Managing AWS WAF web ACLs
Manage the AWS WAF web ACLs for your App Runner service by using one of the following methods:
App Runner console
When you create a service or update an existing one on the App Runner console, you can associate or disassociate an AWS WAF web ACL.
Note
-
An App Runner service can be associated with only one web ACL. However, you can associate one web ACL with more than one App Runner service in addition to other AWS resources.
-
Before you associate a web ACL, make sure to update your IAM permissions for AWS WAF. For more information, see Permissions.
Associating AWS WAF web ACL
Important
Source IP rules for App Runner private services that are associated with WAF web ACLs do not adhere to IP based rules. This is because we currently don't support forwarding request source IP data to App Runner private services associated with WAF. If your App Runner application requires source IP/CIDR incoming traffic control rules, you must use security group rules for private endpoints instead of WAF web ACLs.
To associate an AWS WAF web ACL
-
Open the App Runner console
, and in the Regions list, select your AWS Region. -
Based on whether you're creating or updating a service, perform one of the following steps:
-
If you're creating a new service, choose Create an App Runner service and go to Configure Service.
-
If you're updating an existing service, choose the Configuration tab, and then choose Edit under Configure service.
-
-
Go to Web application firewall under Security.
-
Choose the Activate toggle button to view the options.
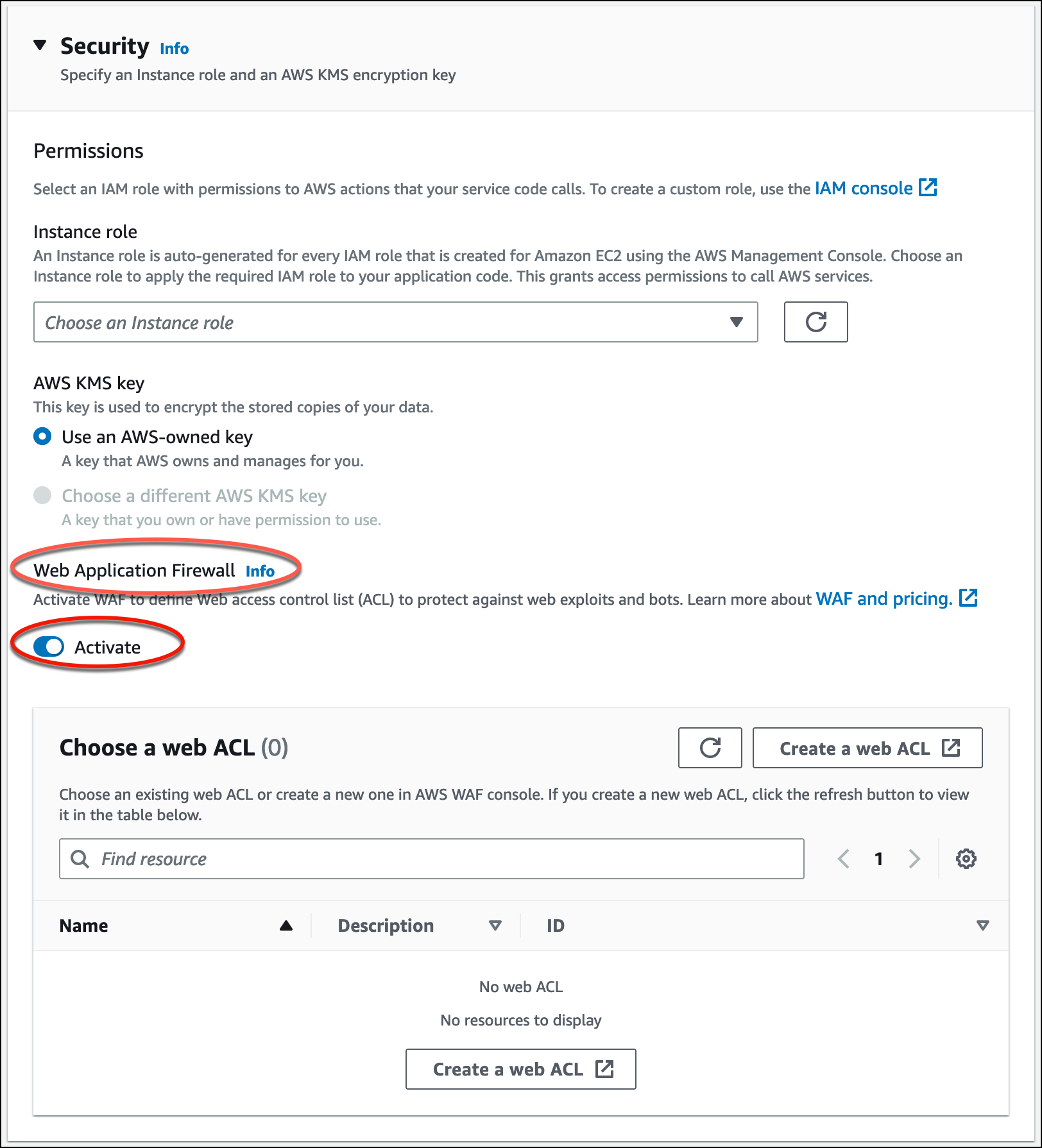
-
Perform one of the following steps:
-
To associate an existing web ACL: Choose the required web ACL from the Choose a web ACL table to associate with your App Runner service.
