Workforce identity management
Workforce identity management, which is illustrated in the following diagram, refers to managing human access to resources that help build and manage your businesses within your cloud infrastructure and applications. It supports secure provisioning, managing, and removing access, as employees join an organization, move between roles, and leave an organization. Identity administrators can create identities directly in AWS or connect to an external identity provider (IdP) to enable employees to use their corporate credentials to securely access AWS accounts and business applications from one place.
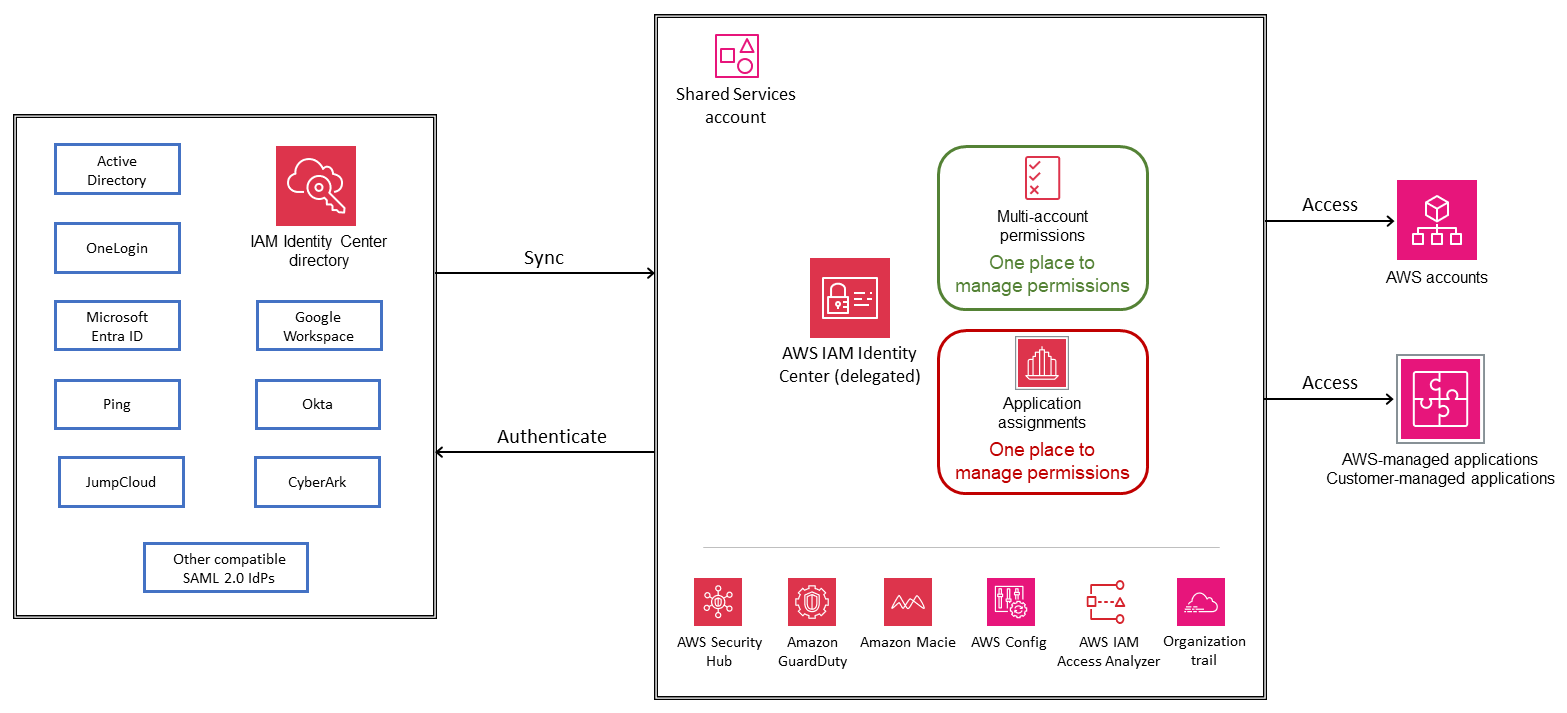
By using AWS IAM Identity Center to manage access to AWS managed applications, you can benefit from new capabilities such as trusted identity propagation from your query application to the AWS data service, and new services such as Amazon Q that provide a continuous user experience as users move from one Amazon Q-enabled service to another. The use of IAM Identity Center for AWS account access prevents the creation and use of IAM users, which have long-term access to resources. Instead, it enables workforce identities to access resources in AWS accounts by using temporary credentials from IAM Identity Center, which is a security best practice. Workforce identity management services let you define fine-grained access control for AWS resources or applications in your multi-account AWS environment based on specific job functions or user attributes. These services also help audit and review user activities within your AWS environment.
AWS offers several several options for workforce identity and access management: AWS IAM Identity Center, IAM SAML federation, and AWS Managed Microsoft AD.
-
AWS IAM Identity Center is the recommended service for managing workforce access to AWS applications and multiple AWS accounts. You can use this service with an existing identity source, such as Okta, Microsoft Entra ID, or on-premises Active Directory, or by creating users in its directory. IAM Identity Center supplies all AWS services with a shared understanding of your workforce users and groups. AWS managed applications integrate with it, so you do not need to connect your identity source individually to each service, and you can manage and view your workforce access from a central location. You can use IAM Identity Center to manage access to AWS applications while you continue to use your established configuration to access AWS accounts. For new multi-account environments, IAM Identity Center is the recommended service to manage your workforce access to the environment. You can assign permissions consistently across AWS accounts, and your users receive single sign-on access across AWS.
-
An alternate way to grant your workforce access to AWS accounts is by using IAM SAML 2.0 federation. This involves creating one-to-one trust between your organization's IdP and each AWS account, and isn't recommended for multi-account environments. Inside your organization, you must have an IdP that supports SAML 2.0, such as Microsoft Entra ID, Okta, or another compatible SAML 2.0 provider.
-
Another option is to use Microsoft Active Directory (AD) as a managed service to run directory-aware workloads in AWS. You can also configure a trust relationship between AWS Managed Microsoft AD in the AWS Cloud and your existing on-premises Microsoft Active Directory, to provide users and groups with access to resources in either domain by using AWS IAM Identity Center.
Design considerations
-
Although this section discusses several services and options, we recommend that you use IAM Identity Center to manage workforce access, because it has advantages over the other two approaches. Later sections discuss the advantages and use cases for individual approaches. A growing number of AWS managed applications require the use of IAM Identity Center. If you are currently using IAM federation, you can enable and use IAM Identity Center with AWS applications without changing your existing configurations.
-
To improve federation resiliency, we recommend that you configure your IdP and AWS federation to support multiple SAML sign-in endpoints. For details, see the AWS blog post How to use regional SAML endpoints for failover
.