Le traduzioni sono generate tramite traduzione automatica. In caso di conflitto tra il contenuto di una traduzione e la versione originale in Inglese, quest'ultima prevarrà.
Dettagli dei componenti
Come descritto nel diagramma dell'architettura, quattro componenti di questa soluzione utilizzano automazioni per ispezionare gli indirizzi IP e aggiungerli alla lista di blocco di AWS WAF. Le seguenti sezioni spiegano ciascuno di questi componenti in modo più dettagliato.
Log parser - Applicazione
Il parser dei registri dell'applicazione aiuta a proteggere da scanner e sonde.
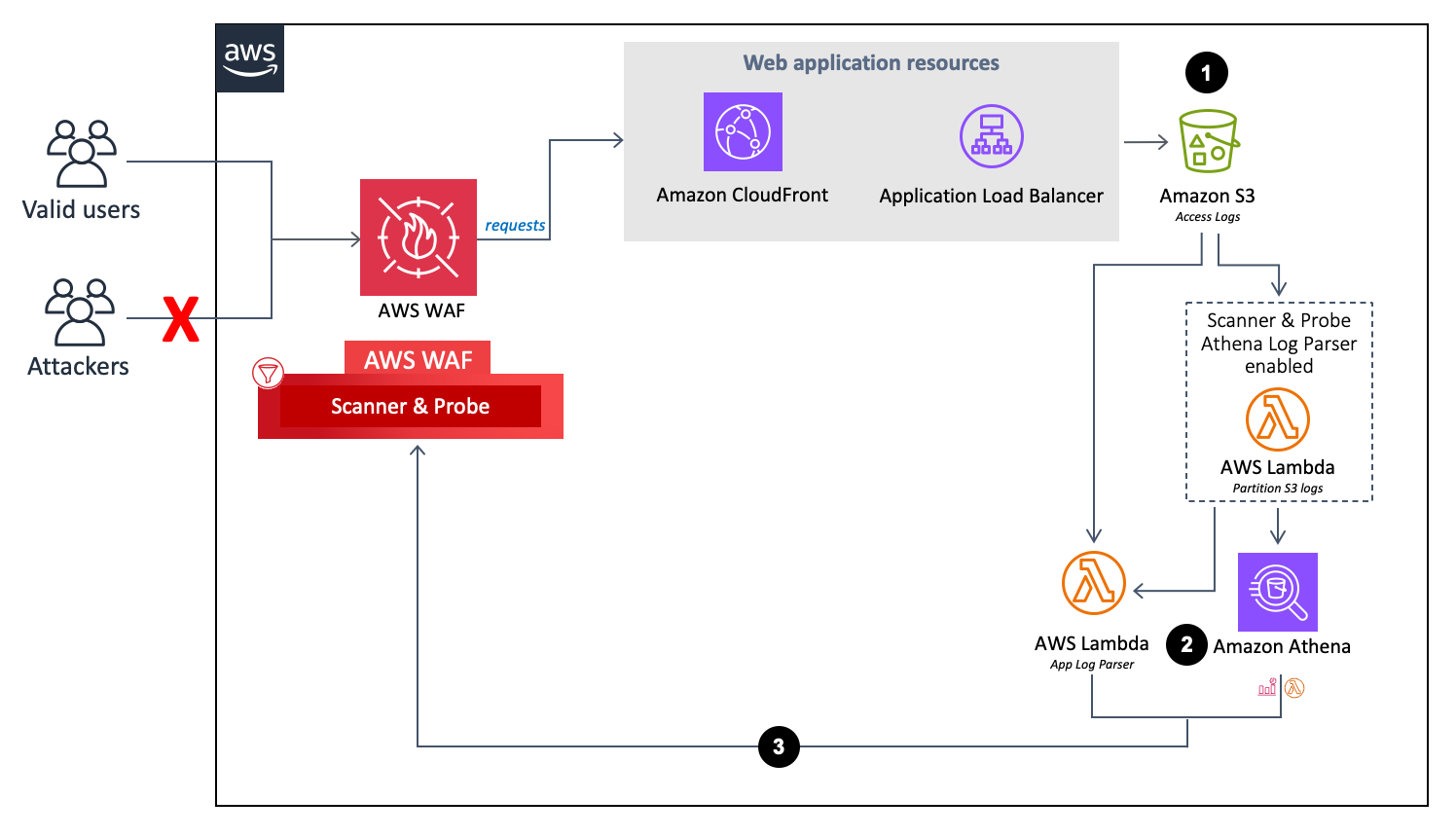
Flusso del parser del registro dell'applicazione.
