기계 번역으로 제공되는 번역입니다. 제공된 번역과 원본 영어의 내용이 상충하는 경우에는 영어 버전이 우선합니다.
아키텍처 개요
이 섹션에서는 이 솔루션과 함께 배포된 구성 요소에 대한 참조 구현 아키텍처 다이어그램을 제공합니다.
아키텍처 다이어그램
기본 파라미터를 사용하여이 솔루션을 배포하면 AWS 계정에 다음 구성 요소가 배포됩니다.
CloudFormation 템플릿은 AWS WAF 및 기타 AWS 리소스를 배포하여 일반적인 공격으로부터 웹 애플리케이션을 보호합니다.
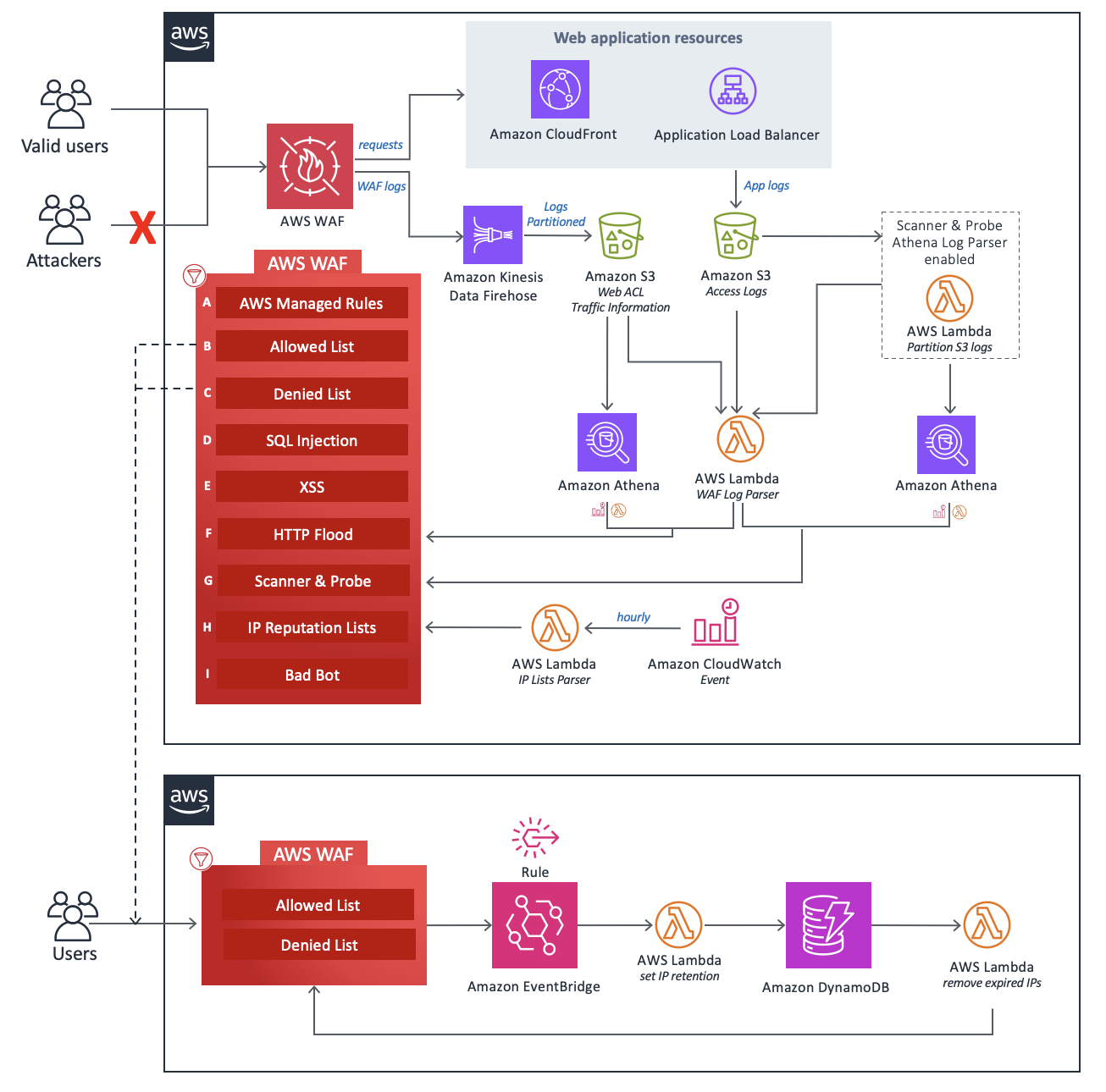
설계의 핵심은 웹 애플리케이션에 대한 모든 수신 요청에 대한 중앙 검사 및 결정 지점 역할을 하는 AWS WAF
이 솔루션의 구성 요소는 다음과 같은 보호 영역으로 그룹화할 수 있습니다.
참고
그룹 레이블은 WAF 규칙의 우선 순위 수준을 반영하지 않습니다.
