As traduções são geradas por tradução automática. Em caso de conflito entre o conteúdo da tradução e da versão original em inglês, a versão em inglês prevalecerá.
Implantação automatizada - StackSets
nota
Recomendamos implantar com StackSets. No entanto, para implantações em uma única conta ou para fins de teste ou avaliação, considere a opção de implantação de pilhas.
Antes de iniciar a solução, analise a arquitetura, os componentes da solução, a segurança e as considerações de design discutidas neste guia. Siga as step-by-step instruções nesta seção para configurar e implantar a solução em seu AWS Organizations.
Tempo de implantação: aproximadamente 30 minutos por conta, dependendo StackSet dos parâmetros.
Pré-requisitos
O AWS Organizations
Se você já implantou a versão 1.3.x ou anterior dessa solução, deverá desinstalar a solução existente. Para obter mais informações, consulte Atualizar a solução.
Antes de implantar essa solução, revise sua implantação do AWS Security Hub:
-
Deve haver uma conta de administrador delegada do Security Hub em sua organização da AWS.
-
O Security Hub deve ser configurado para agregar descobertas em todas as regiões. Para obter mais informações, consulte Agregando descobertas entre regiões no Guia do usuário do AWS Security Hub.
-
Você deve ativar o Security Hub para sua organização em cada região em que você usa a AWS.
Esse procedimento pressupõe que você tenha várias contas usando o AWS Organizations e tenha delegado uma conta de administrador do AWS Organizations e uma conta de administrador do AWS Security Hub.
Visão geral da implantação
nota
StackSets a implantação dessa solução usa uma combinação de serviços gerenciados e autogerenciados. StackSets O autogerenciado StackSets deve ser usado atualmente, pois eles usam aninhados StackSets, que ainda não são compatíveis com o gerenciamento de serviços. StackSets
Implemente o a StackSets partir de uma conta de administrador delegado em seu AWS Organizations.
Planejamento
Use o formulário a seguir para ajudar na StackSets implantação. Prepare seus dados e, em seguida, copie e cole os valores durante a implantação.
AWS Organizations admin account ID: _______________ Security Hub admin account ID: _______________ CloudTrail Logs Group: ______________________________ Member account IDs (comma-separated list): ___________________, ___________________, ___________________, ___________________, ___________________ AWS Organizations OUs (comma-separated list): ___________________, ___________________, ___________________, ___________________, ___________________
(Opcional) Etapa 0: implantar a pilha de integração de tíquetes
-
Se você pretende usar o recurso de emissão de tíquetes, primeiro implante a pilha de integração de tíquetes em sua conta de administrador do Security Hub.
-
Copie o nome da função Lambda dessa pilha e forneça-o como entrada para a pilha de administração (consulte a Etapa 1).
Etapa 1: iniciar a pilha de administração na conta de administrador delegada do Security Hub
-
Usando um modelo autogerenciado StackSet, execute o CloudFormation modelo
automated-security-response-admin.templateda AWS em sua conta de administrador do AWS Security Hub na mesma região do administrador do Security Hub. Esse modelo usa pilhas aninhadas. -
Escolha quais padrões de segurança instalar. Por padrão, somente SC é selecionado (recomendado).
-
Escolha um grupo de registros existente do Orchestrator para usar. Selecione
YesseSO0111-ASR- Orchestratorjá existe em uma instalação anterior.
Para obter mais informações sobre autogerenciamento StackSets, consulte Conceder permissões autogerenciadas no Guia CloudFormation do usuário da AWS.
Etapa 2: instalar as funções de remediação em cada conta membro do AWS Security Hub
Aguarde até que a Etapa 1 conclua a implantação, pois o modelo na Etapa 2 faz referência às funções do IAM criadas pela Etapa 1.
-
Usando um serviço gerenciado StackSet, execute o CloudFormation modelo da
automated-security-response-member-roles.templateAWS em uma única região em cada conta em seu AWS Organizations. -
Escolha instalar esse modelo automaticamente quando uma nova conta ingressar na organização.
-
Insira o ID da conta de administrador do AWS Security Hub.
Etapa 3: Inicie a pilha de membros em cada conta de membro e região do AWS Security Hub
-
Usando o autogerenciamento StackSets, lance o CloudFormation modelo
automated-security-response-member.templateda AWS em todas as regiões em que você tem recursos da AWS em todas as contas da sua organização da AWS gerenciadas pelo mesmo administrador do Security Hub.nota
Até que o StackSets suporte gerenciado por serviços esteja aninhado, você deve executar essa etapa para todas as novas contas que ingressarem na organização.
-
Escolha quais playbooks do Security Standard instalar.
-
Forneça o nome de um grupo de CloudTrail registros (usado por algumas correções).
-
Insira o ID da conta de administrador do AWS Security Hub.