-
Quando CloudFront un ALB riceve richieste per conto della tua applicazione Web, invia i log di accesso a un bucket Amazon S3.
-
(Facoltativo) Se si seleziona
Yes - Amazon Athena log parserper i parametri del modello Activate HTTP Flood Protection e Activate Scanner & Probe Protection, una funzione Lambda sposta i log di accesso dalla cartella originale<customer-bucket>/AWSLogsa una cartella appena partizionata/al<customer-bucket>/AWSLogs-partitioned/<optional-prefix>/year=<YYYY>/month=<MM>/day=<DD>/hour=<HH>loro arrivo in Amazon S3. -
(Facoltativo) Se si seleziona
yesil parametro del modello di posizione Keep Data in Original S3, i log rimangono nella posizione originale e vengono copiati nella cartella partizionata, duplicando lo spazio di archiviazione dei log.Nota
Per il parser di log Athena, questa soluzione partiziona solo i nuovi log che arrivano nel bucket Amazon S3 dopo aver distribuito questa soluzione. Se disponi di log esistenti che desideri partizionare, devi caricarli manualmente su Amazon S3 dopo aver distribuito questa soluzione.
-
-
In base alla selezione dei parametri del modello Activate HTTP Flood Protection e Activate Scanner & Probe Protection, questa soluzione elabora i log utilizzando uno dei seguenti metodi:
-
Lambda: ogni volta che un nuovo log di accesso viene archiviato nel bucket Amazon S3, viene avviata
Log Parserla funzione Lambda. -
Athena - Per impostazione predefinita, ogni cinque minuti viene eseguita la query Athena di Scanner & Probe Protection e l'output viene inviato ad AWS WAF. Questo processo viene avviato da un CloudWatch evento che avvia la funzione Lambda responsabile dell'esecuzione della query Athena e invia il risultato in AWS WAF.
-
-
La soluzione analizza i dati di registro per identificare gli indirizzi IP che hanno generato più errori rispetto alla quota definita. La soluzione aggiorna quindi una condizione del set di IP AWS WAF per bloccare tali indirizzi IP per un periodo di tempo definito dal cliente.
Analizzatore di log - AWS WAF
Se selezioni yes - AWS Lambda log parser o yes - Amazon Athena log parser per Activate HTTP Flood Protection, questa soluzione fornisce i seguenti componenti, che analizzano i log di AWS WAF per identificare e bloccare le origini che inondano l'endpoint con una frequenza di richiesta superiore alla quota definita.