-
To create a new web ACL: Choose Create web ACL to create a new web ACL using the AWS WAF console. For more information, see Creating a web ACL in the AWS WAF Developer Guide.
-
Choose the refresh button to view the newly created web ACL in the Choose a web ACL table.
-
Select the required web ACL.
-
-
-
Choose Next if you're creating a new service or Save changes if you're updating an existing service. The selected web ACL is associated with your App Runner service.
-
To verify the web ACL association, choose the Configuration tab of your service and go to Configure service. Scroll to Web application firewall under Security to view the details of the web ACL associated with your service.
Note
When you create a web ACL, a small amount of time passes before the web ACL fully propagates and is available to App Runner. The propagation time can be from a few seconds to a number of minutes. AWS WAF returns a
WAFUnavailableEntityExceptionwhen you try to associate a web ACL before it has fully propagated.If you refresh the browser or navigate away from the App Runner console before the web ACL is fully propagated, the association fails to occur. However, you can navigate within the App Runner console.
Disassociating an AWS WAF web ACL
You can disassociate AWS WAF web ACl that you no longer need by updating your App Runner service.
To disassociate an AWS WAF web ACl
-
Open the App Runner console
, and in the Regions list, select your AWS Region. -
Go to Configuration tab of the service you want to update and choose Edit under Configure service.
-
Go to Web application firewall under Security.
-
Disable the Activate toggle button. You receive a message to confirm the deletion.
-
Choose Confirm. The web ACL is disassociated from your App Runner service.
Note
-
If you want to associate your service with another web ACL, select a web ACL from the Choose a web ACL table. App Runner disassociates the current web ACL and starts the process to associate with the selected web ACL.
-
If no other App Runner services or resources use a disassociated web ACL, consider deleting the web ACL. Otherwise, you will continue to incur costs. For more information about pricing, see AWS WAF Pricing
. For instruction on how to delete a web ACL, see DeleteWebACL in the AWS WAF API Reference. -
You can't delete a web ACL that's associated with other active App Runner services or other resources.
-
AWS CLI
You can associate or disassociate an AWS WAF web ACL by using the AWS WAF public APIs. The App Runner service, with which you want to associate or disassociate a web ACL, must be in a valid state.
AWS WAF returns a WAFNonexistentItemException error when you call one of the following AWS WAF APIs for an App Runner service which is in an
invalid state:
-
AssociateWebACL -
DisassociateWebACL -
GetWebACLForResource
The invalid states for your App Runner service include:
-
CREATE_FAILED -
DELETE_FAILED -
DELETED -
OPERATION_IN_PROGRESSNote
OPERATION_IN_PROGRESSstate is invalid only if your App Runner service is being deleted.
For more information about AWS WAF public APIs, see AWS WAF API Reference Guide.
Note
Update your IAM permissions for AWS WAF. For more information, see Permissions.
Associating AWS WAF web ACL using AWS CLI
Important
Source IP rules for App Runner private services that are associated with WAF web ACLs do not adhere to IP based rules. This is because we currently don't support forwarding request source IP data to App Runner private services associated with WAF. If your App Runner application requires source IP/CIDR incoming traffic control rules, you must use security group rules for private endpoints instead of WAF web ACLs.
To associate an AWS WAF web ACL
-
Create an AWS WAF web ACL for your service with your preferred set of rule actions to
AlloworBlockthe web requests to your service. For more information about AWS WAF APIs, see CreateWebACL in the AWS WAF API Reference Guide.Example Create a web ACL - Request
aws wafv2 create-web-acl --region <region> --name <web-acl-name> --scopeREGIONAL--default-actionAllow={}--visibility-config <file-name.json> # This is the file containing the WAF web ACL rules. -
Associate the web ACL that you created with the App Runner service using the
associate-web-aclAWS WAF public API. For more information about AWS WAF APIs, see AssociateWebACL in the AWS WAF API Reference Guide.Note
When you create a web ACL, a small amount of time passes before the web ACL fully propagates and is available to App Runner. The propagation time can be from a few seconds to a number of minutes. AWS WAF returns a
WAFUnavailableEntityExceptionwhen you try to associate a web ACL before it has fully propagated.If you refresh the browser or navigate away from the App Runner console before the web ACL is fully propagated, the association fails to occur. However, you can navigate within the App Runner console.
