Policy summary (list of services)
Policies are summarized in three tables: the policy summary, the service summary, and the action summary. The policy summary table includes a list of services and summaries of the permissions that are defined by the chosen policy.
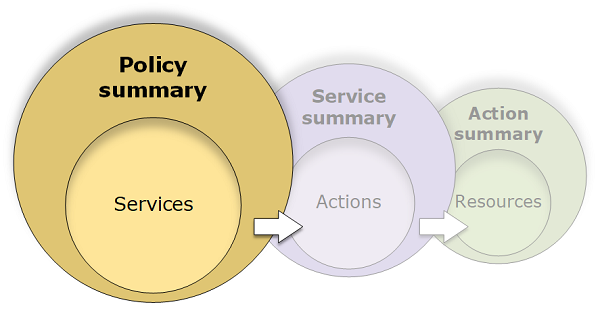
The policy summary table is grouped into one or more Uncategorized
services, Explicit deny, and Allow
sections. If the policy includes a service that IAM does not recognize, then the service is
included in the Uncategorized services section of the table. If IAM
recognizes the service, then it is included under the Explicit deny or
Allow sections of the table, depending on the effect of the policy
(Deny or Allow).
Understanding the elements of a policy summary
In the following example of a policy details page, the SummaryAllElements policy is a managed policy (customer managed policy) that is attached directly to the user. This policy is expanded to show the policy summary.
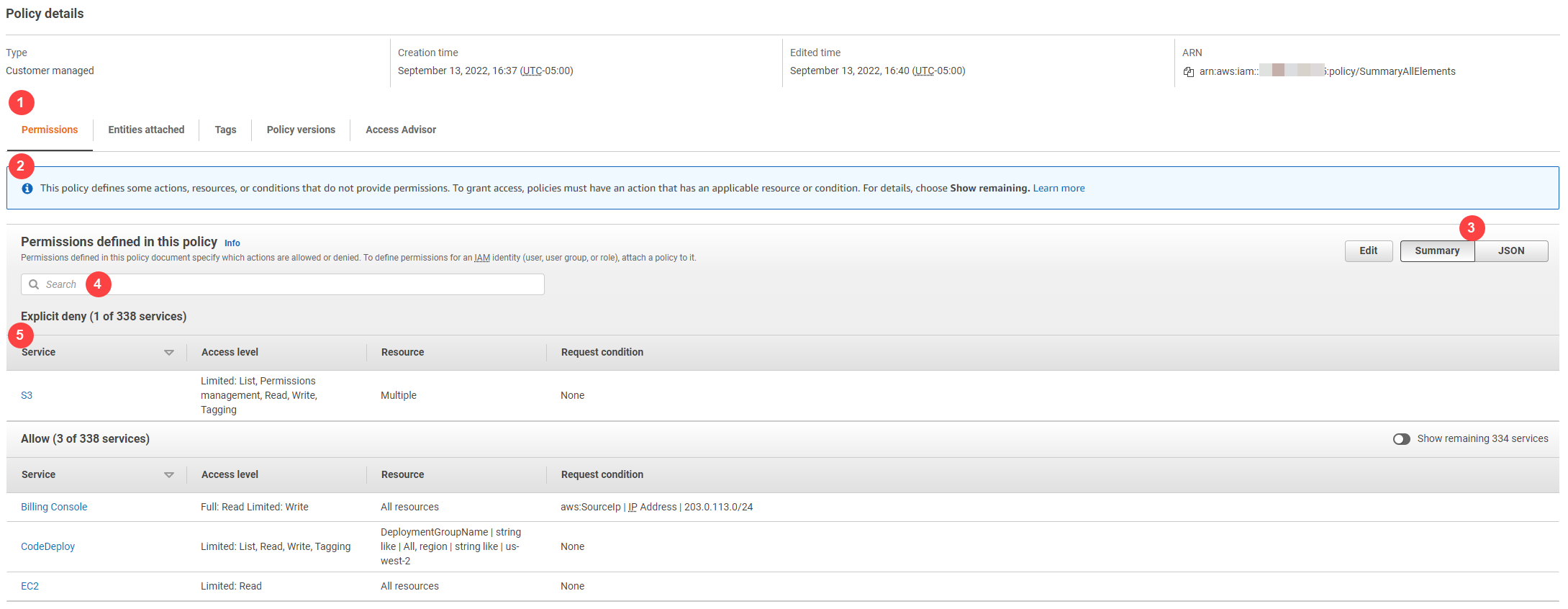
In the preceding image, the policy summary is visible from within the Policies page:
-
The Permissions tab includes the permissions defined in the policy.