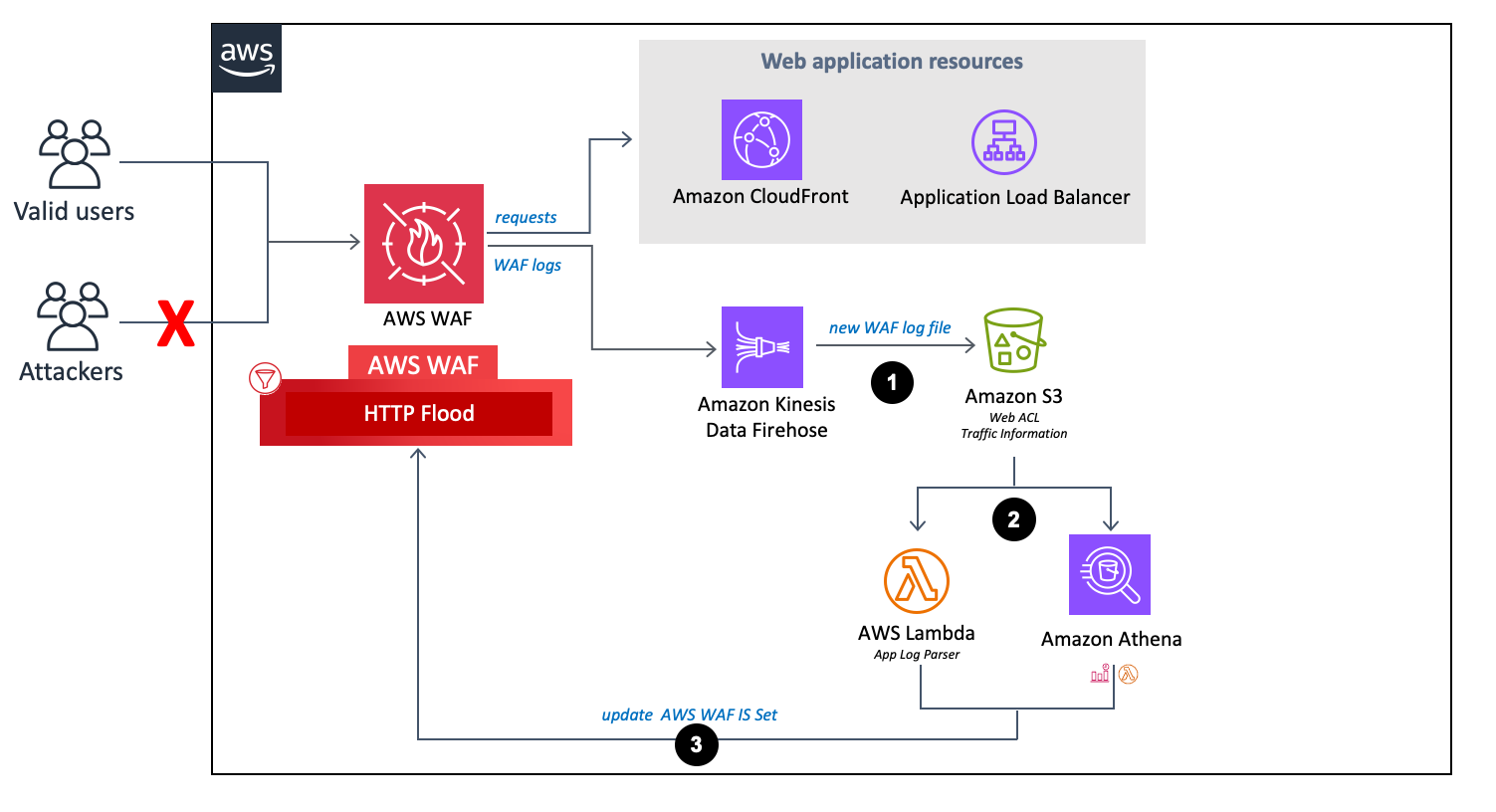
Flusso del parser di log AWS WAF.
-
Quando AWS WAF riceve i log di accesso, li invia a un endpoint Firehose. Firehose invia quindi i log a un bucket partizionato in Amazon S3 denominato
<customer-bucket>/AWSLogs/<optional-prefix>/year=<YYYY>/month=<MM>/day=<DD>/hour=<HH>/ -
In base alla selezione effettuata per i parametri del modello Activate HTTP Flood Protection e Activate Scanner & Probe Protection, questa soluzione elabora i log utilizzando uno dei seguenti strumenti:
-
Lambda: ogni volta che un nuovo log di accesso viene archiviato nel bucket Amazon S3, viene avviata
Log Parserla funzione Lambda. -
Athena: per impostazione predefinita, ogni cinque minuti viene eseguita la query Athena dello scanner e della sonda e l'output viene inviato ad AWS WAF. Questo processo viene avviato da un CloudWatch evento Amazon, che avvia quindi la funzione Lambda responsabile dell'esecuzione della query Amazon Athena e invia il risultato in AWS WAF.
-
-
La soluzione analizza i dati di registro per identificare gli indirizzi IP che hanno inviato più richieste rispetto alla quota definita. La soluzione aggiorna quindi una condizione del set di IP AWS WAF per bloccare tali indirizzi IP per un periodo di tempo definito dal cliente.