(Opcional) Etapa 0: iniciar uma pilha de integração do sistema de tickets
-
Se você pretende usar o recurso de emissão de tíquetes, inicie primeiro a respectiva pilha de integração.
-
Escolha as pilhas de integração fornecidas para o Jira ou ServiceNow use-as como um modelo para implementar sua própria integração personalizada.
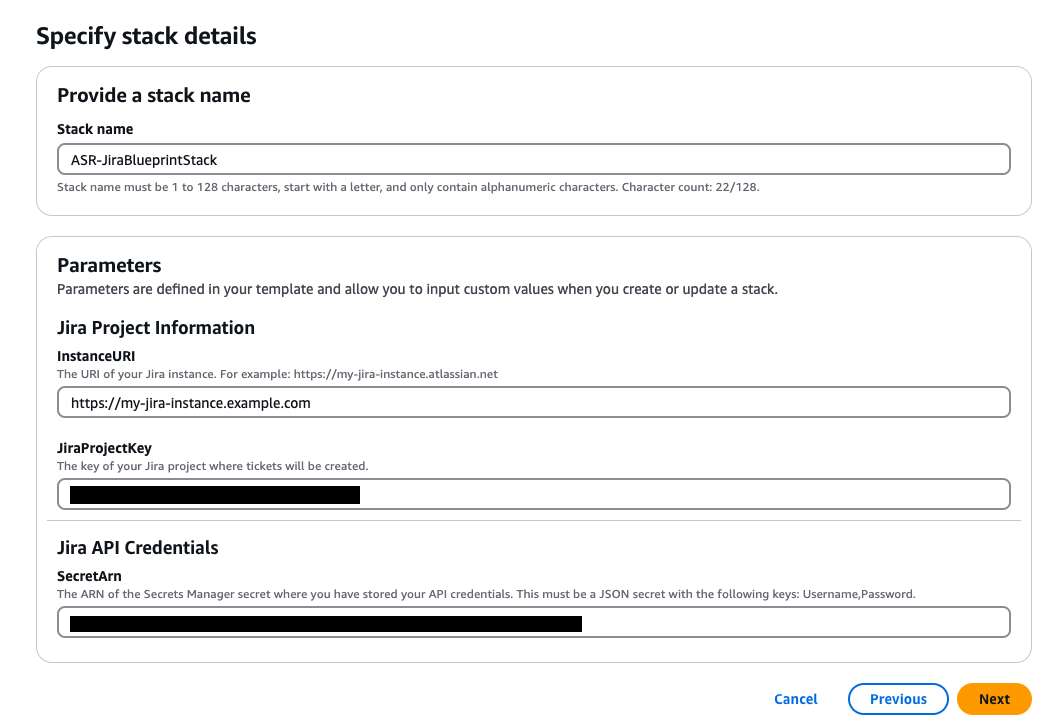
Para implantar a pilha do Jira:
-
Insira um nome para sua pilha.
-
Forneça o URI para sua instância do Jira.
-
Forneça a chave do projeto do Jira para o qual você deseja enviar tickets.
-
Crie um novo segredo de valor-chave no Secrets Manager que contenha seu Jira e.
UsernamePasswordnota
Você pode optar por usar uma chave de API do Jira no lugar de sua senha, fornecendo seu nome de usuário como
Usernamee sua chave de API como o.Password -
Adicione o ARN desse segredo como entrada na pilha.
Forneça um nome de pilha, informações do projeto Jira e credenciais da API Jira.
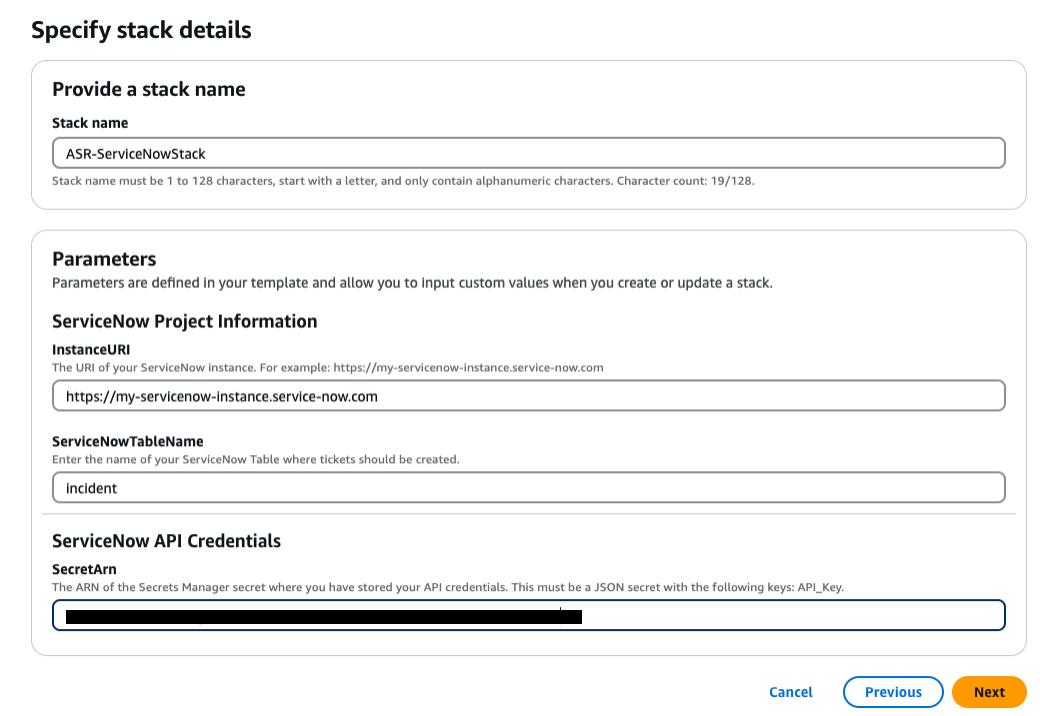
Para implantar a ServiceNow pilha:
-
Insira um nome para sua pilha.
