Cryptography concepts
As you work with cryptographic tools and services, you are likely to encounter a number of basic concepts.
Topics
- additional authenticated data (AAD)
-
Nonsecret data that is provided to encryption and decryption operations to add an additional integrity and authenticity check on the encrypted data. Typically, the decrypt operation fails if the AAD provided to the encrypt operation does not match the AAD provided to the decrypt operation.
AWS Key Management Service (AWS KMS) and the AWS Encryption SDK both support AAD by using an encryption context.
See also: authenticated encryption
- authenticated encryption
Authenticated encryption uses additional authenticated data (AAD) to provide confidentiality, data integrity, and authenticity assurances on encrypted data.
For example, the AWS Key Management Service (AWS KMS)
EncryptAPI and the encryption methods in the AWS Encryption SDK take an encryption context that represents additional authenticated data (AAD). The encryption context is cryptographically bound to the encrypted data so that the same encryption context is required to decrypt the data. To learn how to use encryption context to protect the integrity of encrypted data, see How to Protect the Integrity of Your Encrypted Data by Using AWS Key Management Service and EncryptionContextin the AWS Security Blog. - asymmetric and symmetric encryption
-
Symmetric encryption uses the same secret key to perform both the encryption and decryption processes.
Asymmetric encryption, also known as public-key encryption, uses two keys, a public key for encryption and a corresponding private key for decryption. The public key and private key are mathematically related so that when the public key is used for encryption, the corresponding private key must be used for decryption. Encryption algorithms are either symmetric or asymmetric.
For more information, see Cryptographic algorithms.
- authentication
-
The process of verifying identity, that is, determining whether an entity is who it claims to be and that the authentication information has not been manipulated by unauthorized entities.
- block cipher
-
An algorithm that operates on fixed-length blocks of data, one block at a time, rather than encrypting one bit at a time as in stream ciphers.
- ciphertext
-
The encrypted data. Ciphertext is typically the output of an encryption algorithm operating on plaintext. Ciphertext is unreadable without knowledge of the algorithm and a secret key.
- client-side and server-side encryption
-
Client-side encryption is encrypting data at or close to its source, such as encrypting data in the application or service that generates it.
Server-side encryption is encrypting data at its destination, that is, the application or service that receives it.
The method that you choose depends on the sensitivity of your data and the security requirements of your application. Client-side and server-side encryption differ in when, where, and who encrypts and decrypts the data. They do not necessarily define how the data is encrypted and might use the same process. In addition, they are not exclusive. You can often use client-side and server-side encryption on the same data.
AWS supports both client-side and server-side encryption. Most AWS services that store or manage customer data offer a server-side encryption option or perform server-side encryption of your data by default. These services transparently encrypt your data before writing it to disk and transparently decrypt it when you access it. Most AWS services that support server-side encryption are integrated with AWS Key Management Service (AWS KMS) to protect the encryption keys that protect your data. For a list of integrated services, see AWS Service Integration
. AWS also supports client-side encryption libraries, such as the AWS Encryption SDK, the AWS Database Encryption SDK, and Amazon S3 client-side encryption. For help choosing the library that best meets your needs, see How to choose a PKI service.
- data key
-
In envelope encryption, a data key or data encryption key is an encryption key that is used to protect data. Data keys differ from root keys and key encryption keys, which are typically used to encrypt other encryption keys.
The term data key usually refers to how the key is used, not how it is constructed. Like all encryption keys, a data key is typically implemented as a byte array that meets the requirements of the encryption algorithm that uses it. As such, data keys can be used to encrypt data or other data keys.
Often a tool or service generates unique data key for each data element, such as a database item, email message, or other resource. Then, it encrypts all of the data keys under the same root key.
Several AWS tools and services provide data keys.
-
The HSMs in a AWS CloudHSM cluster generate encryption keys that can be used as data keys, key encryption keys, or root keys.
-
You can ask AWS Key Management Service (AWS KMS) to generate a data key. It returns a plaintext key and a copy of that key that is encrypted under the KMS keys that you specify.
