This whitepaper is for historical reference only. Some content might be outdated and some links might not be available.
Security Best Practices for Manufacturing OT
Publication date: May 21, 2021 (Document history and contributors)
Abstract
New developments in cloud, Internet of Things (IoT), and edge computing have opened the door for traditionally on-premises manufacturing operations technology (OT) workloads to evolve into hybrid workloads. This whitepaper describes security best practices to design, deploy, and architect these on-premises hybrid manufacturing workloads for the AWS Cloud.
Introduction
Traditionally, manufacturing workloads can be categorized as operation technology (OT) workloads and information technology (IT) workloads. OT workloads support production operations. Enterprise operations are supported by IT workloads.
OT workloads are typically located within factories, because they support operations on the production floor. However, the adoption of cloud, IoT, and edge computing enables OT workloads to transform from on-premises to hybrid workloads, which can take advantage of cloud services.
This document describes the security best practices to design, deploy, and architect
distributed manufacturing workloads for the AWS Cloud. The focus of this document is securing
resources at the industrial edge. The best practices for securing cloud resources are
documented in the Security
Pillar of the AWS Well-Architected Framework
The Purdue model, as shown the following figure, is used as the backdrop to define cloud integration points and placement for resources for manufacturing workloads. The Purdue model is a reference model for the manufacturing industry, and is used as the basis for the International Society of Automation ISA-95 standard to define detailed information models for manufacturing and enterprise integration.
Purdue enterprise reference architecture model
Taking the Purdue reference model and applying it to an industrial control network illustrates the distribution of IT and OT functions, as seen in the following figure:

Purdue Model representation of an industrial control network
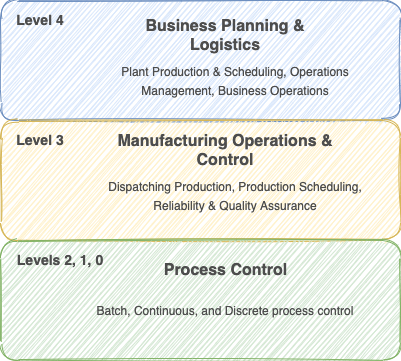
Levels 4 and 5 are in the IT domain. In most enterprises, the enterprise network boundary to the internet (level 5) is traditionally controlled by the IT organization, along with business operations served by the infrastructure in level 4. The most frequently used connection method between the enterprise and the AWS Cloud is over the internet through the internet DMZ firewall in level 5.
The firewall between levels 3 and 4 is the interface between the corporate data backbone and the local industrial facility. The functions implemented in levels 3 and below are tied to production operations and control.
Levels 2, 1, and 0 form what is sometimes referred to as the Cell / Area zone. Level 2 contains human machine interface (HMI), Supervisory Control and Data Acquisition (SCADA), and Distributed Control System (DCS) used to interact with production control assets (field devices and sensors) in level 0 via logical controllers in level 1.
The emergence of connected sensors and controllers that take advantage of IoT technologies has introduced new gateway devices that can be used with local HMI assets, but are purposely designed to send industrial asset and machine data to the cloud.
Insights for improving operational efficiency are driven from the data generated by services and applications including Manufacturing Execution Systems (MES), SCADA/DCS and Programmable Logic Controllers (PLC) in levels 3, 2 and 1, which is what this document focuses on. Processing this data efficiently is best accomplished by leveraging the availability of on-demand compute resources, unlimited cost-efficient storage, and analytics and Artificial Intelligence/Machine Learning (AI/ML) services in the AWS Cloud.
Connectivity to AWS and AWS services can be achieved with a variety of AWS services, such
as AWS Direct Connect