Les traductions sont fournies par des outils de traduction automatique. En cas de conflit entre le contenu d'une traduction et celui de la version originale en anglais, la version anglaise prévaudra.
Détails des composants
Comme décrit dans le schéma d'architecture, quatre des composants de cette solution utilisent des automatisations pour inspecter les adresses IP et les ajouter à la liste de blocage d'AWS WAF. Les sections suivantes expliquent chacun de ces composants de manière plus détaillée.
Log parser - Application
L'analyseur du journal des applications permet de se protéger contre les scanners et les sondes.
Flux de l'analyseur du journal des applications.
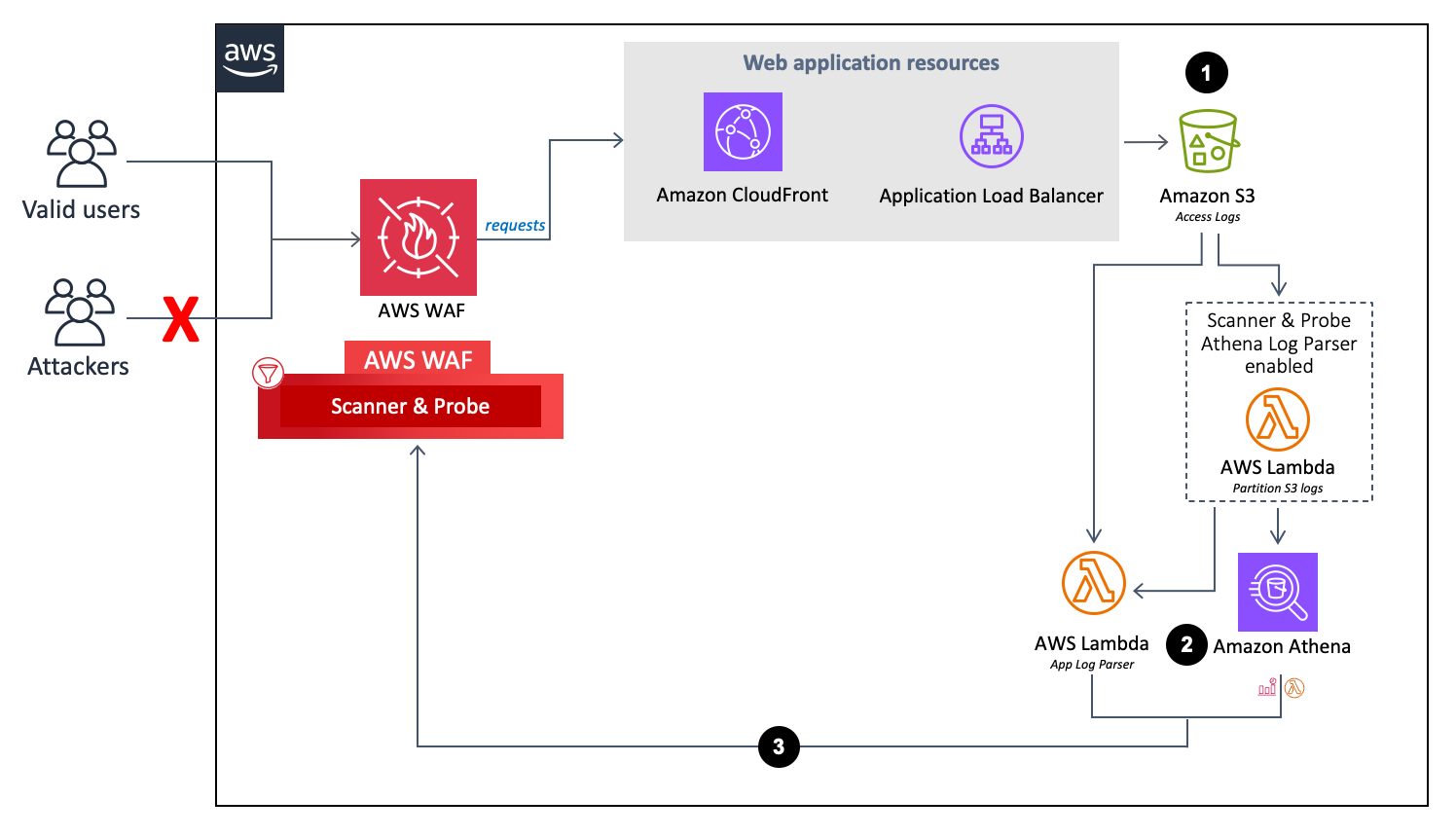
-
Lorsqu' CloudFront un ALB reçoit des demandes au nom de votre application Web, il envoie des journaux d'accès à un compartiment Amazon S3.
