Using SSH to Log In to a Linux Instance
Important
The AWS OpsWorks Stacks service reached end of life on May 26, 2024 and has been disabled for both new and existing customers.
We strongly recommend customers migrate their workloads to other solutions as soon as possible. If you have questions about migration, reach out to the AWS Support Team on AWS re:Post
You can log into your online Linux instances with SSH using either the built-in MindTerm client, or a third-party client, such as PuTTY. SSH typically depends on an RSA key pair for authentication. You install the public key on the instance and provide the corresponding private key to the SSH client. OpsWorks Stacks handles installing public keys on your stack's instances for you, as follows.
-
Amazon Elastic Compute Cloud (Amazon EC2)key pair – If the stack's region has one or more Amazon EC2 key pairs, you can specify a default SSH key pair for the stack.
You can optionally override the default key pair and specify a different pair when you create an instance. In either case, OpsWorks Stacks installs the specified key pair's public key on the instance. For more information on how to create Amazon EC2 key pairs, see Amazon EC2 Key Pairs.
-
Personal key pair – Each user can register a personal key pair with OpsWorks Stacks.
The user or an administrator registers the public key with OpsWorks Stacks, and the user stores the private key locally. When setting permissions for a stack, the administrator specifies which users should have SSH access to the stack's instances. OpsWorks Stacks automatically creates a system user on the stack's instances for each authorized user and installs the users' personal public key.
A user must have SSH authorization to use the MindTerm SSH client or to use their personal key pair to log in to a stack's instances.
To authorize SSH for a user
-
In the OpsWorks Stacks navigation pane, click Permissions.
-
Select SSH/RDP for the desired IAM user to grant the necessary permissions. If you want to allow the user to use
sudoto elevate privileges—for example, to run agent CLI commands—select sudo/admin also.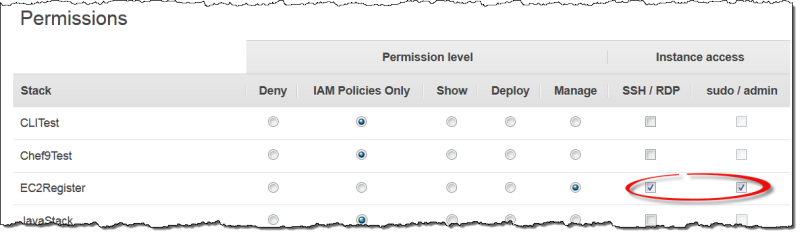
For more information on how to use OpsWorks Stacks to manage SSH access, see Managing SSH Access.