Tutorial: Create a private REST API
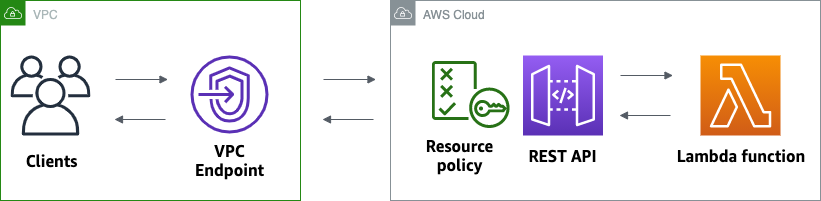
In this tutorial, you create a private REST API. Clients can access the API only from within your Amazon VPC. The API is isolated from the public internet, which is a common security requirement.
This tutorial takes approximately 30 minutes to complete. First, you use an CloudFormation template to create an Amazon VPC, a VPC endpoint, an AWS Lambda function, and launch an Amazon EC2 instance that you'll use to test your API. Next, you use the AWS Management Console to create a private API and attach a resource policy that allows access only from your VPC endpoint. Lastly, you test your API.
To complete this tutorial, you need an AWS account and an AWS Identity and Access Management user with console access. For more information, see Set up to use API Gateway.
In this tutorial, you use the AWS Management Console. For an CloudFormation template that creates this API and all related resources, see template.yaml.
Step 1: Create dependencies
Download and unzip this CloudFormation template. You use the template to create all of the dependencies for your private API, including an Amazon VPC, a VPC endpoint, and a Lambda function that serves as the backend of your API. You create the private API later.
To create an CloudFormation stack
Open the CloudFormation console at https://console.aws.amazon.com/cloudformation
. -
Choose Create stack and then choose With new resources (standard).
-
For Specify template, choose Upload a template file.
-
Select the template that you downloaded.
-
Choose Next.
-
For Stack name, enter
private-api-tutorialand then choose Next. -
For Configure stack options, choose Next.
-
For Capabilities, acknowledge that CloudFormation can create IAM resources in your account.
-
Choose Next, and then choose Submit.
CloudFormation provisions the dependencies for your API, which can take a few minutes. When the status of your CloudFormation stack is CREATE_COMPLETE, choose Outputs. Note your VPC endpoint ID. You need it for later steps in this tutorial.
Step 2: Create a private API
You create a private API to allow only clients within your VPC to access it.
To create a private API
Sign in to the API Gateway console at https://console.aws.amazon.com/apigateway
. -
Choose Create API, and then for REST API, choose Build.
-
For API name, enter
private-api-tutorial. -
For API endpoint type, select Private.
-
For VPC endpoint IDs, enter the VPC endpoint ID from the Outputs of your CloudFormation stack.
-
For IP address type, choose Dualstack.
-
Choose Create API.
Step 3: Create a method and integration
You create a GET method and Lambda integration to handle GET requests to your API.
When a client invokes your API, API Gateway sends the request to the Lambda function that you created in Step 1, and then
returns a response to the client.
To create a method and integration
Sign in to the API Gateway console at https://console.aws.amazon.com/apigateway
. -
Choose your API.
-
Choose Create method.
-
For Method type select
GET. -
For Integration type, select Lambda function.
-
Turn on Lambda proxy integration. With a Lambda proxy integration, API Gateway sends an event to Lambda with a defined structure, and transforms the response from your Lambda function to an HTTP response.
-
For Lambda function, choose the function that you created with the CloudFormation template in Step 1. The function's name begins with
private-api-tutorial. -
Choose Create method.
Step 4: Attach a resource policy
You attach a resource policy to your API that allows clients to invoke your API only through your VPC endpoint. To further restrict access to your API, you can also configure a VPC endpoint policy for your VPC endpoint, but that's not necessary for this tutorial.
To attach a resource policy
Sign in to the API Gateway console at https://console.aws.amazon.com/apigateway
. -
Choose your API.
-
Choose Resource policy, and then choose Create policy.
-
Enter the following policy. Replace
vpceIDwith your VPC endpoint ID from the Outputs of your CloudFormation stack. -
Choose Save changes.
Step 5: Deploy your API
Next, you deploy your API to make it available to clients in your Amazon VPC.
To deploy an API
Sign in to the API Gateway console at https://console.aws.amazon.com/apigateway
. -
Choose your API.
Choose Deploy API.
For Stage, select New stage.
For Stage name, enter
test.(Optional) For Description, enter a description.
Choose Deploy.
Now you're ready to test your API.
Step 6: Verify that your API isn't publicly accessible
Use curl to verify that you can't invoke your API from outside of your Amazon VPC.
To test your API
Sign in to the API Gateway console at https://console.aws.amazon.com/apigateway
. -
Choose your API.
-
In the main navigation pane, choose Stages, and then choose the test stage.
-
Under Stage details, choose the copy icon to copy your API's invoke URL. The URL looks like
https://. The VPC endpoint that you created in Step 1 has private DNS enabled, so you can use the provided URL to invoke your API.abcdef123.execute-api.us-west-2.amazonaws.com/test -
Use curl to attempt to invoke your API from outside of your VPC.
curl https://abcdef123.execute-api.us-west-2.amazonaws.com/testCurl indicates that your API's endpoint can't be resolved. If you get a different response, go back to Step 2, and make sure that you choose Private for your API's endpoint type.
curl: (6) Could not resolve host:abcdef123.execute-api.us-west-2.amazonaws.com/test
Next, you connect to an Amazon EC2 instance in your VPC to invoke your API.
Step 7: Connect to an instance in your VPC and invoke your API
Next, you test your API from within your Amazon VPC. To access your private API, you connect to an Amazon EC2 instance in your VPC and then use curl to invoke your API. You use Systems Manager Session Manager to connect to your instance in the browser.
To test your API
Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/
. -
Choose Instances.
-
Choose the instance named private-api-tutorial that you created with the CloudFormation template in Step 1.
-
Choose Connect and then choose Session Manager.
-
Choose Connect to launch a browser-based session to your instance.
-
In your Session Manager session, use curl to invoke your API. You can invoke your API because you're using an instance in your Amazon VPC.
curl https://abcdef123.execute-api.us-west-2.amazonaws.com/testVerify that you get the response
Hello from Lambda!.
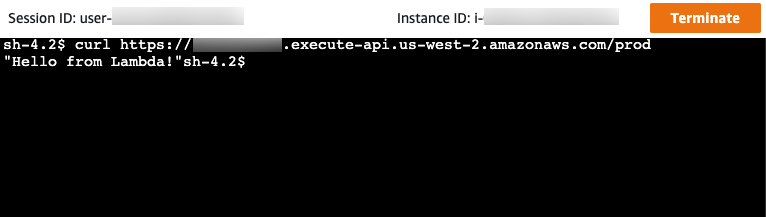
You successfully created an API that's accessible only from within your Amazon VPC and then verified that it works.
Step 8: Clean up
To prevent unnecessary costs, delete the resources that you created as part of this tutorial. The following steps delete your REST API and your CloudFormation stack.
To delete a REST API
Sign in to the API Gateway console at https://console.aws.amazon.com/apigateway
. -
On the APIs page, select an API. Choose API actions, choose Delete API, and then confirm your choice.
To delete an CloudFormation stack
Open the CloudFormation console at https://console.aws.amazon.com/cloudformation
. -
Select your CloudFormation stack.
-
Choose Delete and then confirm your choice.
Next steps: Automate with CloudFormation
You can automate the creation and cleanup of all AWS resources involved in this tutorial. For a full example CloudFormation template, see template.yaml.