-
(Facultatif) Si vous sélectionnez
Yes - Amazon Athena log parsercomme paramètres du modèle Activate HTTP Flood Protection et Activate Scanner & Probe Protection, une fonction Lambda déplace les journaux d'accès de leur dossier d'origine<customer-bucket>/AWSLogsvers un dossier nouvellement<customer-bucket>/AWSLogs-partitioned/<optional-prefix>/year=<YYYY>/month=<MM>/day=<DD>/hour=<HH>partitionné/ à leur arrivée dans Amazon S3. -
(Facultatif) Si vous sélectionnez
yesle paramètre Conserver les données dans l'emplacement S3 d'origine, les journaux restent dans leur emplacement d'origine et sont copiés dans leur dossier partitionné, dupliquant ainsi votre stockage de journaux.Note
Pour l'analyseur de journaux Athena, cette solution partitionne uniquement les nouveaux journaux qui arrivent dans votre compartiment Amazon S3 après le déploiement de cette solution. Si vous souhaitez partitionner des journaux existants, vous devez les charger manuellement sur Amazon S3 après avoir déployé cette solution.
-
-
En fonction de votre sélection pour les paramètres du modèle Activate HTTP Flood Protection et Activate Scanner & Probe Protection, cette solution traite les journaux en utilisant l'une des méthodes suivantes :
-
Lambda - Chaque fois qu'un nouveau journal d'accès est stocké dans le compartiment Amazon S3, la fonction
Log ParserLambda est lancée. -
Athena - Par défaut, toutes les cinq minutes, la requête Athena de Scanner & Probe Protection est exécutée et le résultat est envoyé vers AWS WAF. Ce processus est initié par un CloudWatch événement qui lance la fonction Lambda chargée d'exécuter la requête Athena et envoie le résultat dans AWS WAF.
-
-
La solution analyse les données du journal pour identifier les adresses IP qui ont généré plus d'erreurs que le quota défini. La solution met ensuite à jour une condition d'ensemble d'adresses IP AWS WAF afin de bloquer ces adresses IP pendant une période définie par le client.
Analyseur de journaux - AWS WAF
Si vous sélectionnez yes - AWS Lambda log parser ou yes - Amazon Athena log parser pour Activer la protection HTTP contre les inondations, cette solution fournit les composants suivants, qui analysent les journaux AWS WAF afin d'identifier et de bloquer les origines qui inondent le point de terminaison avec un taux de demandes supérieur au quota que vous avez défini.
Flux de l'analyseur de journaux AWS WAF.
