DNS
When you launch an instance into a VPC, excluding the default VPC, AWS provides the instance with a
private DNS hostname (and potentially a public DNS hostname) depending on the DNS
attributes you specify for the VPC and if your instance has a public IPv4
address. When the enableDnsSupport attribute is set to true, you get a
DNS resolution within the VPC from Route 53 Resolver (+2 IP offset to the VPC CIDR). By default,
Route 53 Resolver answers DNS queries for VPC domain names such as domain names for EC2 instances
or Elastic Load Balancing load balancers. With VPC peering, hosts in one VPC can resolve public DNS hostnames to
private IP addresses for instances in peered VPCs, provided the option to do so is enabled. The
same is applicable for VPCs connected via AWS Transit Gateway. For more information, refer to Enabling
DNS Resolution Support for a VPC Peering Connection.
If you want to map your instances to a custom domain name, you can use Amazon Route 53
Hybrid DNS
DNS is a critical component of any infrastructure, hybrid or otherwise, as it provides the hostname-to-IP-address resolution that applications rely on. Customers implementing hybrid environments usually have a DNS resolution system already in place, and they want a DNS solution that works in tandem with their current system. Native Route 53 resolver (+2 offset of the base VPC CIDR) is not reachable from on-premises networks using VPN or AWS Direct Connect. Therefore, when you integrate DNS for the VPCs in an AWS Region with DNS for your network, you need a Route 53 Resolver inbound endpoint (for DNS queries that you are forwarding to your VPCs) and a Route 53 Resolver outbound endpoint (for queries that you are forwarding from your VPCs to your network).
As shown in the following figure, you can configure outbound Resolver endpoints to forward queries it receives from Amazon EC2 instances in your VPCs to DNS servers on your network. To forward selected queries, from a VPC to an on-premises network, create Route 53 Resolver rules that specify the domain names for the DNS queries that you want to forward (such as example.com), and the IP addresses of the DNS resolvers on your network where you want to forward the queries. For inbound queries from on-premises networks to Route 53 hosted zones, DNS servers on your network can forward queries to inbound Resolver endpoints in a specified VPC.
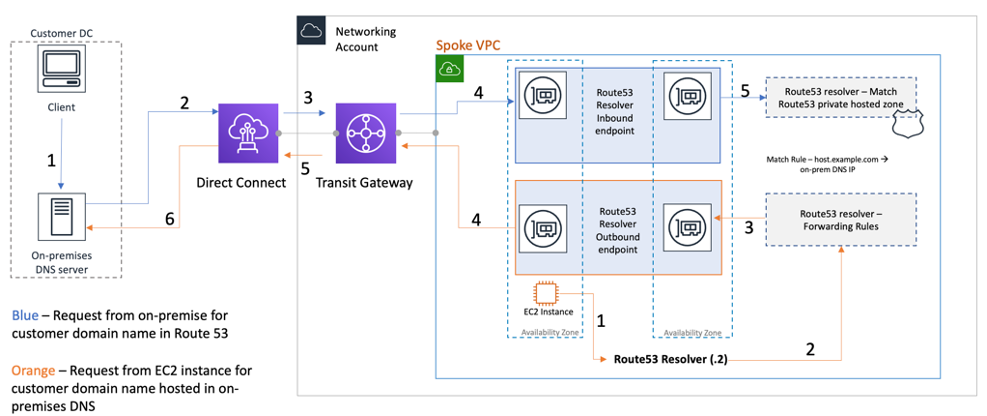
Hybrid DNS resolution using Route 53 Resolver
This allows your on-premises DNS resolvers to easily resolve domain names for AWS resources, such as Amazon EC2 instances or records in a Route 53 private hosted zone associated with that VPC. In addition, Route 53 Resolver endpoints can handle up to approximately 10,000 queries per second per ENI, so can scale to much larger DNS query volume easily. Refer to Best practices for Resolver in the Amazon Route 53 documentation for more details.
It is not recommended that you create Route 53 Resolver endpoints in every VPC of the Landing Zone. Centralize them in a central egress VPC (in the Network services account). This approach allows for better manageability while keeping the costs low (you are charged an hourly fee for each inbound/outbound resolver endpoint you create). You share the centralized inbound and outbound endpoint with the rest of the Landing Zone.
