Using RDP to Log In to a Windows Instance
Important
The AWS OpsWorks Stacks service reached end of life on May 26, 2024 and has been disabled for both new and existing customers.
We strongly recommend customers migrate their workloads to other solutions as soon as possible. If you have questions about migration, reach out to the AWS Support Team on AWS re:Post
You can use the Windows remote desktop protocol (RDP) to log in to an online Windows instance, as follows:
-
The instance must have a security group with an inbound rule that allows RDP access.
For more information on working with security groups, see Using Security Groups.
-
Ordinary users – OpsWorks Stacks provides authorized ordinary users with an RDP password that is valid for a limited time period, which can range from 30 minutes to 12 hours.
In addition to being authorized, users must have at least a Show permission level or their attached AWS Identity and Access Management (IAM) policies must allow the
opsworks:GrantAccessaction. -
Administrators – You can use the Administrator password to log in for an unlimited amount of time.
As described later, if you have specified an Amazon Elastic Compute Cloud (Amazon EC2) key pair for the instance, you can use it to retrieve the Administrator password.
Note
This topic describes how to use the Windows Remote Desktop Connection client to log in
from a Windows workstation. You can also use one of the available RDP clients for Linux
or OS X, but the procedure might be somewhat different. For more information on RDP
clients that are compatible with Microsoft Windows Server 2012 R2, see Microsoft Remote
Desktop Clients
Topics
Providing a Security Group that Allows RDP Access
Before you can use RDP to log into a Windows instance, the instance's security group
inbound rules must allow RDP connections. When you create the first stack in a region,
OpsWorks Stacks creates a set of security groups. They include one named something like
AWS-OpsWorks-RDP-Server, which OpsWorks Stacks attaches to all Windows instances
to allow RDP access. However, by default, this security group does not have any rules,
so you must add an inbound rule to allow RDP access to your instances.
To allow RDP access
-
Open the Amazon EC2 console
, set it to the stack's region, and choose Security Groups from the navigation pane. -
Select AWS-OpsWorks-RDP-Server, choose the Inbound tab, and choose Edit.
-
Choose Add Rule and specify the following settings:
-
Type – RDP
-
Source – The permissible source IP addresses.
You typically allow inbound RDP requests from your IP address or a specified IP address range (typically your corporate IP address range).
-
Logging in As an Ordinary User
An authorized user can log in to instances using a temporary password, provided by OpsWorks Stacks.
To authorize RDP for a user;
-
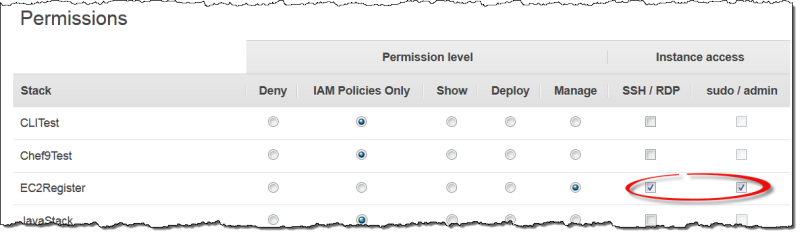
In the OpsWorks Stacks navigation pane, click Permissions.
-
Select the SSH/RDP checkbox for the desired user to grant the necessary permissions. If you want the user to have administrator permissions, you should also select sudo/admin.
Authorized users can log in to any of the stack's online instances, as follows.
To log in as an ordinary IAM user
-
Log in as an IAM user.
-
On the Instances page, choose rdp in the Actions column for the appropriate instance.
-
Specify the session length, which can vary from 30 minutes to 12 hours, and choose Generate Password. The password will be valid only for the specified session duration.
-
Record the public DNS name, username, and password values, then choose Acknowledge and close.
-
Open the Windows Remote Desktop Connection client, choose Show Options, and provide the following from the information that you recorded in Step 4:
-
Computer – The instance's public DNS name.
You can also use the public IP address, if you prefer. Choose Instances and copy the address from the instance's Public IP column.
-
User name – The user name.
-
-
When the client prompts for your credentials, enter the password that you saved in Step 4.
Note
OpsWorks Stacks generates a user password only for online instances. If you start an
instance and, for example, one of your custom Setup recipes fails, the instance will
end up in the setup_failed state. Even though the instance is not
online as far as OpsWorks Stacks is concerned, the EC2 instance is running and it's often
useful to log in to troubleshoot the issue. OpsWorks Stacks won't generate a password for you
in this case, but if you have assigned an SSH key pair to the instance, you can use
the EC2 console or CLI to retrieve the instance's Administrator password and log in
as Administrator. For more information, see the following section.
Logging in As Administrator
You can log in to an instance as Administrator by using the appropriate password. If you have assigned an EC2 key pair to an instance, Amazon EC2 uses it to automatically create and encrypt an Administrator password when the instance starts. You can then use the key pair's private key with the EC2 console, API, or CLI to retrieve and decrypt the password.
Note
You cannot use a personal SSH key pair to retrieve an Administrator password; you must use an EC2 key pair.
The following describes how to use the EC2 console to retrieve an Administrator
password and log in to an instance. If you prefer command-line tools, you can also use
the AWS CLI get-password-data command to retrieve the password.
To log in as Administrator
-
Make sure that you have specified an EC2 key pair for the instance. You can specify a default key pair for all of the stack's instances when you create the stack, or you can specify a key pair for a particular instance when you create the instance.
-
Open the EC2 console
, set it to the stack's region, and choose Instances from the navigation pane. -
Select the instance, choose Connect, and choose Get Password.
-
Provide a path to the EC2 key pair's private key on your workstation, and choose Decrypt Password. Copy the decrypted password for later use.
-
Open the Windows Remote Desktop Connection client, choose Show Options, and provide the following information:
-
Computer – The instance's public DNS name or public IP address, which you can get from the instance's details page.
-
User name –
Administrator.
-
-
When the client prompts for your credentials, provide the decrypted password from Step 4.