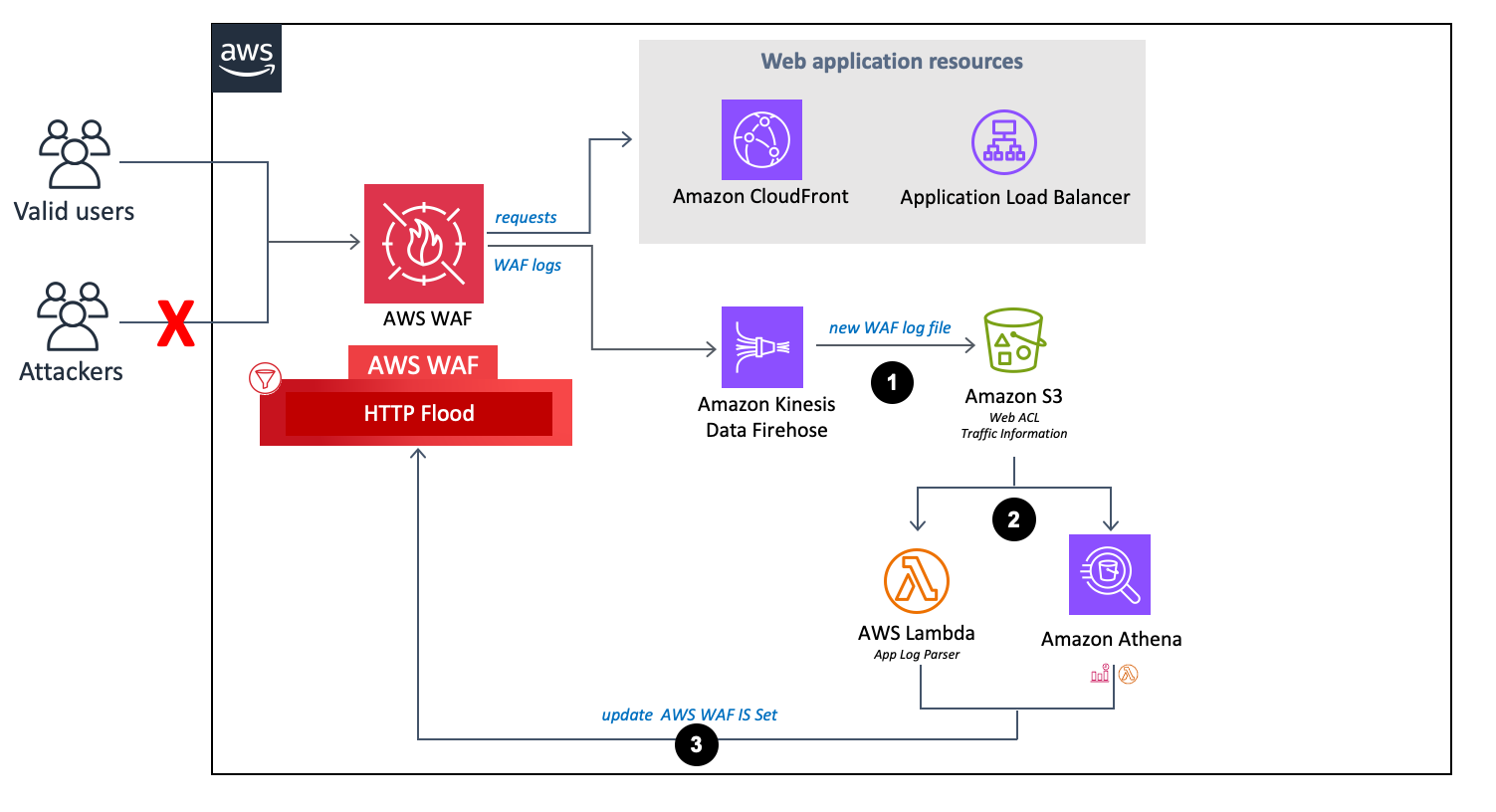
-
Lorsqu'AWS WAF reçoit des journaux d'accès, il les envoie à un point de terminaison Firehose. Firehose envoie ensuite les journaux dans un compartiment partitionné dans Amazon S3 nommé
<customer-bucket>/AWSLogs/<optional-prefix>/year=<YYYY>/month=<MM>/day=<DD>/hour=<HH>/ -
En fonction de votre sélection pour les paramètres du modèle Activate HTTP Flood Protection et Activate Scanner & Probe Protection, cette solution traite les journaux en utilisant l'une des méthodes suivantes :
-
Lambda : chaque fois qu'un nouveau journal d'accès est stocké dans le compartiment Amazon S3, la fonction
Log ParserLambda est lancée. -
Athena : Par défaut, toutes les cinq minutes, la requête Athena du scanner et de la sonde est exécutée et le résultat est transféré vers AWS WAF. Ce processus est initié par un CloudWatch événement Amazon, qui lance ensuite la fonction Lambda chargée d'exécuter la requête Amazon Athena et envoie le résultat dans AWS WAF.
-
-
La solution analyse les données du journal pour identifier les adresses IP qui ont envoyé plus de demandes que le quota défini. La solution met ensuite à jour une condition d'ensemble d'adresses IP AWS WAF afin de bloquer ces adresses IP pendant une période définie par le client.
Log parser - Mauvais robot
L'analyseur de log Bad bot inspecte les requêtes adressées au point de terminaison Honeypot pour en extraire l'adresse IP source.