Log parser - Bot non valido
Il parser di log Bad bot esamina le richieste all'endpoint honeypot per estrarne l'indirizzo IP di origine.
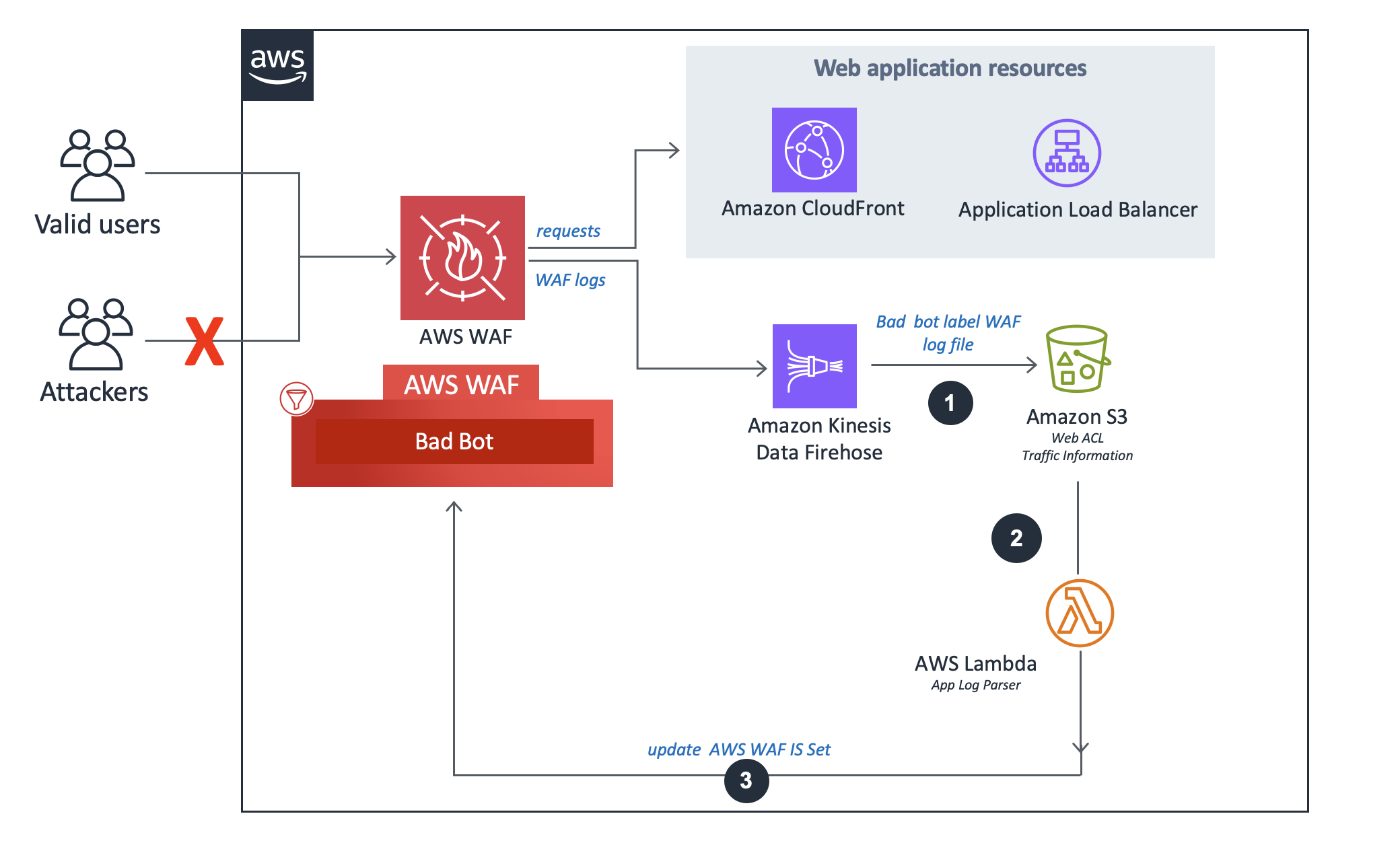
Flusso del parser del registro di avvio errato.
-
La funzione Lambda intercetta e ispeziona le intestazioni delle richieste per estrarre l'indirizzo IP della fonte che ha avuto accesso all'endpoint trap.