-
- decryption
-
The process of turning ciphertext back into plaintext. Decryption algorithms typically require an encryption key and can require other inputs, such as initialization vectors (IVs) and additional authenticated data (AAD).
- encryption
-
The process of converting plaintext readable data to an unreadable form, known as ciphertext, to protect it. The formula used to encrypt the data, known as an encryption algorithm, must be almost impossible (using current and anticipated technology) to reverse without knowledge of the inputs to the algorithm. These inputs can include an encryption key and other random and determined data.
All of the cryptographic services and tools that AWS supports provide methods for you to encrypt and decrypt your data. Other AWS services automatically and transparently encrypt the data that they store and manage for you.
- encryption algorithm
-
A procedure or ordered set of instructions that specifies precisely how plaintext data is transformed into encrypted data or ciphertext. The input to an encryption algorithms includes the plaintext data and a encryption key. The output includes the ciphertext.
For example, AWS Key Management Service (AWS KMS) uses the Advanced Encryption Standard (AES)
symmetric algorithm in Galois/Counter Mode (GCM) , known as AES-GCM. AWS CloudHSM supports keys for multiple encryption algorithms. - encryption context
-
A type of additional authenticated data (AAD). It typically consists of nonsecret, arbitrary, name–value pairs. In most cases, you can provide an encryption context when you encrypt data. The same encryption context must be provided to decrypt the data. The encryption context is usually optional but recommended.
The term encryption context has different meanings in various AWS services and tools. This can be confusing, so be sure to understand how your tool or service interprets this term.
The following tools and services support an encryption context.
-
In AWS Key Management Service (AWS KMS), an encryption context is a collection of nonsecret name–value pairs. When you provide an encryption context to an encryption operation, AWS KMS binds it cryptographically to the ciphertext. To decrypt the data, you must provide an exact, case-sensitive match for the encryption context.
AWS KMS includes the encryption context in AWS CloudTrail logs of cryptographic operations. As such, you can use a well-designed encryption context to help you track and audit the use of your encryption keys for particular projects or types of data.
AWS KMS also lets you use all or part of the encryption context as the condition for a permission in a policy or grant. For example, you can allow a user to use a root key to decrypt data only when the encryption context includes a particular value.
For details, see Encryption Context in the AWS Key Management Service Developer Guide.
-
The AWS Encryption SDK also supports an optional encryption context in all cryptographic operations.
However, you do not provide the encryption context to the decryption operation. Instead, when it encrypts data, the SDK saves the encryption context (in plaintext) along with the ciphertext in the encrypted message that it returns. When you ask the SDK to decrypt the encrypted message, the SDK uses the encryption context that it saved.
You can still use the encryption context to provide an additional verification of your data. When you decrypt data, you can get and examine the encryption context and return the decrypted data only after verifying that the encryption context has the expected value.
-
The AWS Database Encryption SDK uses encryption context to mean something different from its use in AWS KMS or the AWS Encryption SDK. The DynamoDB encryption context is a collection of information about the table and table item that you pass to a cryptographic materials provider (CMP). It is not related to AAD.
-
- envelope encryption
-
A strategy for protecting the encryption keys that you use to encrypt your data. First, you encrypt plaintext data with a data key. Then, to protect the data key, you encrypt it under another key, known as a key encryption key.
Encrypting the data key is more efficient than reencrypting the data under the new key because it is quicker and produces a much smaller ciphertext.
You can even encrypt the data encryption key under another encryption key and encrypt that encryption key under still another encryption key. But, eventually, one key must remain in plaintext so you can decrypt the keys and your data. This top-level plaintext key encryption key is known as the root key, as shown in the following diagram.