Le flux de l'analyseur de journal des bots est incorrect.
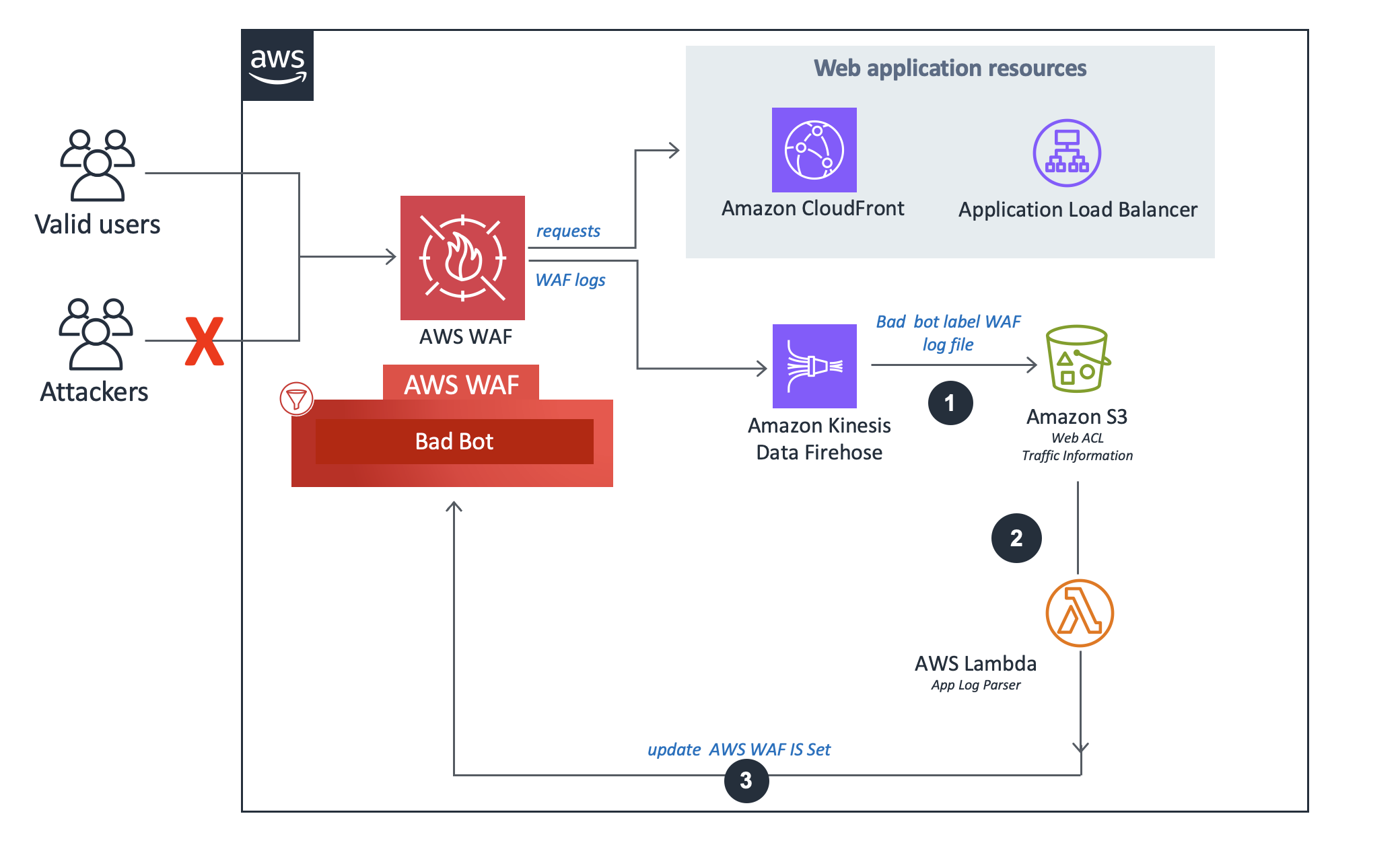
-
S'il
Bad Bot Protectionest activé et que les fonctionnalités de protection contre les inondations HTTP et de protection contre les scanners et les sondes sont désactivées : le système utilisera l'analyseur Log Lambda, qui enregistre uniquement les mauvaises requêtes de bot sur la base des filtres d'étiquettes WAF. -
La fonction Lambda intercepte et inspecte les en-têtes de requête pour extraire l'adresse IP de la source qui a accédé au point de terminaison du trap.
