Integrating Amazon Cognito authentication and authorization with web and mobile apps
Implementation of Amazon Cognito is a mix of AWS Management Console or AWS SDK administrative tools, and SDK libraries in applications. The Amazon Cognito console is the visual interface for setup and management of your Amazon Cognito user pools and identity pools.
The lowest-effort integration you can create with Amazon Cognito user pools is with managed login. Managed login is a ready-to-use web-based sign-in application for quick testing and deployment of Amazon Cognito user pools. User pool authentication with managed login requires OpenID Connect (OIDC) libraries that direct users to hosted sign-in pages. In this series of user-interactive and redirect web endpoints, Amazon Cognito handles the flow of authentication, including third-party sign-in, multi-factor authentication (MFA), and choosing an authentication flow. Your application only has to process the authentication outcome that Amazon Cognito returns in the response.
You can also add an AWS SDK to your application, custom-build authentication interfaces,
and invoke API operations for authentication and authorization of your users. AWS Amplify
For example, your app might invoke managed login for user sign-in, then call the token endpoint from your app code to exchange your user's authorization code for tokens. Then your app must interpret and store your user's tokens, and present them in the appropriate context for authentication and authorization. Amplify adds guided integration tools with built-in functions for these processes.
You can also build your Amazon Cognito resources entirely in code. Identity pools don't have the same
managed authentication options as user pools—for access to AWS credentials in your
applications, implement identity pools operations in imported SDK modules. To get started with
your own custom-built application code, visit the Amazon Cognito code examples for
AWS SDKs
Before you use Amazon Cognito authentication and authorization, choose an app platform and prepare your code to integrate with the service. For available platforms for AWS SDKs, see Authentication with AWS SDKs. The AWS CLI is a command-line SDK for Amazon Cognito and other AWS services, and is a valuable place to begin to familiarize yourself with Amazon Cognito API operations and their syntax.
Note
Some components of Amazon Cognito can be configured only with the API. For example, you can only
set a user pool custom SMS
or email sender Lambda trigger with a request that updates the
LambdaConfig property of the UserPool
class in a CreateUserPool or UpdateUserPool API request.
The Amazon Cognito user pools API shares its namespace with several classes of API operations. One class configures user pools and their processes, identity providers and users. Another includes unauthenticated operations for your users in a public client to sign in, sign out, and manage their profiles. The final class of API operations performs user operations that you authorize with your own AWS credentials in a confidential server-side client. You must know your intended app architecture before you begin to implement app code. For more information, see Understanding API, OIDC, and managed login pages authentication.
Topics
Authentication with AWS Amplify
AWS Amplify is a complete solution for building web and mobile applications. With
Amplify, you can connect to existing resources with the Amplify libraries, or you can
create and configure new resources with the Amplify command line interface (CLI). Amplify
also has connected UI components like Authenticator
To use Amplify authentication features in your front-end app, see the following documentation by platform.
The Amplify libraries are open source and are available on GitHub
Creating a user interface (UI) with Amplify
User pool managed login can fulfill the essential needs of an
authentication front-end for a web or mobile app. To customize your user interface (UI)
beyond the parameters that managed login accommodates, custom-build an application. Amplify UI
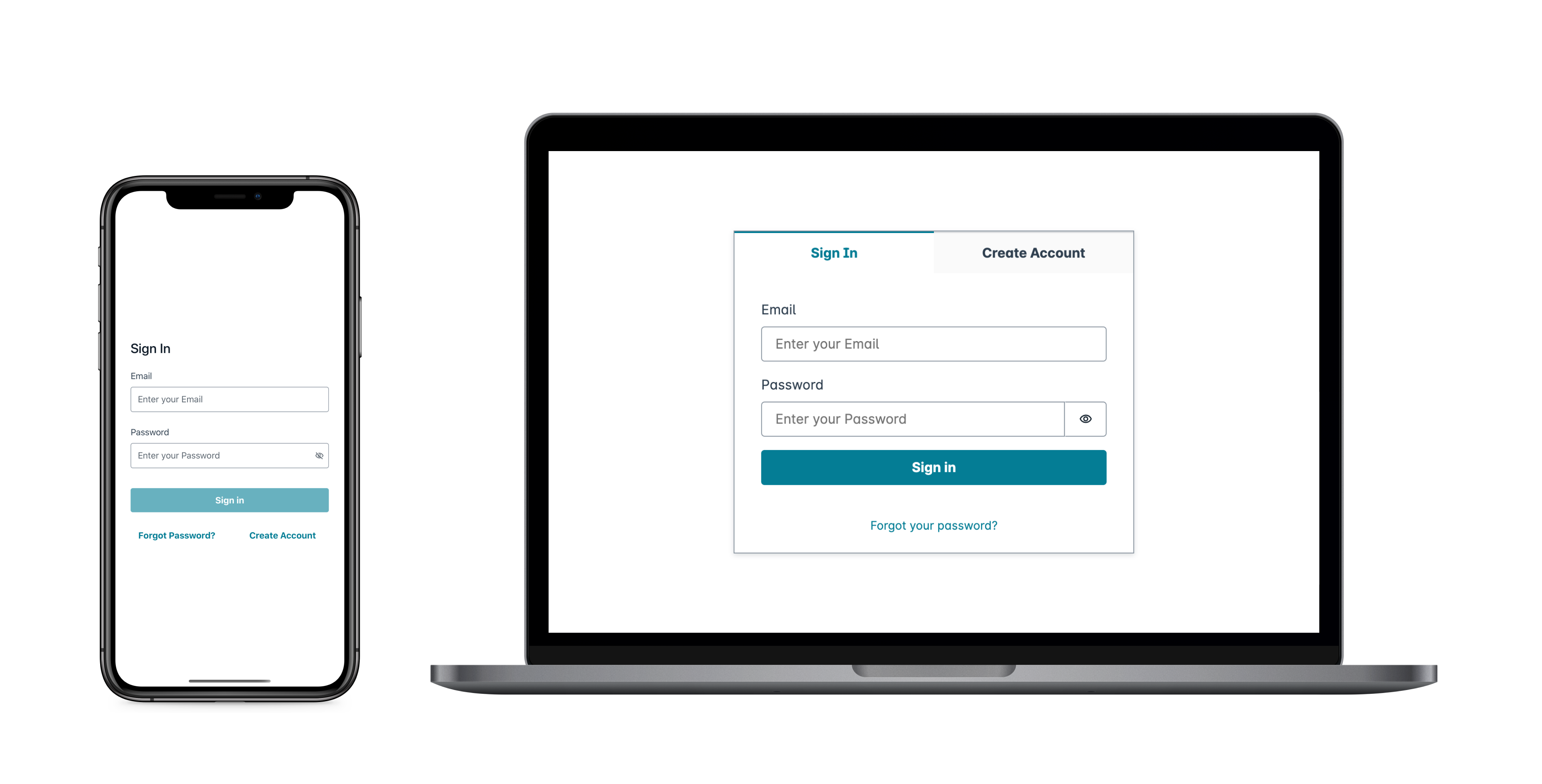
To get started with your custom authentication component, visit the following documentation for the Authenticator component.
Authentication with AWS SDKs
To use a secure backend to build your own identity microservice that interacts with Amazon Cognito, connect to the Amazon Cognito user pools and Amazon Cognito identity pools API with an AWS SDK in the language of your choice.
For details on each API operation, see the Amazon Cognito user pools API Reference and the Amazon Cognito API Reference. These documents contain See also sections with resources for using a variety of SDKs in supported platforms.