Example Associating a web ACL - Request
aws wafv2 associate-web-acl --resource-arn <apprunner_service_arn> --web-acl-arn <web_acl_arn> --region <region> -
Verify that the web ACL is associated with your App Runner service using the
get-web-acl-for-resourceAWS WAF public API. For more information about AWS WAF APIs, see GetWebACLForResource in the AWS WAF API Reference Guide.Example Verify web ACL for resource - Request
aws wafv2 get-web-acl-for-resource --resource-arn <apprunner_service_arn> --region <region>If there are no web ACLs associated with your service, you receive a blank response.
Deleting an AWS WAF web ACL using AWS CLI
You can't delete an AWS WAF web ACL if it's associated with an App Runner service.
To delete an AWS WAF web ACL
-
Disassociate the web ACL from your App Runner service by using the
disassociate-web-aclAWS WAF public API. For more information about AWS WAF APIs, see DisassociateWebACL in the AWS WAF API Reference Guide.Example Disassociating a web ACL - Request
aws wafv2 disassociate-web-acl --resource-arn <apprunner_service_arn> --region <region> -
Verify that the web ACL is disassociated from your App Runner service using the
get-web-acl-for-resourceAWS WAF public API.Example Verify that the web ACL is disassociated - Request
aws wafv2 get-web-acl-for-resource --resource-arn <apprunner_service_arn> --region <region>The disassociated web ACL isn't listed for your App Runner service. If there are no web ACLs associated with your service, you receive a blank response.
-
Delete the disassociated web ACL using the
delete-web-aclAWS WAF public API. For more information about AWS WAF APIs, see DeleteWebACL in the AWS WAF API Reference Guide.Example Delete a web ACL - Request
aws wafv2 delete-web-acl --name <web_acl_name> --scopeREGIONAL--id <web_acl_id> --lock-token <web_acl_lock_token> --region <region> -
Verify that the web ACL is deleted using the
list-web-aclAWS WAF public API. For more information about AWS WAF APIs, see ListWebACLs in the AWS WAF API Reference Guide.Example Verify that the web ACL is deleted - Request
aws wafv2 list-web-acls --scopeREGIONAL--region <region>The deleted web ACL is no longer be listed.
Note
If a web ACL is associated with other active App Runner services or other resources, such as Amazon Cognito user pools, the web ACL can't be deleted.
Listing App Runner services that are associated with a web ACL
A web ACL can be associated with multiple App Runner services and other resources. List the App Runner services associated with a web ACL using the
list-resources-for-web-acl AWS WAF public API. For more information about AWS WAF APIs, see ListResourcesForWebACL in the AWS WAF API Reference Guide.
Example List App Runner services associated with a web ACL - Request
aws wafv2 list-resources-for-web-acl --web-acl-arn <WEB_ACL_ARN> --resource-typeAPP_RUNNER_SERVICE--region <REGION>
Example List App Runner services associated with a web ACL - Response
The following example illustrates the response when there are no App Runner services that are associated with a web ACL.
{ "ResourceArns": [] }
Example List App Runner services associated with a web ACL - Response
The following example illustrates the response when there are App Runner services that are associated with a web ACL.
{ "ResourceArns": [ "arn:aws:apprunner:<region>:<aws_account_id>:service/<service_name>/<service_id>" ] }
Testing and logging AWS WAF web ACLs
When you set a rule action to Count in your web ACL, AWS WAF adds the request to a count of requests that match the rule. To test a
web ACL with your App Runner service, set rule actions to Count and consider the volume of requests that match each rule. For example, you
set a rule for the Block action that matches a large number of requests that you determine to be normal user traffic. In that case, you might
need to reconfigure your rule. For more information, see Testing and tuning your AWS WAF protections
in the AWS WAF Developer Guide.
You can also configure AWS WAF to log request headers to an Amazon CloudWatch Logs log group, an Amazon Simple Storage Service (Amazon S3) bucket, or an Amazon Data Firehose. For more information, see Logging web ACL traffic in the AWS WAF Developer Guide.
To access logs related to the web ACL that's associated with your App Runner service, refer to the following log fields:
-
httpSourceName: ContainsAPPRUNNER -
httpSourceId: Containscustomeraccountid-apprunnerserviceid
For more information, see Log Examples in the AWS WAF Developer Guide.
Important
Source IP rules for App Runner private services that are associated with WAF web ACLs do not adhere to IP based rules. This is because we currently don't support forwarding request source IP data to App Runner private services associated with WAF. If your App Runner application requires source IP/CIDR incoming traffic control rules, you must use security group rules for private endpoints instead of WAF web ACLs.