-
Outbound resolution — Use the Network Services account to write resolver rules (based on which DNS queries will be forwarded to on-premises DNS servers). Using Resource Access Manager (RAM), share these Route 53 Resolver rules with multiple accounts (and associate with VPCs in the accounts). EC2 instances in spoke VPCs can send DNS queries to Route 53 Resolver and Route 53 Resolver Service will forward these queries to on-premises DNS server via the outbound Route 53 Resolver endpoints in the egress VPC. You don’t need to peer spoke VPCs to the egress VPC, or connect them via Transit Gateway. Do not use the IP of the outbound resolver endpoint as the primary DNS in the spoke VPCs. Spoke VPCs should use Route 53 Resolver (to offset of the VPC CIDR) in their VPC.
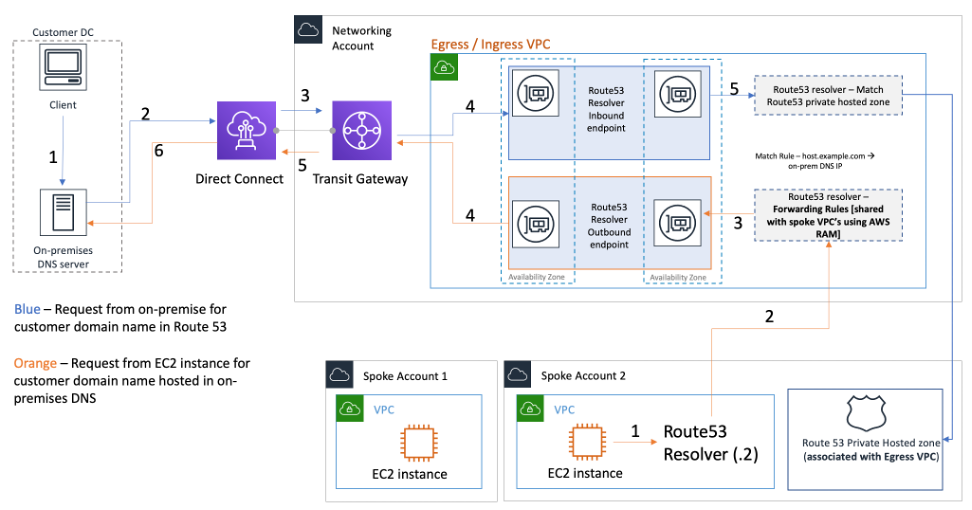
Centralizing Route 53 Resolver endpoints in ingress/egress VPC
-
Inbound DNS resolution – Create Route 53 Resolver inbound endpoints in a centralized VPC and associate all the private hosted zones in your Landing Zone with this centralized VPC. For more information, refer to Associating More VPCs with a Private Hosted Zone. Multiple Private Hosted Zones (PHZ) associated with a VPC cannot overlap. As shown in the preceding figure, this association of PHZ with the centralized VPC will enable on-premises servers to resolve DNS for any entry in any private hosted zone (associated with central VPC) using the inbound endpoint in the centralized VPC. For further more information on hybrid DNS setups, refer to Centralized DNS management of hybrid cloud with Amazon Route 53 and AWS Transit Gateway
and Hybrid Cloud DNS Options for Amazon VPC .
Route 53 DNS Firewall
Amazon Route 53 Resolver DNS Firewall helps filter and regulate outbound DNS traffic for your VPCs. A primary use of the DNS Firewall is to help prevent data exfiltration of your data by defining domain name allow-lists which allow resources in your VPC to make outbound DNS requests only for the sites your organization trusts. It also gives customers the ability to create blocklists for domains they don’t want resources inside a VPC to communicate with via DNS. Amazon Route 53 Resolver DNS firewall has the following features:
Customers can create rules to define how DNS queries are answered. The actions that can be
defined for the domain names include NODATA, OVERRIDE and NXDOMAIN.
Customers can create alerts for both allow-lists and deny-lists to monitor the rule activity. This can come in handy when customers want to test the rule before moving it to production.
For more information, refer to the How to Get Started with Amazon Route 53 Resolver DNS Firewall for Amazon VPC