-
AWS 관리형 규칙(A) -이 구성 요소에는 AWS 관리형 규칙 IP 평판 규칙 그룹, 기준 규칙 그룹 및 사용 사례별 규칙 그룹이 포함되어 있습니다. 이러한 규칙 그룹은 자체 규칙을 작성할 필요 없이 OWASP
간행물에 설명된 트래픽을 포함하여 일반적인 애플리케이션 취약성 또는 기타 원치 않는 트래픽의 악용으로부터 보호합니다. -
수동 IP 목록(B 및 C) - 이러한 구성 요소는 두 개의 AWS WAF 규칙을 생성합니다. 이러한 규칙을 사용하면 허용하거나 거부할 IP 주소를 수동으로 삽입할 수 있습니다. Amazon EventBridge 규칙 및 Amazon
DynamoDB를 사용하여 허용되거나 거부된 IP 세트에서 IP 보존을 구성하고 만료된 IP 주소를 제거할 수 있습니다 . https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-rules.html 자세한 내용은 허용 및 거부된 AWS WAF IP 세트에서 IP 보존 구성을 참조하세요. -
SQL Injection(D) 및 XSS(E) - 이러한 구성 요소는 URI, 쿼리 문자열 또는 요청 본문의 일반적인 SQL 삽입 또는 교차 사이트 스크립팅(XSS) 패턴으로부터 보호하도록 설계된 두 가지 AWS WAF 규칙을 구성합니다.
-
HTTP Flood(F) -이 구성 요소는 웹 계층 DDoS 공격 또는 무차별 대입 로그인 시도와 같은 특정 IP 주소의 많은 요청으로 구성된 공격으로부터 보호합니다. 이 규칙을 사용하면 기본 5분 기간 내에 단일 IP 주소에서 허용되는 최대 수신 요청 수를 정의하는 할당량을 설정합니다(Athena 쿼리 실행 시간 일정 파라미터로 구성 가능). 이 임계값을 위반하면 IP 주소의 추가 요청이 일시적으로 차단됩니다. AWS WAF 속도 기반 규칙을 사용하거나 Lambda 함수 또는 Athena 쿼리를 사용하여 AWS WAF 로그를 처리하여이 규칙을 구현할 수 있습니다. HTTP flood 완화 옵션과 관련된 장단점에 대한 자세한 내용은 로그 구문 분석기 옵션을 참조하세요.
-
스캐너 및 프로브(G) -이 구성 요소는 오리진에서 생성된 비정상적인 양의 오류와 같은 의심스러운 동작을 검색하는 애플리케이션 액세스 로그를 구문 분석합니다. 그런 다음 고객이 정의한 기간 동안 의심스러운 소스 IP 주소를 차단합니다. Lambda
함수 또는 Athena 쿼리를 사용하여이 규칙을 구현할 수 있습니다. 스캐너 및 프로브 완화 옵션과 관련된 장단점에 대한 자세한 내용은 로그 구문 분석기 옵션을 참조하세요. -
IP 평판 목록(H) -이 구성 요소는 차단할 새 범위에 대해 서드 파티 IP 평판 목록을 시간별로 확인하는
IP Lists ParserLambda 함수입니다. 이러한 목록에는 Spamhaus Don't Route Or Peer(DROP) 및 Extended DROP(EDROP) 목록, Proofpoint Emerging Threats IP 목록 및 Tor 출구 노드 목록이 포함됩니다. -
잘못된 봇(I) -이 구성 요소는 허니팟 메커니즘 외에도 Application Load Balancer(ALB) 또는 Amazon CloudFront에 대한 직접 연결을 모니터링하여 잘못된 봇 탐지를 개선합니다. 봇이 허니팟을 우회하고 ALB 또는 CloudFront와 상호 작용하려고 하면 시스템은 요청 패턴 및 로그를 분석하여 악의적인 활동을 식별합니다. 잘못된 봇이 감지되면 IP 주소가 추출되어 AWS WAF 블록 목록에 추가되어 추가 액세스를 방지합니다. 잘못된 봇 탐지는 구조화된 로직 체인을 통해 작동하여 포괄적인 위협 범위를 보장합니다.
-
HTTP Flood Protection Lambda 로그 파서 - 플러드 분석 중에 로그 항목에서 잘못된 봇 IPs를 수집합니다.
-
스캐너 및 프로브 보호 Lambda 로그 파서 - 스캐너 관련 로그 항목에서 잘못된 봇 IPs.
-
HTTP Flood Protection Athena Log Parser - 쿼리 실행 전반의 파티션을 사용하여 Athena 로그에서 잘못된 봇 IPs를 추출합니다.
-
스캐너 및 프로브 보호 Athena 로그 파서 - 동일한 파티셔닝 전략을 사용하여 스캐너 관련 Athena 로그에서 잘못된 봇 IPs를 검색합니다.
-
폴백 감지 - HTTP Flood Protection과 스캐너 및 프로브 보호가 모두 비활성화된 경우 시스템은 WAF 레이블 필터를 기반으로 봇 활동을 기록하는 Log Lambda 구문 분석기를 사용합니다.
-
이 솔루션의 세 가지 사용자 지정 Lambda 함수는 각각 CloudWatch에 런타임 지표를 게시합니다. 이러한 Lambda 함수에 대한 자세한 내용은 구성 요소 세부 정보를 참조하세요.