-
If the policy does not grant permissions to all the actions, resources, and conditions defined in the policy, then a warning or error banner appears at the top of the page. The policy summary then includes details about the problem. To learn how policy summaries help you to understand and troubleshoot the permissions that your policy grants, see My policy does not grant the expected permissions.
-
Use the Summary and JSON buttons to toggle between the policy summary and the JSON policy document.
-
Use the Search box to reduce the list of services and find a specific service.
-
The expanded view shows additional details of the SummaryAllElements policy.
The following policy summary table image shows the expanded SummaryAllElements policy on the policy details page.
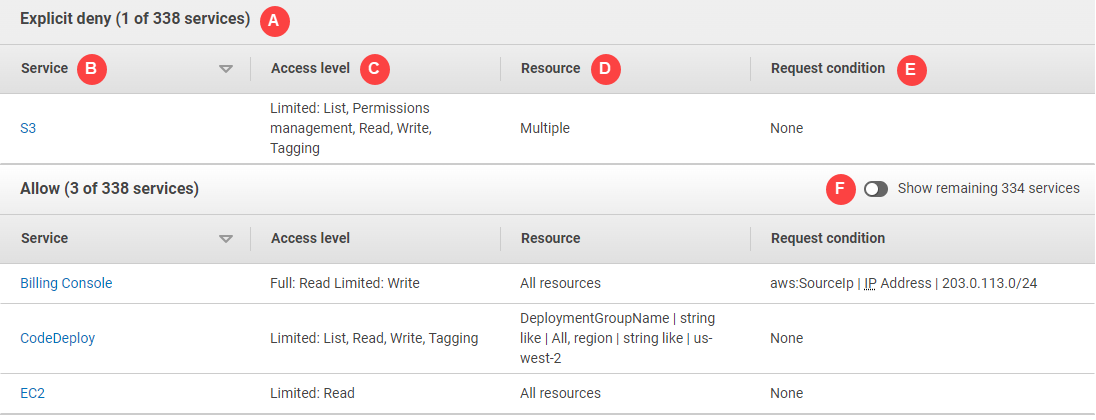
In the preceding image, the policy summary is visible from within the Policies page:
-
For those services that IAM recognizes, it arranges services according to whether the policy allows or explicitly denies the use of the service. In this example, the policy includes a
Denystatement for the Amazon S3 service andAllowstatements for the Billing, CodeDeploy, and Amazon EC2 services. -
Service – This column lists the services that are defined within the policy and provides details for each service. Each service name in the policy summary table is a link to the service summary table, which is explained in Service summary (list of actions). In this example, permissions are defined for the Amazon S3, Billing, CodeDeploy, and Amazon EC2 services.
-
Access level – This column tells whether the actions in each access level (
List,Read,Write,Permission Management, andTagging) haveFullorLimitedpermissions defined in the policy. For additional details and examples of the access level summary, see Access levels in policy summaries.-
Full access – This entry indicates that the service has access to all actions within all four of the access levels available for the service.
-
If the entry does not include Full access, then the service has access to some but not all of the actions for the service. The access is then defined by following descriptions for each of the access level classifications (
List,Read,Write,Permission Management, andTagging):Full: The policy provides access to all actions within each access level classification listed. In this example, the policy provides access to all of the Billing
Readactions.Limited: The policy provides access to one or more but not all actions within each access level classification listed. In this example, the policy provides access to some of the Billing
Writeactions.
-
-
Resource – This column shows the resources that the policy specifies for each service.
-
Multiple – The policy includes more than one but not all of the resources within the service. In this example, access is explicitly denied to more than one Amazon S3 resource.
-
All resources – The policy is defined for all resources within the service. In this example, the policy allows the listed actions to be performed on all Billing resources.
-
Resource text – The policy includes one resource within the service. In this example, the listed actions are allowed on only the
DeploymentGroupNameCodeDeploy resource. Depending on the information that the service provides to IAM, you might see an ARN or you might see the defined resource type.Note
This column can include a resource from a different service. If the policy statement that includes the resource does not include both actions and resources from the same service, then your policy includes mismatched resources. IAM does not warn you about mismatched resources when you create a policy, or when you view a policy in the policy summary. If this column includes a mismatched resource, then you should review your policy for errors. To better understand your policies, always test them with the policy simulator.
