Note
End of support notice: On May 1, 2025, AWS Launch Wizard will discontinue support for Amazon Elastic Kubernetes Service, Microsoft Internet Information Services, and Microsoft Exchange Server. After May 1, 2025, you can no longer use AWS Launch Wizard to access these workloads.
The following are post-deployment steps for Internet Information Services (IIS) with AWS Launch Wizard.
Topics
(Optional) Run Windows Updates
To help ensure that the deployed servers' operating systems and installed applications have the latest Microsoft updates, run Windows Update on each server.
Run Windows Updates on your RD Gateways using public IP addresses
To run Windows updates on the RD Gateways with their public IP addresses:
-
Identify the public IP addresses for the RD Gateways, from the Amazon EC2 console
. -
Use the public IP of the RD Gateway to connect to the instance.
-
On the taskbar, open the Start menu, and choose Settings.
-
In the Settings application, choose Update & Security
-
Choose Check for updates.
-
Install any updates, and restart if necessary.
Run Windows Updates on your IIS servers by connecting through an RD Gateway or public bastion
To run Windows updates on the IIS servers by connecting from within a public resource such as an RD Gateway or bastion host:
-
Identify the public IP addresses for the public resource, and also the private IP addresses of the IIS servers, from the Amazon EC2 console
. -
Use the public IP of the public resource to connect to the instance.
-
From within the RDP connection to the public resource, use the IIS server's private IP addresses when creating subsequent RDP connections.
Note
You will use the nested RDP session within the public resource to the IIS server for the remaining steps.
-
On the taskbar, open the Start menu, and choose Settings.
-
In the Settings application, choose Update & Security
-
Choose Check for updates.
-
Install any updates, and restart if necessary.
Testing the deployment
To test the deployment, ensure that your IP address being used is entered in the
WebAccessCIDR parameter. You can review previously entered
Parameters for the Launch Wizard deployment in the AWS CloudFormation console

Connect to your Windows instances using SSM port
forwarding sessions and RDP
You can connect to your deployed resources by completing some prerequisites for Amazon EC2 Systems Manager and using a port forwarding session for the RDP connection. The port forwarding method doesn't require bastion hosts, or for you to open inbound TCP 3389 connections to your resources.
SSM port forwarding prerequisites
To run Windows updates on the servers with Amazon EC2 Systems Manager and port forwarding for RDP sessions, the following prerequisites are required:
-
The AWS Command Line Interface is installed on your computer opening the port forwarding session.
-
The AWS Command Line Interface (AWS CLI) is configured with security credentials for your AWS account.
-
The Session Manager plugin for AWS CLI is installed.
-
The SSM Agent is installed on your EC2 instances.*
-
An instance profile is attached which allows access to the Amazon EC2 Systems Manager API.*
* These prerequisites are completed automatically as part of the Launch Wizard deployment.
Connect to your resources using SSM port forwarding sessions
The following steps use the AWS CLI to start an SSM Session Manager connection on a specified Amazon EC2 instance and invoke the SSM document AWS-StartPortForwardingSession. This allows an RDP connection from your computer to the target Amazon EC2 instance using the redirected port.
-
You can locate instance IDs to connect to from the Amazon EC2 console
, for example i-1234567890abcdef0. -
Run the following command in the AWS CLI by providing your target instance ID after the
--targetparameter, and a free local port on your computer for thelocalPortNumberaws ssm start-session --target "your-instance-id" --document-name AWS-StartPortForwardingSession --parameters "portNumber"=["3389"],"localPortNumber"=["56788"]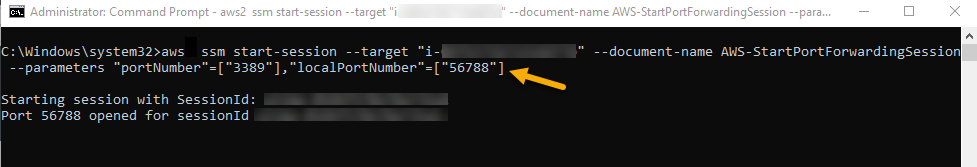
-
When the session is established, open the Remote Desktop application, enter
localhost:, and choose Connect.56788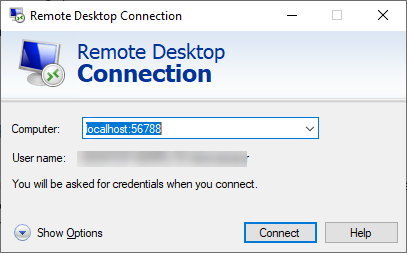
-
Enter the credentials to the Amazon EC2 instance to log in. You can find more information on retrieving the user name and password for your instance here.
-
When finished, you can exit the RDP session and end the AWS CLI session.