-
La soluzione analizza i dati di registro per identificare gli indirizzi IP che hanno inviato più richieste rispetto alla quota definita. La soluzione aggiorna quindi una condizione del set di IP AWS WAF per bloccare tali indirizzi IP per un periodo di tempo definito dal cliente.
Analizzatore di elenchi IP
La funzione IP Lists Parser Lambda aiuta a proteggere dagli aggressori noti identificati negli elenchi di reputazione IP di terze parti.
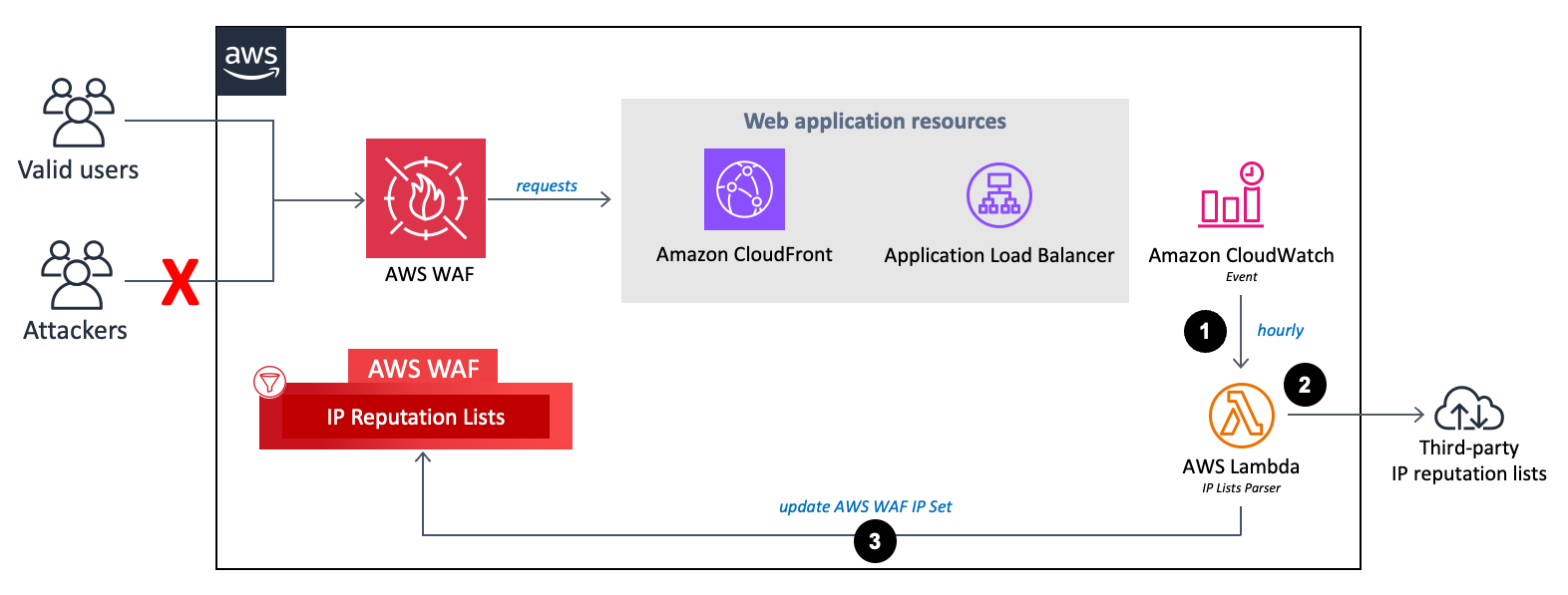
La reputazione IP elenca i flussi del parser.
-
Un CloudWatch evento Amazon ogni ora richiama la funzione
IP Lists ParserLambda. -
La funzione Lambda raccoglie e analizza i dati da tre fonti:
-
Elenchi Spamhaus DROP e EDROP
-
Elenco IP Proofpoint Emerging Threats
-
Elenco dei nodi di uscita Tor
-
-
La funzione Lambda aggiorna l'elenco di blocchi di AWS WAF con gli indirizzi IP correnti.