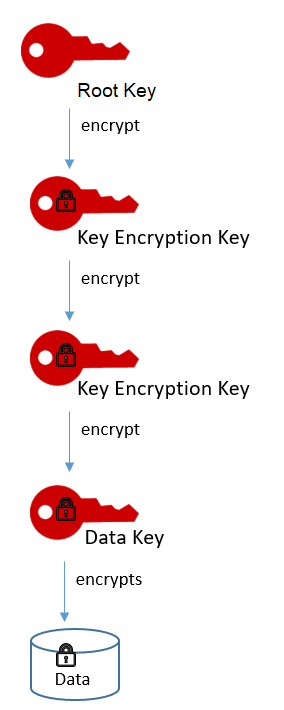
Several AWS cryptographic tools and services support envelope encryption. AWS Key Management Service (AWS KMS) protects the root key that must remain in plaintext. It supplies root keys that never leave the service unencrypted. AWS KMS supports operations that generate data keys that are encrypted under your root key. You can use the data keys to encrypt your data outside of AWS KMS.
The AWS Encryption SDK automatically encrypts your data with a data key that is encrypted by a root key that you specify. The AWS Database Encryption SDK supports many encryption strategies, including envelope encryption with a KMS key or with keys that you provide.
- hardware security module (HSM)
-
A computing device that performs cryptographic operations and provides secure storage for cryptographic keys. Many HSMs have features that make them resistant to tampering or provide reliable tamper detection.
AWS CloudHSM lets you create, manage, and control your own HSMs in the cloud. AWS Key Management Service (AWS KMS) generates and protects the KMS keys that it provides in FIPS 140-2 validated HSMs that it manages for you. AWS KMS also lets you create your KMS keys in a custom key store backed by an AWS CloudHSM cluster that you own and manage.
- key encryption key
-
In envelope encryption, a key encryption key is an encryption key that is used to encrypt a data key or another key encryption key. To protect the key encryption key, it is encrypted by using a root key.
The term key encryption key refers to how the key is used, not how it is constructed. Like all encryption keys, a key encryption key is typically implemented as a byte array that meets the requirements of the encryption algorithm that uses it.
Several AWS services provide key encryption keys.
-
The HSMs in a AWS CloudHSM cluster generate encryption keys that can be used as data keys, key encryption keys, or root keys.
-
You can ask AWS Key Management Service (AWS KMS) to generate a data key, then use that key as a key encryption key outside of AWS KMS.
-
- plaintext
-
Information or data in an unencrypted, unprotected, or human-readable form.
See also: ciphertext.
- private key
-
One of two keys, along with public keys, used to protect data in an asymmetric encryption scheme. Public and private keys are algorithmically generated in tandem: the public key is distributed to multiple trusted entities, and one of its paired private keys is distributed to a single entity. This way, a message can be authenticated because the public key signature proves that a trusted entity encrypted and sent it. The message contents can also be secured so that only a private key holder can decrypt it.
- public key
-
One of two keys, along with private keys, used to protect data in an asymmetric encryption scheme. Public and private keys are algorithmically generated in tandem: the public key is distributed to multiple trusted entities, and one of its paired private keys is distributed to a single entity. This way, a message can be authenticated because the public key signature proves that a trusted entity encrypted and sent it. The message contents can also be secured so that only a private key holder can decrypt it.
- root key
-
In envelope encryption, a root key is an encryption key that is used to encrypt other encryption keys, such as data keys and key encryption keys. Unlike data keys and key encryption keys, root keys must be kept in plaintext so they can be used to decrypt the keys that they encrypted.
The term root key usually refers to how the key is used, not how it is constructed. Like all encryption keys, a root key is typically implemented as a byte array that meets the requirements of the encryption algorithm that uses it.
AWS Key Management Service (AWS KMS) generates and protect root keys. Its KMS keys are created, managed, used, and deleted entirely within AWS KMS.
Several AWS services provide root keys.
-
The HSMs in a AWS CloudHSM cluster generate encryption keys that can be used as data keys, key encryption keys, or root keys.
-
AWS Key Management Service (AWS KMS) generates and protects root keys. Its KMS keys are created, managed, used, and deleted entirely within AWS KMS.
-
- stream cipher
-
An algorithm that operates one bit of a data at a time rather than encrypting one block of data at a time as in block ciphers.