-
La solution analyse les données du journal pour identifier les adresses IP qui ont envoyé plus de demandes que le quota défini. La solution met ensuite à jour une condition d'ensemble d'adresses IP AWS WAF afin de bloquer ces adresses IP pendant une période définie par le client.
Analyseur de listes IP
La fonction IP Lists Parser Lambda permet de se protéger contre les attaquants connus identifiés dans les listes de réputation IP tierces.
La réputation IP répertorie les flux d'analyseurs.
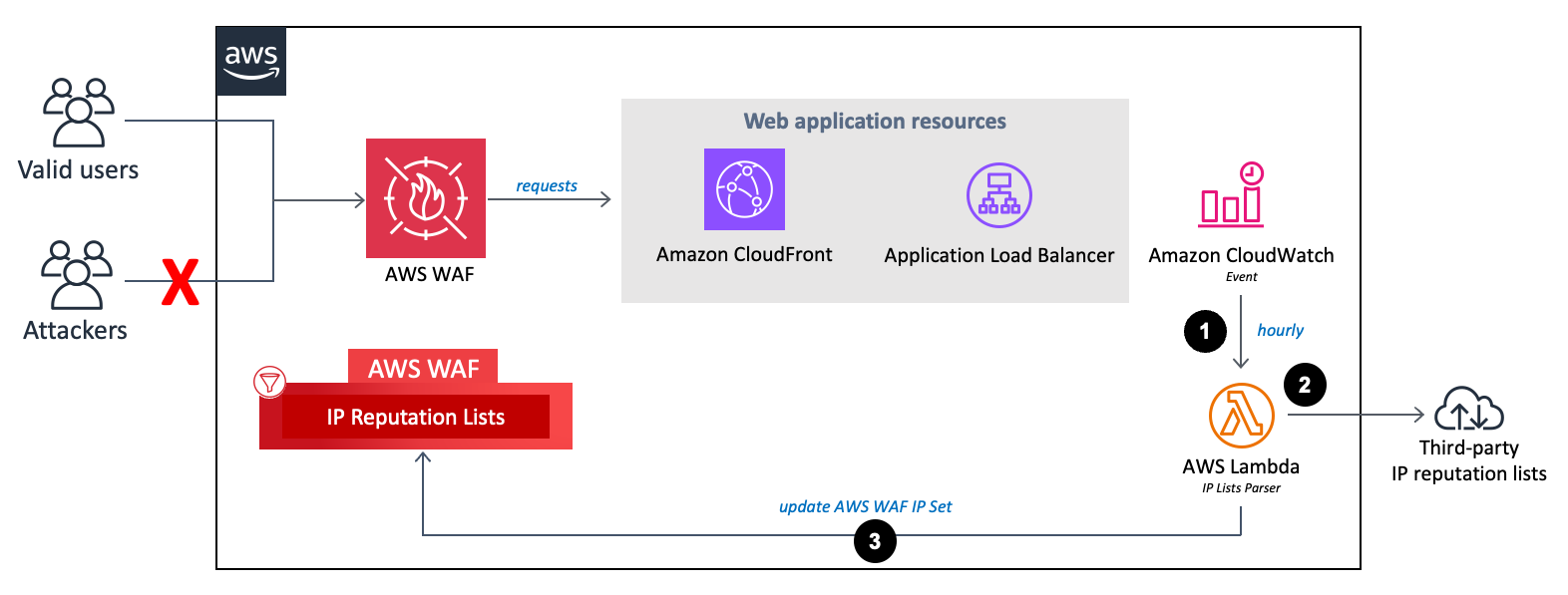
-
Un CloudWatch événement Amazon horaire appelle la fonction
IP Lists ParserLambda. -
La fonction Lambda collecte et analyse les données provenant de trois sources :
-
Listes DROP et EDROP de Spamhaus
-
Liste des adresses IP des menaces émergentes de Proofpoint
-
Liste des nœuds de sortie de Tor
-
-
La fonction Lambda met à jour la liste de blocage AWS WAF avec les adresses IP actuelles.