-
Forneça o URI da sua ServiceNow instância.
-
Forneça o nome ServiceNow da sua tabela.
-
Crie uma chave de API ServiceNow com permissão para modificar a tabela na qual você pretende gravar.
-
Crie um segredo no Secrets Manager com a chave
API_Keye forneça o ARN secreto como entrada para a pilha.Forneça o nome da pilha, as informações ServiceNow do projeto e as credenciais ServiceNow da API.
Para criar uma pilha de integração personalizada: inclua uma função Lambda que o orquestrador de soluções Step Functions possa chamar para cada correção. A função Lambda deve receber a entrada fornecida pelo Step Functions, construir uma carga útil de acordo com os requisitos do seu sistema de emissão de tíquetes e fazer uma solicitação ao sistema para criar o ticket.
-
Etapa 1: iniciar a pilha de administração na conta de administrador delegada do Security Hub
-
Inicie a pilha de administração
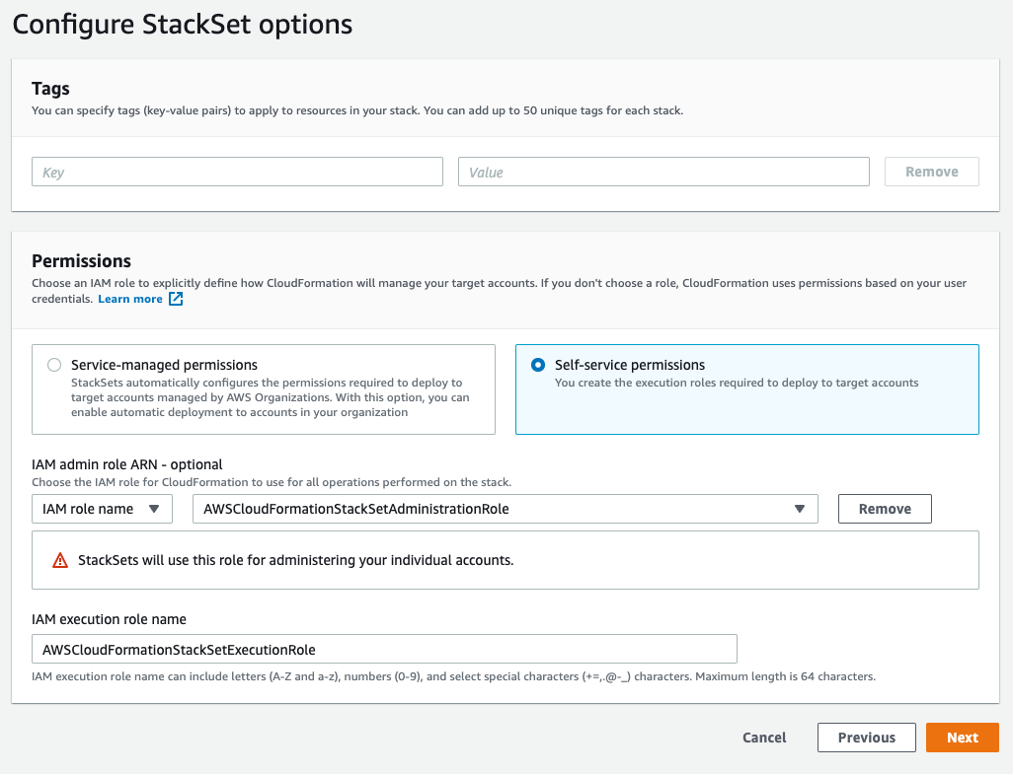
, automated-security-response-admin.template, com sua conta de administrador do Security Hub. Normalmente, um por organização em uma única região. Como essa pilha usa pilhas aninhadas, você deve implantar esse modelo como autogerenciado. StackSetConfigurar StackSet opções
-
Para o parâmetro Números da conta, insira o ID da conta de administrador do AWS Security Hub.
-
Para o parâmetro Especificar regiões, selecione somente a região em que o administrador do Security Hub está ativado. Aguarde a conclusão dessa etapa antes de prosseguir para a Etapa 2.
Etapa 2: instalar as funções de remediação em cada conta membro do AWS Security Hub
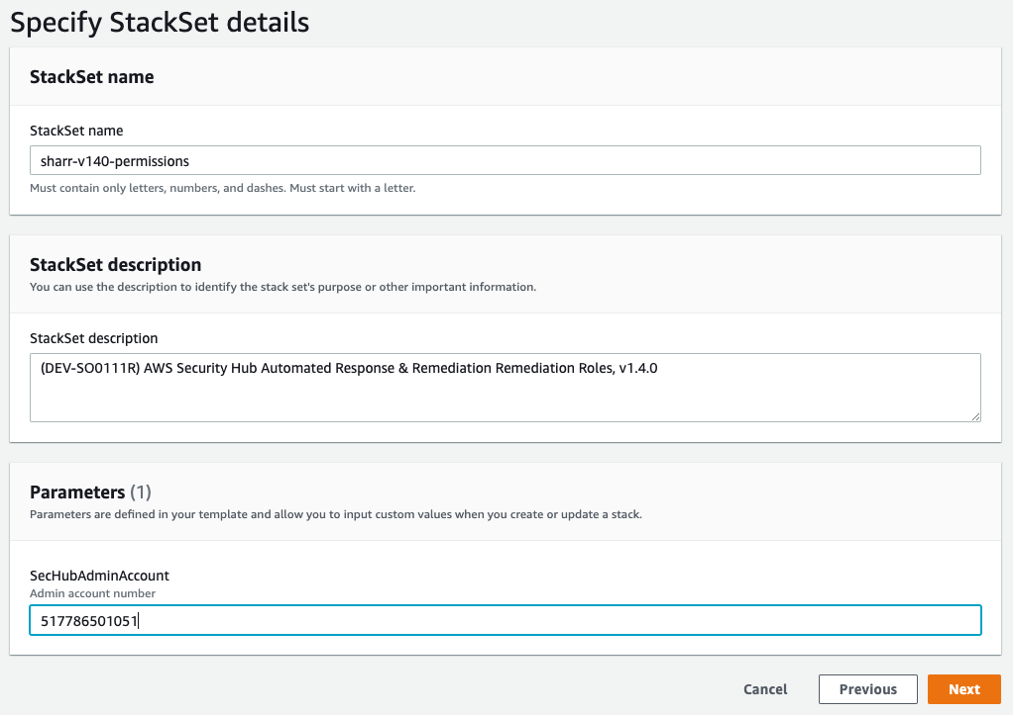
Use um serviço gerenciado StackSets para implantar o modelo de funções de membroautomated-security-response-member-roles.template Isso StackSet deve ser implantado em uma região por conta de membro. Ele define as funções globais que permitem chamadas de API entre contas a partir da função de etapa do ASR Orchestrator.
-
Implante em toda a organização (típica) ou em unidades organizacionais, de acordo com as políticas de sua organização.
-
Ative a implantação automática para que novas contas no AWS Organizations recebam essas permissões.
-
Para o parâmetro Especificar regiões, selecione uma única região. As funções do IAM são globais. Você pode continuar na Etapa 3 enquanto isso é StackSet implantado.
Especifique StackSet detalhes
Etapa 3: Inicie a pilha de membros em cada conta de membro e região do AWS Security Hub
Como a pilha de membros usa pilhas
Parâmetros
LogGroup Configuração: escolha o grupo de registros que recebe CloudTrail os registros. Se não existir nenhum ou se o grupo de registros for diferente para cada conta, escolha um valor conveniente. Os administradores da conta devem atualizar o parâmetro Systems Manager - Parameter Store/Solutions/SO0111/Metrics_ LogGroupName depois de criar um grupo de CloudWatch registros para CloudTrail registros. Isso é necessário para correções que criam alarmes de métricas em chamadas de API.
Padrões: escolha os padrões a serem carregados na conta do membro. Isso só instala os runbooks do AWS Systems Manager — não habilita o Padrão de Segurança.
SecHubAdminAccount: insira o ID da conta de administrador do AWS Security Hub na qual você instalou o modelo de administração da solução.
Contas

Locais de implantação: você pode especificar uma lista de números de contas ou unidades organizacionais.
Especifique regiões: selecione todas as regiões nas quais você deseja corrigir as descobertas. Você pode ajustar as opções de implantação conforme apropriado para o número de contas e regiões. A simultaneidade de regiões pode ser paralela.