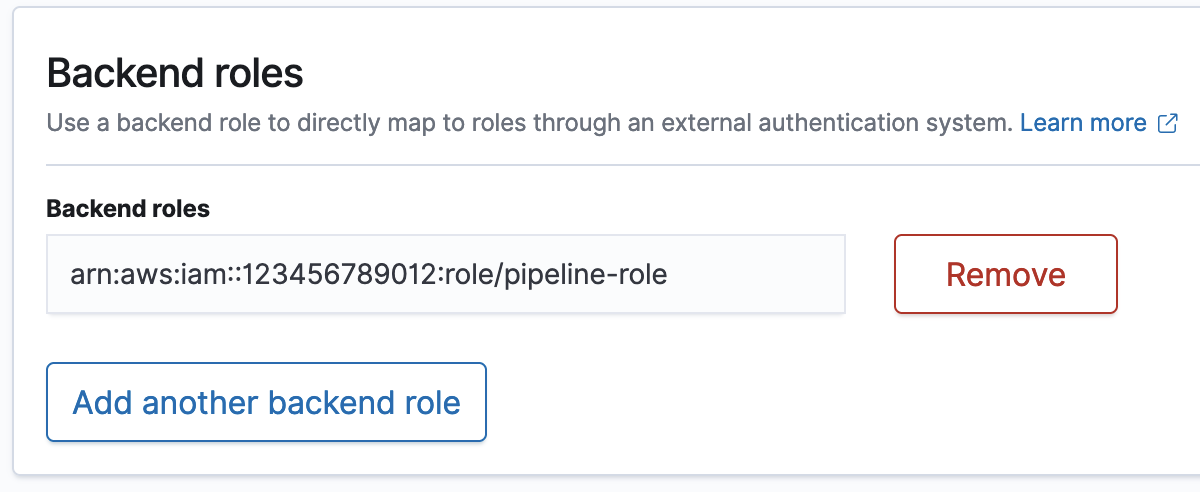
Map the pipeline role (only for domains that use fine-grained access control)
If your domain uses fine-grained access control for authentication, there are extra steps you need to take to provide your pipeline access to a domain. The steps differ depending on your domain configuration:
-
Scenario 1: Different master role and pipeline role – If you're using an IAM Amazon Resource Name (ARN) as the master user and it's different than the pipeline role, you need to map the pipeline role to the OpenSearch
all_accessbackend role. This adds the pipeline role as an additional master user. For more information, see Additional master users. -
Scenario 2: Master user in the internal user database – If your domain uses a master user in the internal user database and HTTP basic authentication for OpenSearch Dashboards, you can't pass the master username and password directly into the pipeline configuration. Instead, map the pipeline role to the OpenSearch
all_accessbackend role. This adds the pipeline role as an additional master user. For more information, see Additional master users. -
Scenario 3: Same master role and pipeline role (uncommon) – If you're using an IAM ARN as the master user, and it's the same ARN that you're using as the pipeline role, you don't need to take any further action. The pipeline has the required permissions to write to the domain. This scenario is uncommon because most environments use an administrator role or some other role as the master role.
The following image shows how to map the pipeline role to a backend role: