External pipeline deployment
In a default Landing Zone Accelerator on AWS installation, the CodePipeline and S3 bucket deploys into the AWS Organizations management account. You may want to deploy and operate these components in a member AWS account to limit access to the management account. This solution supports this model with an optional pipeline deployment account.
External pipeline deployment
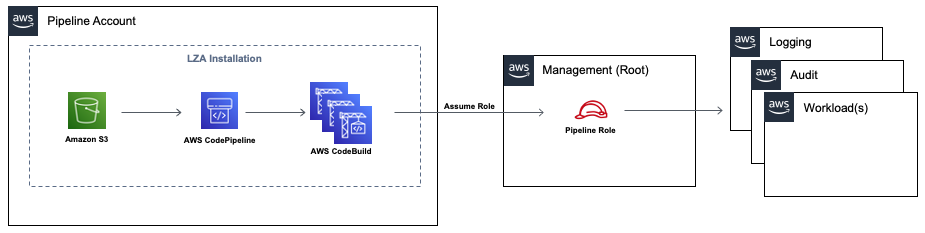
Follow these instructions to implement this pattern:
-
Select an AWS account for the pipeline deployment account. We recommend having the account as a member of the AWS Organizations environment.
-
Create a new IAM role in the AWS Organizations management account that allows access from the pipeline deployment account.
AcceleratorPipelineDeploymentRoleis the preferred name for this role. -
Update the trust policy of the
AcceleratorPipelineDeploymentRoleto allow access from the pipeline deployment account:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "arn:aws:iam::<PIPELINE_DEPLOYMENT_ACCOUNT_ID>:root" }, "Action": "sts:AssumeRole" "Condition": { "StringLike": { "aws:PrincipalArn": "arn:aws:iam::<PIPELINE_DEPLOYMENT_ACCOUNT_ID>:role/<AcceleratorQualifier-*>" } } } ] }
-
Attach the
AdministratorAccessAWS managed IAM policy to the role.
Note
By default, AWS IAM roles with prefix AcceleratorQualifier in the pipeline account are used by AWS CodeBuild to assume role in the management account and deploy resources. To protect these roles, you should implement additional security measures, such as Service control policies (SCPs).
After you create the IAM role in the management account, synthesize the Landing Zone Accelerator on AWS installer template configured for external deployments by following these instructions:
-
Clone or download the latest release of the Landing Zone Accelerator on AWS source code
. -
Navigate to the
sourcefolder:cd landing-zone-accelerator-on-aws/source -
Install dependencies and build the source code:
yarn install && yarn build -
Navigate to the installer folder:
cd packages/\@aws-accelerator/installer/ -
Synthesize the installer template by running:
cdk synth --context use-external-pipeline-account=true -
Retrieve the synthesize template named
AWSAccelerator-InstallerStack.template.jsonfrom thecdk.outdirectory. -
Use this template to create the
AWSAccelerator-InstallerCloudFormation stack in the external deployment account. -
The deployment now follows the same process as the standard deployment process with the addition of the following parameters:
-
AcceleratorQualifier - Names the resources in the external deployment account. This must be unique for each Landing Zone Accelerator on AWS pipeline created in a single external deployment account, for example "env2" or "app1." Do not use "aws-accelerator" or a similar value that could be confused with the prefix.
-
ManagementAccountId - This is the AWS account ID of the AWS Organizations management account.
-
ManagementAccountRoleName - This is the name of the IAM role used to access the management account from the external deployment account.
-