As traduções são geradas por tradução automática. Em caso de conflito entre o conteúdo da tradução e da versão original em inglês, a versão em inglês prevalecerá.
Criar sinalizadores de recurso multivariante
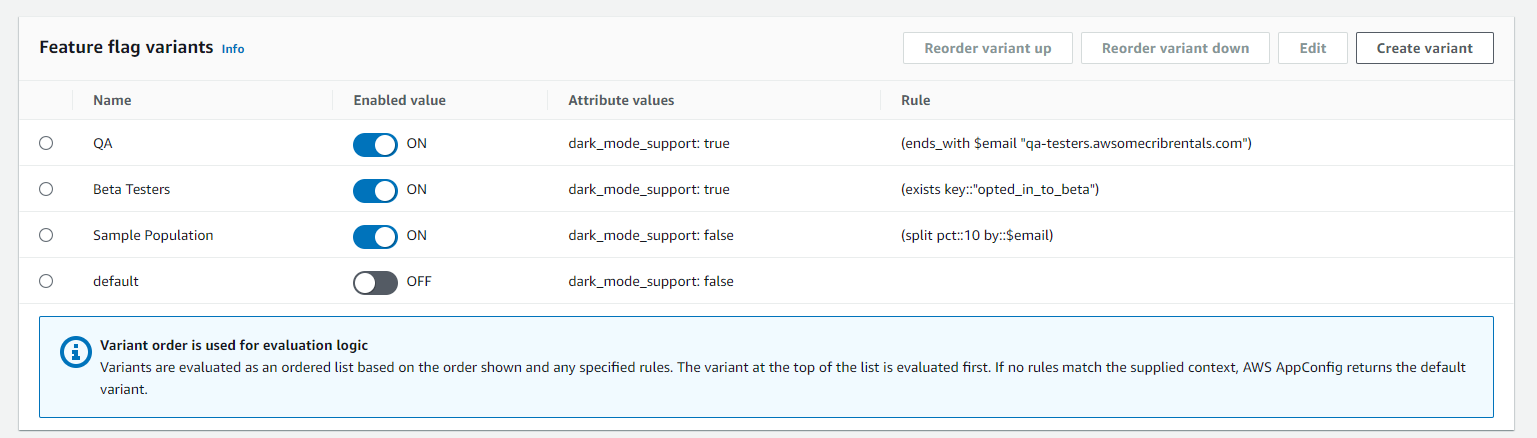
As variantes de sinalizador de recurso permitem definir um conjunto de possíveis valores de sinalizador a serem exibidos para uma solicitação. Também é possível configurar diferentes status (habilitado ou desabilitado) para sinalizadores multivariante. Ao solicitar um sinalizador configurado com variantes, seu aplicativo fornece um contexto que é AWS AppConfig avaliado em relação a um conjunto de regras definidas pelo usuário. Dependendo do contexto especificado na solicitação e das regras definidas para a variante, AWS AppConfig retorna valores de sinalizadores diferentes para o aplicativo.
A captura de tela a seguir mostra um exemplo de sinalizador de recurso com três variantes definidas pelo usuário e a variante padrão.