-
-
Request condition – This column indicates whether the services or actions associated with the resource are subject to conditions.
-
None – The policy includes no conditions for the service. In this example no conditions are applied to the denied actions in the Amazon S3 service.
-
Condition text – The policy includes one condition for the service. In this example, the listed Billing actions are allowed only if the IP address of the source matches
203.0.113.0/24. -
Multiple – The policy includes more than one condition for the service. To view each of the multiple conditions for the policy, choose JSON to view the policy document.
-
-
Show remaining services – Toggle this button to expand the table to include the services that are not defined by the policy. These services are implicitly denied (or denied by default) within this policy. However, a statement in another policy might still allow or explicitly deny using the service. The policy summary summarizes the permissions of a single policy. To learn about how the AWS service decides whether a given request should be allowed or denied, see Policy evaluation logic.
When a policy or an element within the policy does not grant permissions, IAM provides additional warnings and information in the policy summary. The following policy summary table shows the expanded Show remaining services services on the SummaryAllElements policy details page with the possible warnings.

In the preceding image, you can see all services that include defined actions, resources, or conditions with no permissions:
-
Resource warnings – For services that do not provide permissions for all of the included actions or resources, you see one of the following warnings in the Resource column of the table:
-
 No resources are defined. – This means that
the service has defined actions but no supported resources are included in the
policy.
No resources are defined. – This means that
the service has defined actions but no supported resources are included in the
policy.
-
 One or more actions do not have an applicable
resource. – This means that the service has defined actions, but
that some of those actions don't have a supported resource.
One or more actions do not have an applicable
resource. – This means that the service has defined actions, but
that some of those actions don't have a supported resource. -
 One or more resources do not have an applicable
action. – This means that the service has defined resources, but
that some of those resources don't have a supporting action.
One or more resources do not have an applicable
action. – This means that the service has defined resources, but
that some of those resources don't have a supporting action.
If a service includes both actions that do not have an applicable resource and resources that do have an applicable resource, then only the One or more resources do not have an applicable action. warning is shown. This is because when you view the service summary for the service, resources that do not apply to any action are not shown. For the
ListAllMyBucketsaction, this policy includes the last warning because the action does not support resource-level permissions, and does not support thes3:x-amz-aclcondition key. If you fix either the resource problem or the condition problem, the remaining issue appears in a detailed warning. -
-
Request condition warnings – For services that do not provide permissions for all of the included conditions, you see one of the following warnings in the Request condition column of the table:
-
 One or more actions do not have an applicable
condition. – This means that the service has defined actions, but
that some of those actions don't have a supported condition.
One or more actions do not have an applicable
condition. – This means that the service has defined actions, but
that some of those actions don't have a supported condition. -
 One or more conditions do not have an applicable
action. – This means that the service has defined conditions, but
that some of those conditions don't have a supporting action.
One or more conditions do not have an applicable
action. – This means that the service has defined conditions, but
that some of those conditions don't have a supporting action.
-
-
Multiple |
 One or more actions do not have an applicable resource.
– The
One or more actions do not have an applicable resource.
– The Denystatement for Amazon S3 includes more than one resource. It also includes more than one action, and some actions support the resources and some do not. To view this policy, see SummaryAllElements JSON policy document. In this case, the policy includes all Amazon S3 actions, and only the actions that can be performed on a bucket or bucket object are denied. -
 No resources are defined – The service has
defined actions, but no supported resources are included in the policy, and therefore the
service provides no permissions. In this case, the policy includes CodeCommit actions but no
CodeCommit resources.
No resources are defined – The service has
defined actions, but no supported resources are included in the policy, and therefore the
service provides no permissions. In this case, the policy includes CodeCommit actions but no
CodeCommit resources. -
DeploymentGroupName | string like | All, region | string like | us-west-2 |
 One or more actions do not have an applicable resource.
– The service has a defined action, and at least one more action that does not have
a supporting resource.
One or more actions do not have an applicable resource.
– The service has a defined action, and at least one more action that does not have
a supporting resource. -
None |
 One or more conditions do not have an applicable action.
– The service has at least one condition key that does not have a supporting
action.
One or more conditions do not have an applicable action.
– The service has at least one condition key that does not have a supporting
action.
SummaryAllElements JSON policy document
The SummaryAllElements policy is not intended for you to use to define permissions in your account. Rather, it is included to demonstrate the errors and warnings that you might encounter while viewing a policy summary.