Granting QuickSight access to IAM users
Note
An IAM user is an entity that you create in AWS Identity and Access Management (IAM). This type of entity accesses your AWS account by using long-term credentials. As a best practice, AWS recommends that you grant access through temporary credentials by using identity federation and IAM roles. For more information, see Security best practices in IAM.
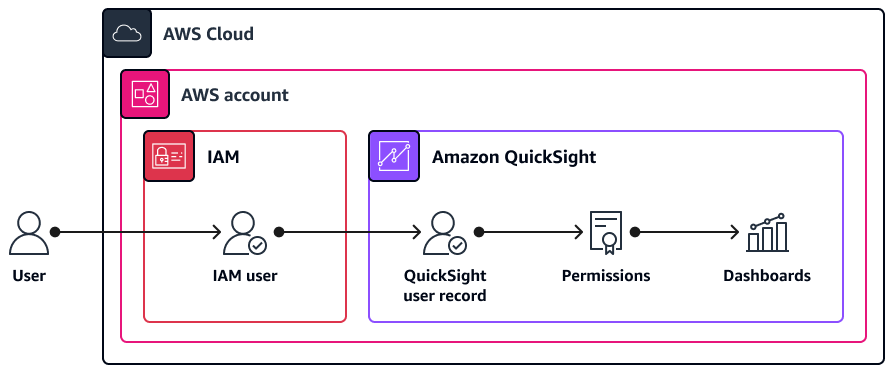
The following are the characteristics of this architecture and access approach:
-
The Amazon QuickSight user record is linked to the user in IAM.
-
User passwords are managed in IAM.
-
You can invite IAM users directly or create an IAM identity-based policy that permits users to self-provision access.
-
This type of user can log in through the QuickSight console or through the AWS Management Console.
Considerations and use cases
Although AWS generally doesn't recommend configuring access through IAM users, other access approaches, such as federation, might not be currently available in your organization. Many organizations that are just starting their cloud journey have not yet established IAM roles and are working in a single-account architecture. If your organization uses IAM users to access your AWS environment, then reapplying that approach to QuickSight might be the most straightforward and sensible approach until your organization supports other approaches.
Prerequisites
-
For the direct invitation approach, you need:
-
Administrative permissions in QuickSight (see IAM identity-based policies for the Standard or Enterprise editions)
-
The email address of the IAM user
-
-
For the self-provisioned access approach, the user needs permissions to create Amazon QuickSight (see IAM identity-based policies for Amazon QuickSight: creating users)
-
The IAM user must have a password associated with their IAM credentials
Configuring access for an IAM user
You can grant access to QuickSight for IAM users by using either of the following options:
-
Direct invitation – You invite the IAM user to access QuickSight, and the user can accept the invitation through their email.
-
Self-provisioned access – You create an IAM policy that permits users to provision their own access. When a user accesses QuickSight for the first time, they are granted access and define the email address that will be associated with their QuickSight user record.
The result of both options is the same: the IAM user can access QuickSight. However, there are advantages and disadvantages to each, as shown in the following table. For example, the direct invitation might be preferable for organizations that want to enforce use of approved corporate email addresses.
Approach |
Advantages |
Disadvantages |
|---|---|---|
Direct invitation |
|
|
Self-provisioned access |
|
|
Direct invitation
For instructions on how to configure access for an IAM user, see Inviting users to access Amazon QuickSight. Note the following when configuring this type of user access:
-
For the QuickSight username, enter the username of the IAM user. Allowed characters are letters, numbers, and the following characters: . _ - (hyphen).
-
For IAM user, choose Yes.
-
The user has seven days to accept the invitation. If they don't accept within this time period, you can resend the invitation email.
-
When the user accepts the invitation, they must enter the password that is associated with their IAM credentials.
Self-provisioned access
When IAM users can self-provision access, they don't need to be invited to the QuickSight account. The first time they try to access the QuickSight console, they must enter an email address. When the user chooses Continue, QuickSight creates a user record for that IAM user.
To grant permission to provision their own access, you create an identity-based policy and apply that policy to the IAM users or IAM user group. For more information, see Configuring IAM policies in this guide.