Overview of security in Amazon OpenSearch Serverless
Security in Amazon OpenSearch Serverless differs fundamentally from security in Amazon OpenSearch Service in the following ways:
| Feature | OpenSearch Service | OpenSearch Serverless |
|---|---|---|
| Data access control | Data access is determined by IAM policies and fine-grained access control. | Data access is determined by data access policies. |
| Encryption at rest | Encryption at rest is optional for domains. | Encryption at rest is required for collections. |
| Security setup and administration | You must configure network, encryption, and data access individually for each domain. | You can use security policies to manage security settings for multiple collections at scale. |
The following diagram illustrates the security components that make up a functional collection. A collection must have an assigned encryption key, network access settings, and a matching data access policy that grants permission to its resources.

Topics
Encryption policies
Encryption policies define whether your collections are encrypted with an AWS owned key or a customer managed key. Encryption policies consist of two components: a resource pattern and an encryption key. The resource pattern defines which collection or collections the policy applies to. The encryption key determines how the associated collections will be secured.
To apply a policy to multiple collections, you include a wildcard (*) in the policy rule. For example, the following policy applies to all collections with names that begin with "logs".

Encryption policies streamline the process of creating and managing collections, especially when you do so programmatically. You can create a collection by specifying a name, and an encryption key is automatically assigned to it upon creation.
Network policies
Network policies define whether your collections are accessible privately, or over the internet from public networks. Private collections can be accessed through OpenSearch Serverless–managed VPC endpoints, or by specific AWS services such as Amazon Bedrock using AWS service private access. Just like encryption policies, network policies can apply to multiple collections, which allows you to manage network access for many collections at scale.
Network policies consist of two components: an access type and a resource type. The access type can either be public or private. The resource type determines whether the access you choose applies to the collection endpoint, the OpenSearch Dashboards endpoint, or both.

If you plan to configure VPC access within a network policy, you must first create one or more OpenSearch Serverless-managed VPC endpoints. These endpoints let you access OpenSearch Serverless as if it were in your VPC, without the use of an internet gateway, NAT device, VPN connection, or Direct Connect connection.
Private access to AWS services can only apply to the collection's OpenSearch endpoint, not to the OpenSearch Dashboards endpoint. AWS services cannot be granted access to OpenSearch Dashboards.
Data access policies
Data access policies define how your users access the data within your collections. Data access policies help you manage collections at scale by automatically assigning access permissions to collections and indexes that match a specific pattern. Multiple policies can apply to a single resource.
Data access policies consist of a set of rules, each with three components: a resource type, granted resources, and a set of permissions. The resource type can be a collection or index. The granted resources can be collection/index names or patterns with a wildcard (*). The list of permissions specifies which OpenSearch API operations the policy grants access to. In addition, the policy contains a list of principals, which specify the IAM roles, users, and SAML identities to grant access to.
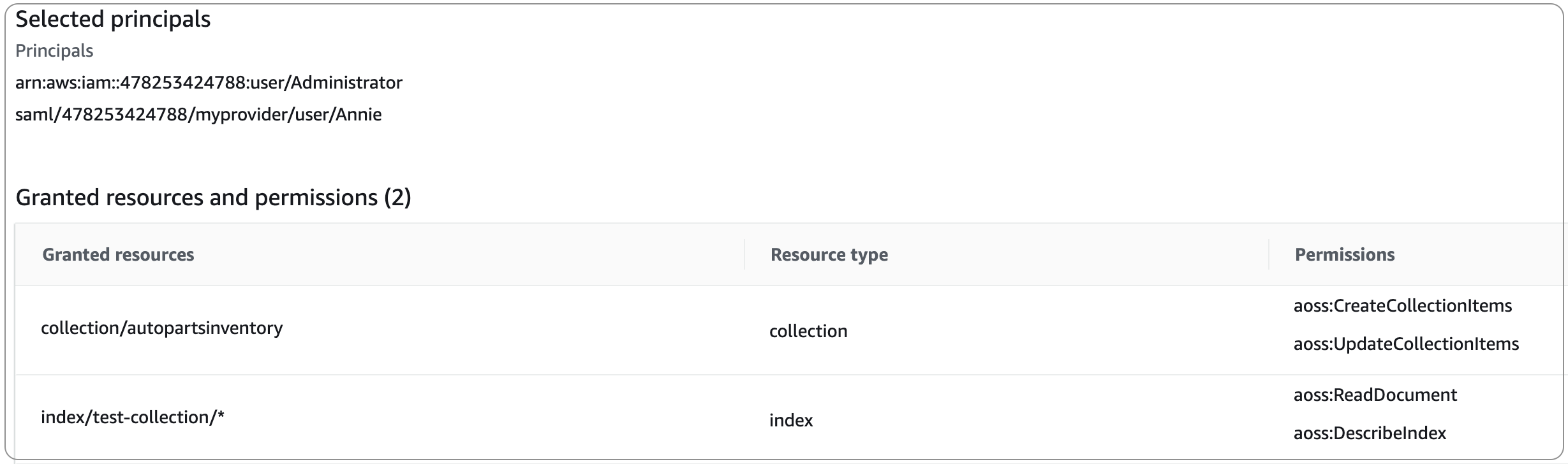
For more information about the format of a data access policy, see the policy syntax.
Before you create a data access policy, you must have one or more IAM roles or users, or SAML identities, to provide access to in the policy. For details, see the next section.
Note
Switching from Public to Private Access for your collection, will remove the Indexes Tab in the OpenSearch Serverless Collection Console.
IAM and SAML authentication
IAM principals and SAML identities are one of the building blocks of a data access
policy. Within the principal statement of an access policy, you can include
IAM roles, users, and SAML identities. These principals are then granted the
permissions that you specify in the associated policy rules.
[ { "Rules":[ { "ResourceType":"index", "Resource":[ "index/marketing/orders*" ], "Permission":[ "aoss:*" ] } ], "Principal":[ "arn:aws:iam::123456789012:user/Dale", "arn:aws:iam::123456789012:role/RegulatoryCompliance", "saml/123456789012/myprovider/user/Annie" ] } ]
You configure SAML authentication directly within OpenSearch Serverless. For more information, see SAML authentication for Amazon OpenSearch Serverless.
Infrastructure security
Amazon OpenSearch Serverless is protected by AWS global network security. For information about AWS
security services and how AWS protects infrastructure, see AWS Cloud Security
You use AWS published API calls to access Amazon OpenSearch Serverless through the network. Clients must support Transport Layer Security (TLS). We require TLS 1.2 and recommend TLS 1.3. For a list of supported ciphers for TLS 1.3, see TLS protocols and ciphers in the Elastic Load Balancing documentation.
Additionally, you must sign requests using an access key ID and a secret access key that is associated with an IAM principal. Or you can use the AWS Security Token Service (AWS STS) to generate temporary security credentials to sign requests.