How API Gateway resource policies affect authorization workflow
When API Gateway evaluates the resource policy attached to your API, the result is affected by the authentication type that you have defined for the API, as illustrated in the flowcharts in the following sections.
Topics
API Gateway resource policy only
In this workflow, an API Gateway resource policy is attached to the API, but no authentication type is defined for the API. Evaluation of the policy involves seeking an explicit allow based on the inbound criteria of the caller. An implicit denial or any explicit denial results in denying the caller.
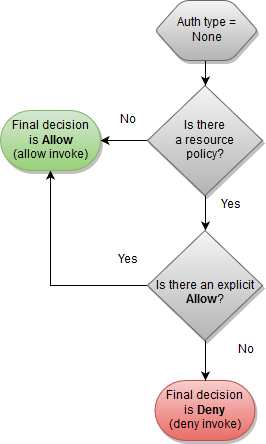
The following is an example of such a resource policy.
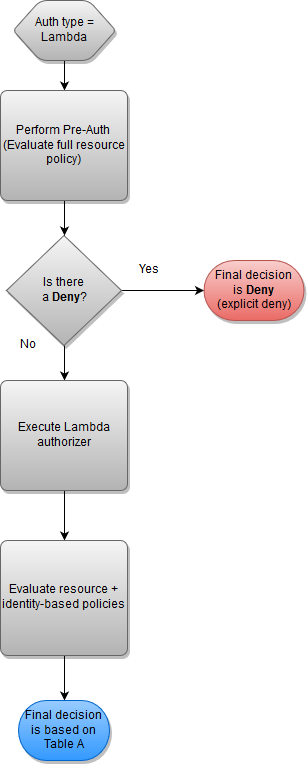
Lambda authorizer and resource policy
In this workflow, a Lambda authorizer is configured for the API in addition to a resource policy. The resource policy is evaluated in two phases. Before calling the Lambda authorizer, API Gateway first evaluates the policy and checks for any explicit denials. If found, the caller is denied access immediately. Otherwise, the Lambda authorizer is called, and it returns a policy document, which is evaluated in conjunction with the resource policy. If your authorizer uses caching, API Gateway might return the cached policy document. The result is determined based on Table A.
The following example resource policy allows calls only from the VPC endpoint whose VPC endpoint ID is
vpce-1a2b3c4d
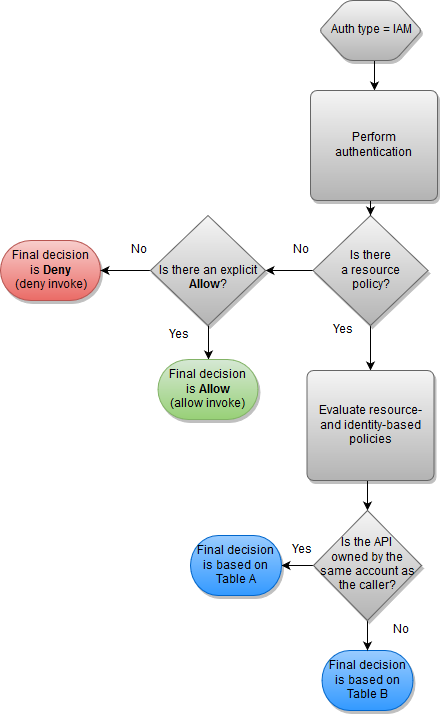
IAM authentication and resource policy
In this workflow, you configure IAM authentication for the API in addition to a resource policy. After you authenticate the user with the IAM service, the API evaluates both the policies attached to the user and the resource policy. The outcome varies based on whether the caller is in the same AWS account or a separate AWS account, from the API owner.
If the caller and API owner are from separate accounts, both the IAM policies and the resource policy explicitly allow the caller to proceed. For more information, see Table B.
However, if the caller and the API owner are in the same AWS account, then either the IAM user policies or the resource policy must explicitly allow the caller to proceed. For more information, see Table A.
The following is an example of a cross-account resource policy. Assuming the IAM policy contains an
allow effect, this resource policy allows calls only from the VPC whose VPC ID is
vpc-2f09a348
Amazon Cognito authentication and resource policy
In this workflow, an Amazon Cognito user pool is configured for the API in addition to a resource policy. API Gateway first attempts to authenticate the caller through Amazon Cognito. This is typically performed through a JWT token that is provided by the caller. If authentication is successful, the resource policy is evaluated independently, and an explicit allow is required. A deny or "neither allow or deny" results in a deny. The following is an example of a resource policy that might be used together with Amazon Cognito user pools.
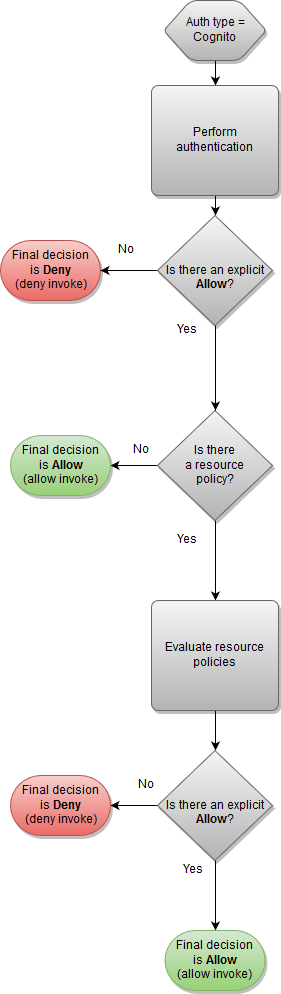
The following is an example of a resource policy that allows calls only from specified source IPs, assuming that the Amazon Cognito authentication token contains an allow. For more information, see Table B.
Policy evaluation outcome tables
Table A lists the resulting behavior when access to an API Gateway API is controlled by an IAM policy or a Lambda authorizer and an API Gateway resource policy, both of which are in the same AWS account.
IAM policy (or Lambda authorizer) |
API Gateway resource policy |
Resulting behavior |
|---|---|---|
| Allow | Allow | Allow |
| Allow | Neither Allow nor Deny | Allow |
| Allow | Deny | Explicit Deny |
| Neither Allow nor Deny | Allow | Allow |
| Neither Allow nor Deny | Neither Allow nor Deny | Implicit Deny |
| Neither Allow nor Deny | Deny | Explicit Deny |
| Deny | Allow | Explicit Deny |
| Deny | Neither Allow nor Deny | Explicit Deny |
| Deny | Deny | Explicit Deny |
Table B lists the resulting behavior when access to an API Gateway API is controlled by an IAM policy or a Amazon Cognito user pools authorizer and an API Gateway resource policy, which are in different AWS accounts. If either is silent (neither allow nor deny), cross-account access is denied. This is because cross-account access requires that both the resource policy and the IAM policy or Amazon Cognito user pools authorizer explicitly grant access.
IAM policy (or Amazon Cognito user pools authorizer) |
API Gateway resource policy |
Resulting behavior |
|---|---|---|
| Allow | Allow | Allow |
| Allow | Neither Allow nor Deny | Implicit Deny |
| Allow | Deny | Explicit Deny |
| Neither Allow nor Deny | Allow | Implicit Deny |
| Neither Allow nor Deny | Neither Allow nor Deny | Implicit Deny |
| Neither Allow nor Deny | Deny | Explicit Deny |
| Deny | Allow | Explicit Deny |
| Deny | Neither Allow nor Deny | Explicit Deny |
| Deny | Deny | Explicit Deny |